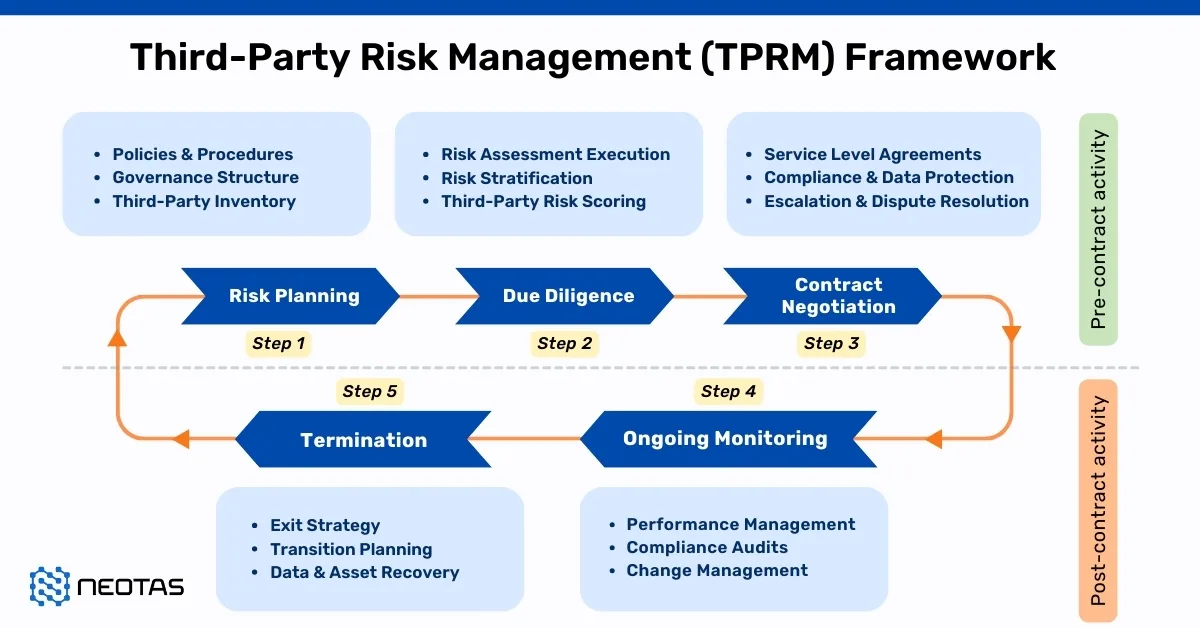
OSINT Framework
A comprehensive guide to OSINT framework, OSINT Tools, OSINT Techniques, and how to use it.
The OSINT Framework is a comprehensive collection of open source intelligence (OSINT) tools and resources that are organised and categorised for easy access. It’s designed to assist researchers, investigators, cybersecurity professionals, journalists, and anyone else interested in gathering information from publicly available sources on the internet. The framework provides a structured approach to OSINT by offering a wide range of tools and techniques to aid in information discovery, analysis, and investigation.
The OSINT framework is a methodology that integrates data, processes, methods, tools and techniques to help the security team identify information about an adversary or their actions quickly and accurately. It serves as a guide for effectively leveraging publicly available information to enhance situational awareness, threat detection, decision-making, and overall security.
The framework provides a systematic approach to harnessing the wealth of information available on the internet for various purposes. By following this structured approach and utilising appropriate tools, individuals and organisations can extract valuable insights from the vast amount of data available on the internet and apply them to their specific objectives.
Key components of the OSINT Framework:
- Structured Methodology: The OSINT Framework offers a systematic and organised approach to conducting open source intelligence activities. It provides a clear roadmap for collecting and processing information.
- Data Collection: The framework emphasises the collection of information from publicly accessible sources, such as social media platforms, websites, forums, news articles, public records, and more.
- Categorisation: Information gathered through OSINT activities is categorised based on its source, relevance, type, and context. This categorisation aids in effective analysis and utilisation.
- Tools and Techniques: The framework includes a wide range of tools, techniques, and resources that individuals can use to gather and analyse data. These tools may include search engines, data scrapers, social media monitoring tools, geolocation services, and more.
- Adversary Profiling: OSINT can be used to profile potential adversaries, threat actors, or entities of interest. This involves collecting information about their online presence, activities, affiliations, and intentions.
- Digital Footprint Analysis: OSINT activities often involve establishing the digital footprint of individuals, organisations, or entities. This includes identifying their online interactions, communications, and patterns of behavior.
- Threat Detection and Prevention: The framework aids in identifying potential threats, vulnerabilities, and risks by monitoring online activities, discussions, and emerging trends.
- Enhancing Situational Awareness: OSINT provides real-time insights into current events, incidents, and trends that may impact an organisation’s security, operations, or reputation.
- Integration with Intelligence Processes: The information gathered through OSINT activities can be integrated with broader intelligence processes, enabling a holistic understanding of security risks and opportunities.
- Ethical Considerations: The OSINT Framework emphasises ethical and responsible information gathering. It encourages practitioners to respect privacy, adhere to legal boundaries, and avoid invasive or harmful actions.
- Continuous Improvement: OSINT is an evolving field, and the framework encourages practitioners to stay updated with the latest tools, techniques, and sources of information. It also promotes a culture of continuous learning and improvement.
- Decision Support: OSINT-derived insights contribute to informed decision-making across various domains, including cybersecurity, business strategy, risk management, and policy formulation.
The OSINT Framework serves as a valuable resource hub for individuals and organisations seeking to leverage open source intelligence to gather information, perform investigations, and make informed decisions. It eliminates the need to search for OSINT tools independently and provides a structured approach to accessing the right tools for specific tasks. However, while using these tools, it’s important to adhere to ethical guidelines, respect privacy, and ensure compliance with applicable laws and regulations.
An OSINT framework can be used to:
- Establish the digital footprint of a known threat
- Gather all availability intelligence about an adversary’s activity, interests, techniques, motivation and habits
- Categorise data by source, tool, method or goal Identify opportunities to enhance the existing security posture through system recommendations
Now let us deep-dive into each of these OSINT framework components and understand how to use it.
Structured Methodology:
The OSINT Framework underpins a structured and methodical approach to open source intelligence operations. It furnishes a well-defined roadmap for the systematic collection and processing of information. This structured methodology is paramount in ensuring that no crucial data is overlooked, and that each piece of information is subjected to rigorous scrutiny. By adhering to a clear framework, practitioners are able to navigate through the vast expanse of publicly accessible sources with precision and purpose.
Data Collection:
Central to the OSINT Framework is the emphasis on comprehensive data collection from an array of publicly accessible sources. This encompasses social media platforms, websites, forums, news articles, public records, and other digital repositories. This breadth of sources ensures a thorough and diverse pool of information for analysis. It is through this meticulous data gathering process that practitioners are equipped to construct a comprehensive view of the subject matter at hand.
Categorisation:
Once data is acquired, the OSINT Framework advocates for its systematic categorization. This entails classification based on the source, relevance, type, and context of the information. Such categorization is pivotal in streamlining subsequent analysis and utilisation. It allows for the efficient retrieval of specific data points, enabling practitioners to extract meaningful insights from the wealth of information gathered.
Tools and Techniques:
The OSINT Framework is enriched by an extensive repertoire of tools, techniques, and resources at the disposal of individuals engaged in intelligence activities. These encompass an array of search engines, data scrapers, social media monitoring tools, geolocation services, and other specialised instruments. These resources serve as force multipliers, augmenting the capabilities of practitioners and facilitating the collection and analysis of data with precision and efficiency.
Adversary Profiling:
A crucial facet of OSINT lies in the ability to profile potential adversaries, threat actors, or entities of interest. This entails a comprehensive exploration of their online presence, activities, affiliations, and underlying intentions. By meticulously piecing together this digital puzzle, practitioners gain invaluable insights into the motivations and objectives of these subjects, forming a foundational element in threat assessment and mitigation strategies.
Digital Footprint Analysis:
Within the realm of OSINT, establishing a digital footprint is a fundamental endeavor. This entails a thorough examination of the online interactions, communications, and behavioral patterns of individuals, organisations, or entities under scrutiny. Through this analysis, practitioners are able to discern valuable patterns and trends, providing a holistic perspective on the subject’s digital presence. This insight is instrumental in constructing a comprehensive narrative and understanding the underlying dynamics at play.
Threat Detection and Prevention:
The OSINT Framework plays a pivotal role in fortifying security postures by facilitating the identification of potential threats, vulnerabilities, and risks. Through vigilant monitoring of online activities, discussions, and emerging trends, practitioners gain the ability to proactively detect and respond to potential security breaches or malicious intent. This pre-emptive approach is indispensable in safeguarding assets, both tangible and intangible.
Enhancing Situational Awareness:
A key advantage of OSINT lies in its capacity to provide real-time insights into current events, incidents, and prevailing trends. This situational awareness empowers organisations to respond promptly and effectively to evolving circumstances that may impact security, operations, or reputation. By staying abreast of the dynamic landscape, decision-makers are equipped to make informed choices in a rapidly changing environment.
Integration with Intelligence Processes:
The information gleaned through OSINT activities seamlessly integrates with broader intelligence processes. This integration affords a comprehensive understanding of security risks and opportunities, enabling a well-informed approach to decision-making. By harmonising OSINT-derived insights with other intelligence sources, organisations cultivate a comprehensive and multifaceted perspective on the landscape in which they operate.
Ethical Considerations:
A cornerstone of the OSINT Framework is the unwavering commitment to ethical and responsible information gathering. Practitioners are strongly urged to uphold principles of privacy, observe legal boundaries, and refrain from engaging in invasive or harmful actions. This ethical foundation ensures that the pursuit of information remains within the bounds of lawful and morally upright conduct.
Continuous Improvement:
Recognising the dynamic nature of the field, the OSINT Framework encourages practitioners to remain abreast of the latest tools, techniques, and information sources. This ethos of continuous learning and improvement ensures that practitioners are equipped with the most effective resources to navigate the evolving landscape of open source intelligence.
Decision Support:
OSINT-derived insights serve as a linchpin in informed decision-making across a spectrum of domains, including cybersecurity, business strategy, risk management, and policy formulation. By leveraging the wealth of information garnered through OSINT activities, organisations empower themselves to make decisions grounded in a thorough understanding of the prevailing environment.
The OSINT Framework, with its structured approach, ethical guidelines, and wealth of resources, stands as an invaluable tool for those seeking to harness the power of open source intelligence in their endeavors. It provides a comprehensive blueprint for navigating the digital landscape with precision and purpose. In its judicious application, the OSINT Framework equips organisations and individuals alike with the knowledge and insights necessary for informed and effective decision-making.
How to use the OSINT framework?
Establishing the Digital Footprint of a Known Threat:
One of the primary applications of an OSINT framework lies in its ability to discern and analyse the digital footprint of a known threat. By systematically scouring online platforms, forums, and digital repositories, practitioners can compile a comprehensive dossier of the threat’s online activities, interactions, and patterns. This detailed analysis serves as a crucial foundation for threat assessment, allowing for the development of targeted and effective countermeasures.
Gathering Comprehensive Intelligence about an Adversary:
In the realm of intelligence gathering, the OSINT framework excels in providing a holistic view of adversaries. It delves deep into their activities, interests, techniques, motivations, and habitual patterns. Through rigorous data collection and analysis, practitioners construct a comprehensive profile, affording invaluable insights into the strategic landscape. This knowledge forms the basis for strategic planning, enabling organisations to anticipate and respond to adversarial actions effectively.
Categorisation for Precision Analysis:
The OSINT framework places significant emphasis on the meticulous categorisation of acquired data. Each piece of information is classified based on its source, relevance, type, and contextual significance. This systematic categorisation streamlines the subsequent analysis process, allowing for the swift retrieval of specific data points. This approach ensures that practitioners can distill meaningful insights from the extensive pool of information amassed.
Identifying Opportunities for Security Enhancement:
Another critical facet of the OSINT framework lies in its ability to identify opportunities for bolstering existing security postures. By scrutinising online activities, discussions, and emerging trends, practitioners can pinpoint potential vulnerabilities and risks. This proactive approach empowers organisations to fortify their defenses and implement preemptive measures, thereby safeguarding assets and interests.
As practitioners engage with the OSINT framework, it is imperative to approach each task with the utmost ethical consideration. Respecting privacy, adhering to legal boundaries, and refraining from any actions that could be perceived as invasive or harmful is paramount. This ethical foundation not only upholds professional standards but also ensures that the pursuit of information remains within the bounds of lawful and morally upright conduct.
In the ever-evolving landscape of open source intelligence, the OSINT framework serves as a beacon of guidance. Its structured methodology, ethical underpinnings, and rich array of tools and techniques equip practitioners with the means to navigate this dynamic terrain effectively. By incorporating the principles and practices outlined in the framework, individuals and organisations alike empower themselves to make informed, strategic decisions based on a solid foundation of intelligence and insights.
Continuous Learning and Adaptation:
In the dynamic field of open source intelligence, continuous learning and adaptation are imperative. The OSINT framework underscores the need for practitioners to stay abreast of the latest tools, techniques, and information sources. This commitment to ongoing education ensures that individuals remain equipped with the most effective resources to navigate the evolving landscape of open source intelligence. By embracing a culture of continuous improvement, practitioners enhance their proficiency and effectiveness in intelligence-gathering endeavors.
Integration into Decision-Making Processes:
The insights derived from OSINT activities play a pivotal role in shaping informed decision-making across various domains. Whether in the realms of cybersecurity, business strategy, risk management, or policy formulation, the wealth of information garnered through OSINT activities provides a valuable foundation. This intelligence empowers decision-makers to make choices grounded in a thorough understanding of the prevailing environment. By integrating OSINT-derived insights into their decision-making processes, organisations optimise their strategic approaches and enhance their overall effectiveness.
The OSINT Framework stands as an invaluable resource for individuals and organisations seeking to harness the power of open source intelligence. It eliminates the need for independent searches for OSINT tools and provides a structured approach to accessing the right tools for specific tasks. However, it is crucial to bear in mind that while utilising these tools, practitioners must uphold ethical guidelines, respect privacy, and ensure compliance with applicable laws and regulations. This commitment to responsible information gathering not only upholds professional standards but also safeguards the integrity of the intelligence-gathering process.
Collaborative Intelligence Gathering:
One of the key strengths of the OSINT framework lies in its capacity to facilitate collaborative intelligence gathering efforts. By leveraging a diverse array of sources and tools, practitioners can work together to compile a comprehensive understanding of a given subject or situation. This collaborative approach fosters a synergistic exchange of insights and expertise, resulting in a more holistic and accurate intelligence assessment.
Multi-Disciplinary Approach:
The OSINT framework embraces a multi-disciplinary approach, recognising that intelligence-gathering efforts often require expertise spanning various domains. It encourages practitioners to draw on a range of skills and knowledge areas, including but not limited to information technology, social sciences, cybersecurity, and geopolitics. This broad spectrum of expertise ensures that intelligence assessments are comprehensive and well-rounded, taking into account various facets of a given subject.
Safeguarding Reputations:
In addition to security concerns, the OSINT framework also plays a crucial role in safeguarding reputations. By monitoring online discussions, mentions, and sentiments, practitioners can proactively address potential reputation risks. This proactive approach allows organisations to mitigate negative publicity or misinformation, preserving their brand image and credibility in the digital sphere.
Societal Impact Assessment:
The OSINT framework extends its reach beyond individual organisations and threats, encompassing assessments of broader societal impacts. Practitioners can use OSINT to analyse trends, sentiments, and emerging issues within the public domain. This societal insight can inform policy decisions, crisis management strategies, and public relations efforts, ensuring that organisations are attuned to the pulse of the wider community.
Influence Mapping:
OSINT can be leveraged for influence mapping, a strategic process that involves identifying key individuals, organisations, or entities that wield significant influence within a given context. By analysing their online presence, affiliations, and activities, practitioners can gain valuable insights into the power dynamics at play. This information can be pivotal in devising effective communication and engagement strategies.
Predictive Analytics and Trend Forecasting:
By analysing patterns and trends derived from open source information, the OSINT framework can facilitate predictive analytics and trend forecasting. This forward-looking approach enables organisations to anticipate potential developments and adapt their strategies accordingly. It empowers decision-makers with the foresight needed to stay ahead of emerging challenges or opportunities.
The OSINT Framework offers a comprehensive and structured approach to open source intelligence activities. It encompasses methodologies for data collection, categorisation, and analysis, supported by a diverse array of tools and techniques. Additionally, it emphasises ethical considerations, continuous learning, and the integration of intelligence into decision-making processes. By adhering to the principles outlined in the OSINT Framework, practitioners equip themselves with the knowledge and skills to navigate the complex landscape of open source intelligence effectively and responsibly.
FAQs regarding the OSINT framework
1. What is OSINT?
- OSINT stands for Open Source Intelligence. It refers to the practice of collecting and analysing information from publicly available sources to gather intelligence and insights. These sources can include websites, social media, news articles, public records, and more.
2. What is the OSINT framework?
- The OSINT framework is a structured methodology that provides a systematic approach to conducting open source intelligence activities. It includes guidelines for data collection, categorisation, analysis, and ethical considerations.
3. How does the OSINT framework differ from other intelligence-gathering methods?
- The OSINT framework focuses specifically on gathering information from publicly available sources, whereas other intelligence-gathering methods may involve classified or confidential sources. OSINT is particularly useful for gathering information in a non-intrusive and legally compliant manner.
4. What are the key components of the OSINT framework?
- The key components of the OSINT framework include structured methodology, data collection, categorisation, tools and techniques, adversary profiling, digital footprint analysis, threat detection and prevention, enhancing situational awareness, integration with intelligence processes, ethical considerations, continuous improvement, and decision support.
5. How can the OSINT framework be used in practice?
- The OSINT framework can be applied in various scenarios, such as threat assessment, competitive intelligence, due diligence, reputation management, and policy formulation. It provides a structured approach to gather relevant information for informed decision-making.
6. Is the use of OSINT legal and ethical?
- Yes, when conducted responsibly and within legal boundaries, OSINT is a legal and ethical practice. It emphasises respecting privacy, adhering to legal regulations, and avoiding invasive or harmful actions.
7. Can the OSINT framework be used for individual research or business purposes?
- Yes, the OSINT framework is applicable for both individual researchers and businesses. It provides a structured approach for gathering information relevant to specific objectives, whether it be for personal research, competitive analysis, or security assessments.
8. How can the OSINT framework be integrated into existing intelligence processes?
- The information gathered through OSINT activities can be integrated with other forms of intelligence, such as human intelligence (HUMINT) or signals intelligence (SIGINT). This holistic approach provides a comprehensive understanding of security risks and opportunities.
9. Are there specific tools and resources recommended within the OSINT framework?
- The OSINT framework includes a wide range of tools and techniques, which may include search engines, data scrapers, social media monitoring tools, geolocation services, and more. The choice of tools depends on the specific requirements of the intelligence-gathering task.
10. How can practitioners stay updated with the latest developments in OSINT?
- Practitioners are encouraged to engage in continuous learning and improvement within the field of OSINT. This involves staying informed about the latest tools, techniques, and information sources through professional development, training, and participation in relevant communities and forums.
Reduce & Manage Business Risk with OSINT.
Neotas is an Enhanced Due Diligence Platform that leverages AI to join the dots between Corporate Records, Adverse Media and Open Source Intelligence (OSINT).
Schedule a Call or Book a Demo of Neotas Enhanced Due Diligence Platform.
Read More about Open Source Intelligence:
- OSINT Tools, OSINT Techniques, and how to use OSINT framework.
- Open Source Intelligence (OSINT) in the Fight Against Financial Crime
- Reduce & Manage Business Risk with Neotas Open Source Intelligence (OSINT) Solutions
- Using OSINT for Sources of Wealth Checks
- Open Source Intelligence (OSINT) based AML Solution sees beneath the surface
- Enhancing ESG Risk Management Framework with Neotas’ OSINT Integration
- How Open Source Intelligence (OSINT) is transforming enhanced due diligence and investigations in AML compliance
- Detecting Modern Slavery In Your Supply Chain using Open-source Intelligence
- Creating an effective framework for managing risk with suppliers and third parties using open-source intelligence (OSINT)
- Using Open Source Intelligence For Enhanced Due Diligence



 New Whitepaper and Checklist
New Whitepaper and Checklist