Risk-Based Approach (RBA) to AML & KYC risk management
Implementing a Risk-Based Approach in AML and KYC: Strategies for Effective Risk Management.
This article presents an in-depth exploration of the Risk-Based Approach (RBA) as a critical tool for compliance teams in the fight against money laundering and terrorist financing. It explains how RBA necessitates a thorough understanding of the risks inherent within an organisation and the development of tailored controls to address these risks. The focus is on prioritising efforts based on the severity and likelihood of risks, thereby optimising resource allocation and enhancing the effectiveness of compliance measures. The article offers a detailed guide on how to implement RBA, including risk assessment methodologies, policy formulation, and staff training, ultimately providing a roadmap for compliance teams to strategically focus their efforts where they are most needed and impactful.
The Risk-Based Approach (RBA) is a strategic framework focused on proactively identifying and managing the potential risks of money laundering and terrorist financing that a business may encounter.
It involves a systematic assessment of these risks, aligning them with robust and effective control measures. Rather than merely reacting to incidents of money laundering through post-event analysis, RBA emphasises preemptive risk management, guiding financial institutions to actively anticipate and mitigate risks.
Risk-Based Approach (RBA) requires an organisation to thoroughly understand its exposure to money laundering and terrorist financing risks, and to develop tailored control mechanisms. These controls are designed and prioritised based on the severity and likelihood of the risks identified. Commonly employed by compliance teams, this approach directs resources and efforts proportionally to the level of risk, ensuring that higher risks receive more attention and resources.
Risk-Based Approach (RBA) dictates that countries, regulatory authorities, and financial entities must not only identify and assess the risks of money laundering and terrorist financing they face but also understand these risks comprehensively. Following this understanding, they are required to implement appropriate and proportionate mitigation measures. These measures should correspond directly to the intensity of the identified risks, ensuring a balanced and effective approach to managing potential threats in the financial sector.
Risk-Based Approach (RBA) to Anti-Money Laundering
The Risk-Based Approach (RBA) in the context of Anti-Money Laundering (AML) is a methodological framework that prioritises and allocates resources to areas deemed as higher risks. This approach is dynamic and adaptable, allowing for a more focused and efficient use of resources in combating money laundering and terrorist financing. It contrasts with a ‘one-size-fits-all’ strategy, instead advocating for measures that are proportionate to the nature, size, and risk exposure of the entity.
In the RBA, financial institutions and obliged entities assess the likelihood and potential impact of money laundering risks specific to their operations. Based on this assessment, they design and implement controls and mitigation strategies that are commensurate with the identified risks. This process involves a continuous cycle of risk identification, assessment, mitigation, and monitoring.
Importance and Benefits of RBA in Risk Management
- Enhanced Effectiveness: By focusing on higher-risk areas, RBA ensures that efforts and resources are directed where they are most needed, enhancing the effectiveness of AML programs.
- Cost-Efficiency: RBA avoids the wasteful allocation of resources to low-risk areas, allowing for more efficient use of funds and personnel.
- Regulatory Compliance: Many regulatory bodies globally have adopted the RBA, making it not just a best practice but a compliance requirement. It aligns with international standards set by bodies like the Financial Action Task Force (FATF).
- Flexibility and Adaptability: RBA allows organisations to quickly adapt to emerging threats or changes in the risk landscape, unlike more rigid, traditional models.
- Informed Decision-Making: RBA fosters a deeper understanding of the specific risks faced by an entity, leading to more informed and effective decision-making in AML strategies.
Transition from Traditional to Risk-Based Models
The shift from traditional, prescriptive AML models to a Risk-Based Approach represents a significant paradigm change in financial crime risk management. Traditional models often revolved around strict adherence to predefined rules and thresholds, regardless of the specific risk context of an entity. This often led to a ‘tick-box’ culture, where compliance was more about meeting set criteria rather than effectively managing risks.
The transition to RBA requires a cultural and operational shift:
- Risk Assessment: Entities must conduct comprehensive risk assessments to understand their unique risk exposures.
- Policies and Procedures: Development of policies and procedures that are tailored to the risk profile, rather than generic.
- Training and Awareness: Staff need training not just in compliance procedures but in understanding and identifying risks.
- Technology and Data Analysis: Leveraging technology for better risk analysis and management.
- Continuous Monitoring and Review: A shift towards ongoing monitoring of risk profiles and effectiveness of controls, rather than periodic compliance checks.
This transition, while challenging, positions organisations to more effectively combat money laundering and terrorist financing, and to respond with agility to the evolving risk landscape.
The Risk-Based Approach (RBA) Framework
Fundamental Concepts and Categories of Risk
The RBA framework in anti-money laundering (AML) and counter-terrorist financing (CTF) is centred around the identification, assessment, mitigation, and ongoing monitoring of risks. This framework requires a nuanced understanding of various categories of risk, which can broadly be classified as:
- Customer Risks: These risks arise from the diverse nature of customers. Factors such as the customer’s background, occupation, business activities, and the transparency of their source of funds or wealth contribute to the risk profile. High-risk customers might include politically exposed persons (PEPs), those from countries with inadequate AML controls, or individuals involved in industries prone to money laundering.
- Product and Service Risks: Different financial products and services carry varying levels of risk. Products that offer higher anonymity, cross-border transactions, complex structures, or those that inherently have higher cash flows are considered riskier. Examples include private banking, correspondent banking, and certain types of electronic payment services.
- Geographical Risks: These are associated with the countries or regions in which the entity operates, as well as those with which its customers have connections. Countries with high levels of corruption, weak AML regulations, known tax havens, or those under international sanctions are typically deemed higher risk.
Transactional Risks: These relate to the nature and patterns of transactions conducted by customers. Unusual transaction patterns, transactions that do not align with a customer’s profile, high-volume or high-value transactions, and transactions involving high-risk countries are potential risk indicators.
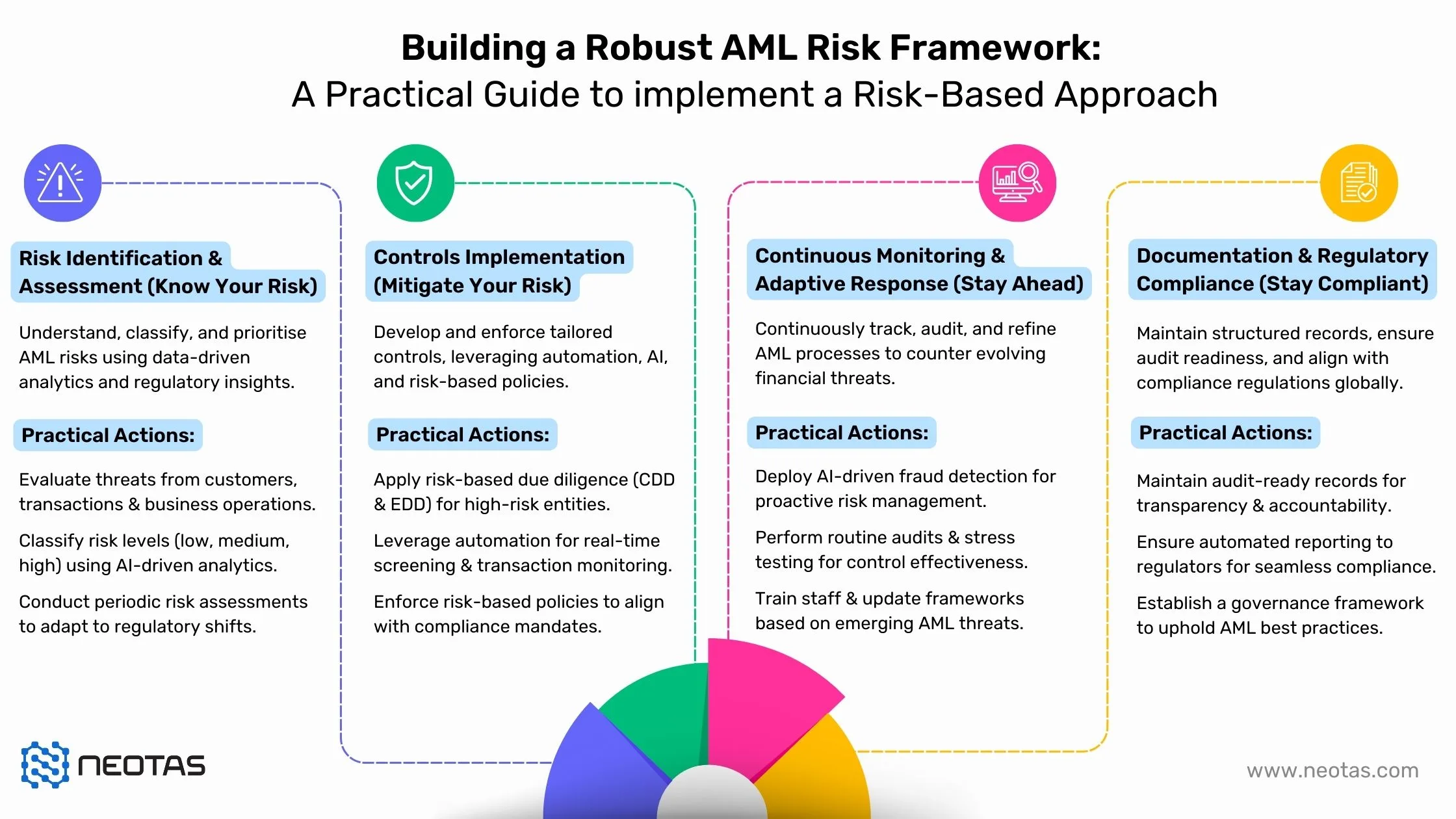
The RBA Process: Identification, Assessment, Mitigation, Monitoring
A Risk-Based Approach (RBA) is central to effective Anti-Money Laundering (AML) compliance, ensuring that resources are allocated where they are most needed. Unlike rigid, rule-based frameworks, an RBA prioritises threats dynamically, enabling financial institutions to detect, assess, and mitigate risks efficiently.
This structured process allows organisations to:




By adopting an RBA, institutions strengthen their compliance posture, enhance fraud detection, and build resilience against regulatory scrutiny.
1. Risk Identification: Establishing the Threat Landscape
The first step in the RBA process is to identify potential risks associated with customers, transactions, products, services, and jurisdictions. This involves:




Why It Matters: Identifying risks at an early stage allows institutions to preemptively apply controls where they are most needed
2. Risk Assessment: Quantifying & Prioritising Risks
Once risks are identified, they must be evaluated based on likelihood and impact to ensure effective prioritisation. Key steps include:



Why It Matters: A well-structured risk assessment model ensures that AML resources are allocated proportionately, preventing unnecessary scrutiny on low-risk entities while enhancing oversight of high-risk areas.
3. Risk Mitigation: Implementing Proportionate Controls
Once risks are assessed, financial institutions must implement tailored controls to reduce exposure while maintaining operational efficiency.




Why It Matters: Effective risk mitigation strategies ensure that AML frameworks remain agile, cost-efficient, and fully compliant with regulatory expectations.
4. Continuous Monitoring & Adaptive Response
AML risks evolve over time, requiring continuous oversight and system adjustments. Institutions must establish ongoing risk management practices such as:




Why It Matters: By continuously adapting to emerging financial crime trends, institutions can stay ahead of regulatory requirements while safeguarding their operations.
The Competitive Advantage of a Robust RBA
A well-implemented Risk-Based Approach delivers tangible benefits, including:




By adopting a structured RBA process, financial institutions not only strengthen their compliance posture but also enhance operational agility, improve risk governance, and foster trust with regulators, clients, and stakeholders.
Practical Implementation: Essential Tools & Technologies
1. Technology in RBA: AI, Machine Learning, and Automation



2. Risk Assessment & Compliance Tools



Institutions that leverage technology-driven risk assessment tools streamline compliance, reduce false positives, and enhance risk detection capabilities.
What is a risk-based approach?
A risk-based approach (RBA) is a method that prioritises risks, focusing on the most significant threats to allocate resources effectively and enhance decision-making processes in various domains like AML, KYC, and compliance. Here is detailed guide to What is a Risk-Based Approach and the Key Components of a Risk-Based Approach.
What are risk-based approach methods?
Risk-based approach methods involve identifying, assessing, prioritising, and managing risks. These methods help organisations tailor their strategies to address specific risks effectively.
What is under a risk-based approach?
Under a risk-based approach, organisations evaluate potential risks in their operations, such as financial, legal, and reputational risks, and implement controls proportionate to the level of risk.
What are the phases of a risk-based approach?
The phases include risk identification, risk assessment, risk prioritisation, risk mitigation, and continuous monitoring and review.
What are the 4 pillars of a risk-based approach?
The four pillars include risk identification, risk assessment, risk control measures, and continuous monitoring and review.
What are the core requirements of a risk-based approach?
Core requirements include comprehensive risk assessment, tailored control measures, continuous monitoring, and effective communication and reporting mechanisms.
How do you adopt a risk-based approach?
Adopting a risk-based approach involves conducting a thorough risk assessment, implementing risk-based controls, regularly reviewing and updating the risk profile, and ensuring staff are trained and aware of the approach.
What are the 5 risk management approaches?
The five approaches include risk avoidance, risk reduction, risk sharing, risk retention, and risk exploitation.
What are the three approaches to risk management?
The three main approaches are risk avoidance, risk transfer, and risk mitigation.
What is the opposite of a risk-based approach?
The opposite is a prescriptive or rules-based approach, which applies uniform controls without considering the specific level of risk.
What is the difference between risk management and a risk-based approach?
Risk management involves identifying and addressing risks, while a risk-based approach prioritises risks to focus efforts and resources on the most critical areas.
What are the two basic approaches to risk management?
The two basic approaches are the traditional risk management approach, focusing on avoiding losses, and the enterprise risk management approach, which also considers strategic risks.
What is the risk-based approach to prioritisation?
This approach involves ranking risks based on their severity and likelihood to ensure that the most critical risks are addressed first.
What are the key elements of a risk management approach?
Key elements include risk identification, risk analysis, risk evaluation, risk treatment, and continuous monitoring.
What is the 4-step approach to risk management?
The four steps are identifying risks, assessing risks, controlling risks, and monitoring and reviewing the control measures.
What are the three phases of a risk-based audit approach?
The three phases include planning (risk identification and assessment), execution (testing controls), and reporting (communicating findings and recommendations).
What is the main objective of using the risk-based approach?
The main objective is to efficiently allocate resources to the areas of highest risk to enhance the effectiveness of risk management practices.
What is the nature of a risk-based approach?
The nature of an RBA is proactive and dynamic, focusing on identifying and mitigating risks before they materialise, based on their likelihood and impact.
What is the difference between a rule-based approach and a risk-based approach?
A rule-based approach applies uniform standards regardless of risk, while a risk-based approach tailors controls to the level of risk.
What are the key benefits of adopting a risk-based approach?
Key benefits include improved resource allocation, enhanced decision-making, increased compliance, and better risk mitigation.
What is an example of a risk management approach?
An example is a company performing regular cybersecurity assessments to identify vulnerabilities and implementing targeted security measures to mitigate identified risks.
What is an example of good risk management?
Good risk management could be a financial institution conducting thorough customer due diligence to prevent money laundering.
What are the 7 types of risk management?
The seven types include financial, operational, reputational, compliance, strategic, environmental, and health and safety risk management.
What is the ideal approach for managing risk?
The ideal approach is context-specific, combining various risk management strategies to address the unique risk profile of an organisation effectively.
What is an example of risk avoidance?
Risk avoidance might involve a company deciding not to enter a high-risk market to prevent potential losses.
When should a risk be avoided?
A risk should be avoided when its potential impact is unacceptable to the organisation or when mitigation costs outweigh the benefits.
About Neotas Due Diligence
Neotas Platform covers 600Bn+ archived web pages, 1.8Bn+ court records, 198M+ corporate records, global social media platforms, and 40,000+ Media sources from over 100 countries to help you build a comprehensive picture of the team. It’s a world-first, searching beyond Google. Neotas’ diligence uncovers illicit activities, reducing financial and reputational risk.
Due Diligence Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Open Source Intelligence (OSINT)
- Customer Due Diligence Requirements
- Risk-Based Approach (RBA) to AML & KYC risk management
- Anti-Money Laundering (AML) Compliance and Checks
- Introducing the Neotas Enhanced Due Diligence Platform
Risk-Based Approach and AML Case Studies:
- Case Study: OSINT for EDD & AML Compliance
- Overcoming EDD Challenges on High Risk Customers
- Neotas Open Source Intelligence (OSINT) based AML Solution sees beneath the surface
- ESG Risks Uncovered In Investigation For Global Private Equity Firm
- Management Due Diligence Reveals Abusive CEO
- Ongoing Monitoring Protects Credit Against Subsidiary Threat
- AML Compliance and Fraud Detection – How to Spot a Money Launderer and Prevent It
- What is Customer Due Diligence in Banking and Financial Services?


 Strengthen regulatory compliance.
Strengthen regulatory compliance.