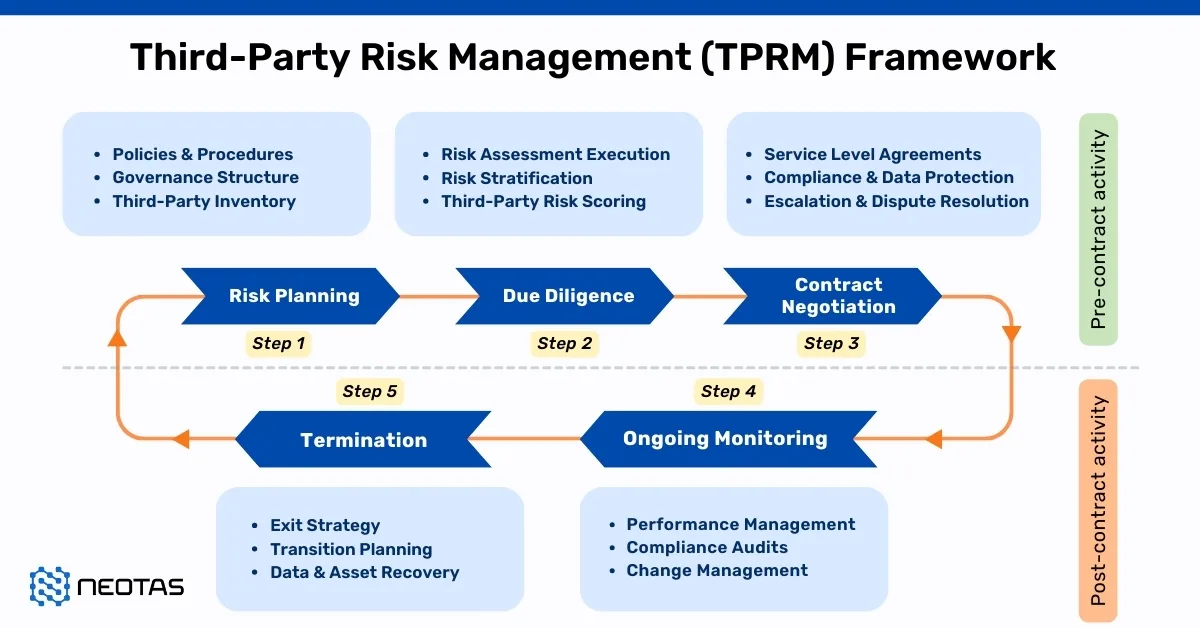
Third-Party Risk Management (TPRM) Lifecycle
In today’s interconnected business environment, organisations increasingly rely on third-party vendors, suppliers, and service providers to support their operations, drive efficiencies, and deliver specialised expertise. However, while outsourcing and partnerships can foster growth and competitive advantage, they also introduce significant risks. Data breaches, regulatory non-compliance, operational disruptions, and reputational damage are just some of the potential consequences if these third-party relationships are not managed effectively.
A structured, robust Third-Party Risk Management (TPRM) Lifecycle provides organisations with a systematic approach to assess, monitor, and mitigate risks arising from these partnerships. Below, we break down each stage in the TPRM lifecycle, providing clear insights into best practices, strategies, and common challenges associated with third-party risk management.
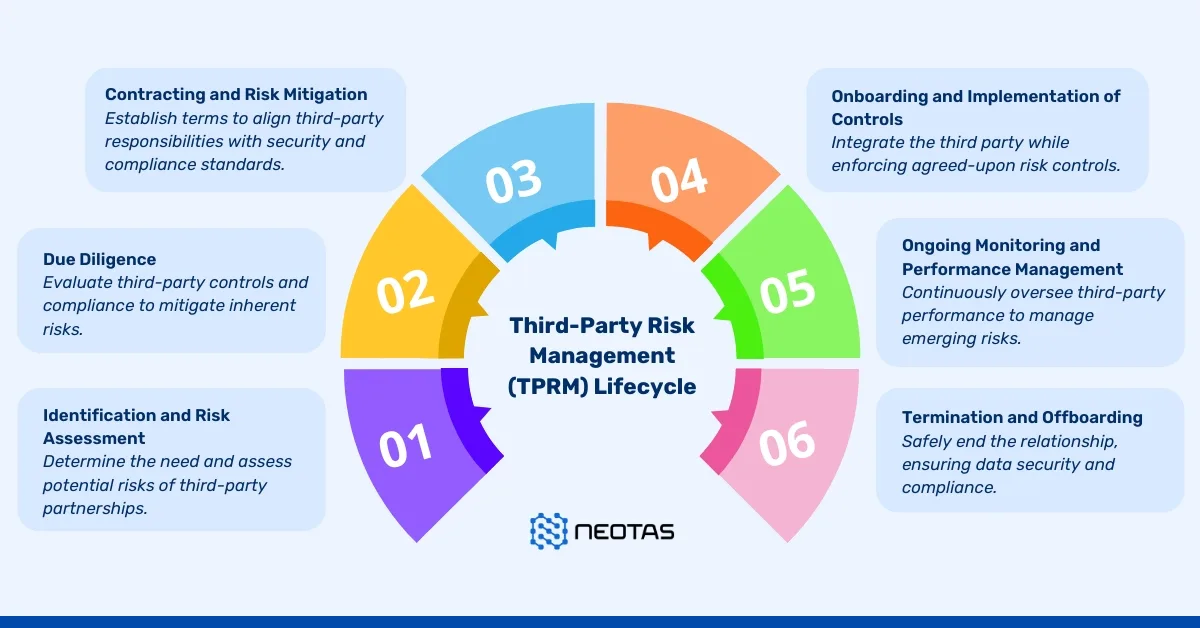
1. Identification and Risk Assessment
Determining the Need and Assessing Potential Risks of Third-Party Partnerships
The initial step in the TPRM lifecycle is to clearly identify the third-party relationships the organisation intends to establish. Here, the focus is on understanding the business need for each vendor and assessing the potential risks these relationships could bring. This assessment is essential, as it helps prioritise third parties based on their risk level and criticality to the organisation’s operations.
Key Activities:
- Identify Business Objectives: Define why the partnership is needed. Are you seeking cost reduction, access to technology, or specialised expertise? Understanding the objectives provides context for potential risks.
- Categorise Based on Risk: Determine the criticality of each vendor by assessing the type of data they will handle, their access to your systems, and the impact on business continuity if they fail to meet expectations. This is often supported by frameworks or risk-tiering models.
- Evaluate Preliminary Risk Exposure: Conduct an initial risk analysis to capture inherent risks. Here, inherent risks are the natural risks present in the relationship due to the nature of the vendor’s services and the data they handle.
Organisations that conduct a thorough risk assessment at this stage can effectively allocate resources, dedicating more attention to higher-risk vendors and streamlining efforts with lower-risk partners.
2. Due Diligence
Evaluating Third-Party Controls and Compliance to Mitigate Inherent Risks
Due diligence is the stage where organisations delve deeper into assessing the third party’s risk profile. This process helps verify the vendor’s ability to meet your security, regulatory, and operational requirements. Conducting rigorous due diligence is critical, as it forms the basis for understanding the third party’s strengths and potential vulnerabilities.
Key Activities:
- Risk Assessment Questionnaires: Use tailored questionnaires to assess the vendor’s security controls, compliance posture, data management practices, and financial stability. The questions should align with industry standards and regulatory requirements.
- Review of Certifications and Compliance: Verify the vendor’s certifications, such as ISO 27001, SOC 2, or GDPR compliance. Ensuring they meet necessary regulatory and industry standards helps establish a baseline for their risk controls.
- Assess Cybersecurity and Data Privacy Measures: Evaluate the third party’s cybersecurity infrastructure and data privacy practices, especially if they will handle sensitive information. This may involve assessing encryption, network security, incident response capabilities, and privacy policies.
A well-executed due diligence process provides an in-depth understanding of the third party’s risk controls and allows for informed decision-making regarding risk acceptance or additional mitigation measures.
3. Contracting and Risk Mitigation
Setting Terms to Align Third-Party Responsibilities with Security and Compliance Standards
The contracting phase is where the organisation formally establishes the terms and conditions governing the third-party relationship. Contracts should explicitly outline performance expectations, compliance requirements, and security obligations. This stage is crucial, as well-structured contracts can enforce risk mitigation strategies and serve as a reference point should issues arise.
Key Activities:
- Define Performance and Compliance Requirements: Establish Service Level Agreements (SLAs) that specify performance metrics, response times, and uptime requirements. Outline compliance expectations, including adherence to relevant regulations.
- Include Security and Data Protection Clauses: Specify security requirements, such as data encryption, access control, and incident reporting. Additionally, include data protection clauses to safeguard personal or sensitive information.
- Establish Audit Rights and Termination Clauses: Ensure the organisation retains the right to conduct audits on the vendor’s practices, especially if they handle sensitive data. Termination clauses should also be included to allow for the immediate discontinuation of services if there is a breach or non-compliance.
By embedding security and compliance measures into the contract, organisations create a foundation for enforcing their risk management standards throughout the partnership.
4. Onboarding and Implementation of Controls
Integrating the Third Party While Enforcing Agreed-Upon Risk Controls
Onboarding is the phase where the third party is fully integrated into the organisation’s ecosystem. During this phase, all agreed-upon controls are implemented, and training may be provided to align the third party with the organisation’s security and compliance standards.
Key Activities:
- Implement Access Controls and Security Measures: Configure access controls to limit the vendor’s access strictly to what is necessary for their service delivery. Set up monitoring systems to detect any unusual activity.
- Provide Training on Security Policies: Share the organisation’s security and data protection policies with the third party. This may include training on incident reporting, data handling, and compliance requirements.
- Conduct Initial Security Reviews: Perform an initial review of the third party’s access and security controls. This check ensures that controls are in place and functioning as intended before full integration.
A well-planned onboarding phase reduces the likelihood of security gaps and ensures the third party’s compliance with your organisation’s standards from the outset.
5. Ongoing Monitoring and Performance Management
Continuously Overseeing Third-Party Performance to Manage Emerging Risks
Once the third party is onboarded, ongoing monitoring becomes essential to ensure continued compliance and performance. Regular monitoring allows organisations to detect and address potential issues promptly, maintaining the integrity of the third-party relationship over time.
Key Activities:
- Track SLAs and Compliance Metrics: Continuously monitor the vendor’s performance against agreed SLAs and compliance standards. Regularly assess their adherence to security controls.
- Conduct Regular Risk Assessments and Audits: Periodic audits help identify any emerging risks or changes in the vendor’s risk profile. This is particularly important if the vendor’s operations or your organisation’s regulatory environment change.
- Monitor for Incidents and Non-Compliance: Implement systems to detect security incidents or compliance violations promptly. Have a process in place to address and remediate any issues swiftly.
Ongoing monitoring ensures that risks remain managed throughout the vendor lifecycle and provides early warning signs for potential breaches or compliance failures.
6. Termination and Offboarding
Safely Ending the Relationship, Ensuring Data Security and Compliance
When a third-party relationship concludes, whether due to contract expiration or performance issues, it is essential to manage the termination process carefully. Offboarding should be conducted in a way that secures all organisational data, revokes access, and ensures compliance with regulatory standards.
Key Activities:
- Revoke Access and Retrieve or Destroy Data: Ensure that the vendor’s access to systems, networks, and data is terminated. Retrieve or verify the secure destruction of any data they held.
- Conduct Final Assessments: Perform a final assessment to review any remaining compliance obligations and evaluate the overall performance of the vendor during the relationship.
- Document Lessons Learned: Analyse the engagement to identify any challenges, successes, or insights that could inform future third-party relationships and improve TPRM processes.
A structured offboarding process minimises residual risk and ensures that all aspects of the third-party relationship are appropriately closed.
Effective Third-Party Risk Management is a cornerstone of sound organisational governance. The TPRM lifecycle not only safeguards your organisation’s data and reputation but also fosters strong, compliant partnerships that support business objectives.
By approaching each stage with diligence and structured processes, organisations can better manage risks, ensure regulatory compliance, and maximise the value of their third-party relationships. The investment in TPRM ultimately creates a secure and resilient foundation for growth in an increasingly complex business landscape.
Adopting a Maturity Model for Third-Party Risk Management (TPRM)
A maturity model in Third-Party Risk Management (TPRM) provides a structured approach for organisations to assess their current TPRM capabilities and progressively enhance them. The model allows organisations to evolve from foundational compliance to a robust, proactive, and resilience-focused approach, better preparing them to manage and mitigate third-party risks effectively over time.
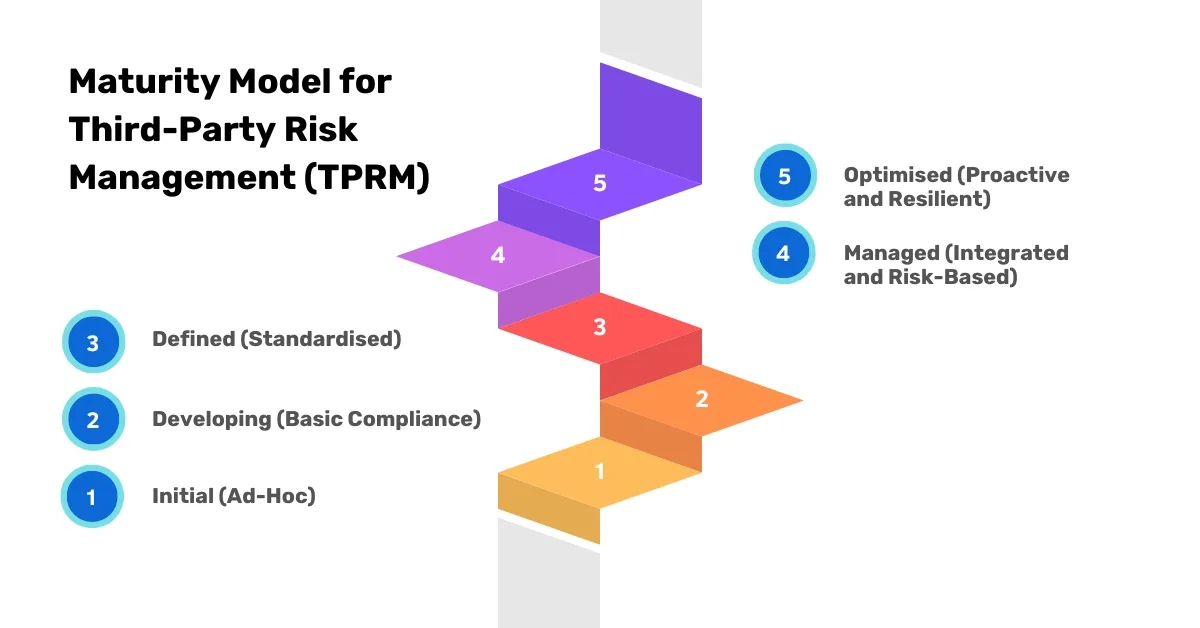
Maturity Levels in TPRM
Third-Party Risk Management (TPRM) is a critical aspect of modern business operations, ensuring that organizations can effectively manage the risks associated with their third-party vendors and partners. As these risks evolve, so too must the approaches to mitigating them. The maturity model for TPRM provides a structured framework to help organizations assess their current practices and progress towards more sophisticated, proactive, and resilient risk management. From ad-hoc and reactive processes to fully optimized, data-driven strategies, each stage in the TPRM maturity model offers valuable insights into how organizations can enhance their risk management capabilities over time.
| Maturity Level | Characteristics | Common Practices | Challenges/Benefits |
| Initial (Ad-Hoc) | Informal, inconsistent, and reactive TPRM practices. Often triggered by issues as they arise. | Minimal due diligence, no standardized process for onboarding or monitoring, reliance on manual assessments. | High likelihood of overlooked risks, fragmented documentation, insufficient visibility into third-party risk. |
| Developing (Basic Compliance) | Basic TPRM processes established, driven by compliance rather than risk-based strategy. | Basic due diligence procedures, some standardization in vendor onboarding, initial attempts at periodic monitoring. | Limited scalability, minimal use of automation, gaps in lower-risk vendor oversight. |
| Defined (Standardised) | TPRM processes formalized with standard processes for due diligence, contracting, onboarding, and monitoring. | Risk-based assessments, documented controls, established governance, use of technology for record-keeping and some automation. | Increased consistency, more structured risk prioritization, better alignment with industry standards. |
| Managed (Integrated and Risk-Based) | Fully integrated TPRM processes, data-driven and risk-based approach, actively monitoring third-party risk. | Continuous monitoring of critical third parties, detailed SLAs, ongoing risk assessments, increased automation. | Improved third-party visibility, stronger incident response, enhanced collaboration with other functions. |
| Optimised (Proactive and Resilient) | Highly proactive TPRM, focusing on resilience, agility, and continuous improvement. | Advanced analytics, predictive risk assessments, robust feedback loops, continuous improvement mindset. | Strong vendor resilience, real-time monitoring, adaptability to emerging risks, alignment with strategic goals. |
By understanding and navigating the different stages of the TPRM maturity model, organizations can better align their third-party risk management practices with their strategic objectives, ensuring stronger vendor relationships, improved compliance, and a more resilient business environment. Whether you’re just starting out or refining your existing processes, identifying your current maturity level and setting goals for the next stage will help you mitigate risks and stay ahead of potential challenges. With a proactive and integrated TPRM strategy, businesses can confidently manage third-party risks and drive long-term success.
Measuring TPRM Effectiveness Through Metrics, Feedback Loops, and Internal Audits
To gauge the maturity and effectiveness of TPRM, organisations should establish measurable goals and utilise performance metrics, feedback systems, and audits. These tools provide insights into current performance, identify areas for improvement, and ensure that TPRM processes evolve to meet changing business and regulatory needs.
Key Metrics for Measuring TPRM Effectiveness
- Risk Identification and Assessment Metrics: Track the number of third parties evaluated, assessment completion times, and risk tier distribution. High completion rates and accurate tiering indicate efficiency and focus on critical risks.
- Compliance Metrics: Measure adherence to regulatory requirements, number of non-compliance incidents, and remediation timeframes. These metrics highlight how well the TPRM process meets regulatory expectations.
- Incident Response Metrics: Monitor the time taken to detect, respond to, and resolve security incidents involving third parties. Faster response times and lower incident rates signal an effective risk management program.
- Vendor Performance Metrics: Assess third parties’ performance against SLAs, response times, and adherence to contract terms. Performance against KPIs shows whether vendors meet expectations and helps identify potentially risky relationships.
- Audit Metrics: Track the frequency and outcomes of internal and external audits, non-compliance issues discovered, and resolved audit findings. A lower number of significant findings over time can indicate improved TPRM maturity.
Establishing Feedback Loops
Feedback loops create a cycle of continuous improvement in TPRM processes, ensuring the program stays relevant, efficient, and responsive to changing risks.
- Vendor Feedback: Encourage third parties to provide feedback on the TPRM process, especially after onboarding and audits. Insights from vendors can reveal friction points and potential process improvements.
- Internal Stakeholder Feedback: Collect feedback from internal departments involved in TPRM, such as procurement, IT, and compliance teams. This input can identify gaps or inefficiencies in risk assessments, communication, or onboarding.
- Post-Incident Reviews: Following an incident or breach involving a third party, conduct a formal review to determine root causes and assess the adequacy of risk controls. Document lessons learned and update processes accordingly.
- Regular Performance Reviews: Conduct quarterly or bi-annual reviews to evaluate the effectiveness of third-party risk controls and track progress on key metrics. Use these reviews to adjust risk strategies, revise SLAs, or modify monitoring protocols as needed.
Conducting Internal Audits
Regular internal audits are essential for maintaining TPRM effectiveness and alignment with regulatory standards.
- Audit Scope and Frequency: Define audit scopes based on risk levels, with high-risk vendors audited more frequently and in greater depth. Audits may include document reviews, on-site assessments, and random sampling.
- Audit Methodologies: Adopt a structured audit methodology (e.g., ISO 19011 for auditing management systems) to ensure thoroughness and consistency. The methodology should address all key components of TPRM, such as onboarding, due diligence, ongoing monitoring, and offboarding.
- Audit Findings and Remediation: Track audit findings and remediation efforts, assigning accountability for resolving issues. Audits should feed into a continuous improvement process, where findings inform updates to TPRM policies, controls, or tools.
Suggesting Periodic TPRM Policy Reviews to Align with Evolving Risks, Regulatory Changes, and Industry Best Practices
Regular policy reviews are vital for ensuring that TPRM practices remain aligned with evolving risks, regulatory shifts, and industry standards. Policy reviews should be conducted at least annually or in response to significant events, such as regulatory updates or major vendor-related incidents.
Key Components of TPRM Policy Reviews
- Risk Landscape Assessment: Assess the current risk landscape, including emerging threats, new regulatory requirements, and business changes that may impact third-party risk. Update TPRM policies to address new risk sources, such as supply chain vulnerabilities or cloud dependencies.
- Regulatory and Compliance Updates: Monitor changes in data privacy laws (e.g., GDPR, CCPA), industry standards, and specific sector regulations (e.g., HIPAA for healthcare). Policies should be updated to reflect new compliance requirements and mitigate risks associated with non-compliance.
- Benchmarking Against Industry Standards: Regularly benchmark TPRM policies and procedures against industry best practices. Organisations can use frameworks such as ISO 27001, NIST guidelines, or sector-specific standards to ensure their TPRM aligns with broader risk management standards.
- Technology and Process Innovations: Evaluate emerging tools, technologies, and methodologies that could enhance TPRM. For example, automated risk monitoring, AI-driven vendor scoring, or blockchain-based traceability can strengthen risk controls and improve efficiency.
- Documenting Changes and Communicating Updates: Document any policy updates, including rationale and expected benefits, and ensure all stakeholders are informed. Communication of policy changes is crucial to maintain adherence across departments and with third parties.
Adopting a TPRM maturity model, measuring effectiveness through key metrics and feedback loops, and conducting regular policy reviews are foundational practices that support continuous improvement. By progressing from a reactive, compliance-driven approach to a proactive, resilience-focused model, organisations can create a robust TPRM framework. Such a framework not only addresses present risks but is agile enough to adapt to emerging threats, regulatory changes, and evolving business needs, positioning the organisation for long-term resilience and strategic advantage.
Read more about Third-Party Risk, TPRM software, and TPRM processes.
TPRM Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Open Source Intelligence (OSINT)
- Introducing the Neotas Enhanced Due Diligence Platform
TPRM Case Studies:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation



 New Whitepaper and Checklist
New Whitepaper and Checklist