Third-Party Risk Management (TPRM)
Third-party risk management is a fundamental aspect of modern business operations, aimed at identifying and mitigating risks associated with engaging third-party vendors, suppliers, contractors, and partners. As businesses increasingly rely on external entities to support various functions, TPRM plays a pivotal role in safeguarding against potential threats and vulnerabilities that could impact organisational resilience and reputation.
What is third-party risk management?
TPRM encompasses a systematic approach to assessing, monitoring, and managing risks arising from third-party relationships. It involves conducting due diligence on third-party vendors to understand their capabilities, security measures, and adherence to regulatory requirements. By proactively addressing risks, organisations can mitigate the likelihood and severity of disruptions that may arise from third-party engagements.
The scope of TPRM extends beyond traditional buyer-seller relationships and encompasses a wide range of risks that could impact financial, legal, and operational aspects of an organisation. From cybersecurity challenges to disruptions in critical supply items, TPRM addresses multi-dimensional risks that may arise from third-party engagements.
In today’s complex business environment, third-party risks emerge in diverse forms, encompassing financial fragility, cybersecurity susceptibilities, geopolitical dynamics, and beyond. Third-Party Risk Management (TPRM) involves a comprehensive analysis of the risks arising from relationships with third-party providers. By conducting due diligence on the risks posed by third parties, organisations can foresight to plan and mitigate these risks, averting potential escalation.
At its core, TPRM empowers organisations to take a proactive stance in managing third-party risks, rather than reacting to incidents as they occur.
By conducting thorough risk assessments, establishing robust contractual agreements, and implementing ongoing monitoring mechanisms, organisations can enhance their resilience and protect against potential disruptions.
TPRM is a critical component of effective risk management, allowing organisations to navigate the complexities of third-party relationships while safeguarding against potential threats. By adopting a comprehensive TPRM approach, organisations can enhance their ability to anticipate, assess, and mitigate risks, thereby fostering resilience and ensuring sustainable business operations in an increasingly interconnected world.
Why is third-party risk management important?
The reliance on third-party vendors and partners for outsourcing offers numerous benefits such as cost savings and access to specialised expertise, but it also introduces significant risks that can impact an organisation’s operations, reputation, and bottom line. Therefore, implementing a robust Third-Party Risk Management (TPRM) program is essential to mitigate these risks effectively.
1. Protection of Reputation and Customer Trust:
- External Outages Affecting Areas Across the Supply Chain: Third-party disruptions can ripple through the entire supply chain, affecting upstream and downstream partners, suppliers, and customers.
- Reputation is a valuable asset that can take years to build and seconds to destroy. Third-party incidents, such as service outages or data breaches, can tarnish an organisation’s reputation and erode customer trust. In an era where social media amplifies the impact of negative events, organisations must prioritise reputation management by implementing robust TPRM practices. By safeguarding against third-party risks, businesses can maintain customer confidence and preserve their brand integrity.
- For instance, if a key supplier experiences production delays or supply chain interruptions due to unforeseen circumstances, it can lead to shortages, delays in product delivery, and increased costs for all parties involved.
In today’s interconnected business landscape, safeguarding reputation and nurturing customer trust are paramount imperatives for organisations. Third-party disruptions, such as service outages or data breaches, can tarnish an organisation’s reputation and erode customer trust.
2. Regulatory Compliance Requirements:
- Regulatory bodies worldwide are increasingly focused on third-party risk management as part of broader compliance frameworks: Failure to adequately manage third-party risks can result in compliance and regulatory violations, exposing organisations to legal penalties, fines, and reputational damage.
- Regulatory bodies increasingly hold organisations accountable for the actions of their third-party vendors, necessitating robust oversight and governance to ensure compliance with applicable laws and regulations.
- Organisations operating in regulated industries must adhere to stringent data protection, privacy, and security regulations, often requiring them to assess and mitigate risks associated with third-party relationships. Failure to comply with regulatory requirements can result in severe penalties, legal consequences, and reputational damage, highlighting the importance of robust TPRM programs.
3. Increasing Vulnerability to Disruptive Events:
- Internal Outages and Lapses in Operational Capabilities: Dependence on third-party vendors for critical services or resources can lead to internal outages and operational disruptions if these vendors experience downtime or fail to deliver as expected. Disruptive events, ranging from natural disasters to cyberattacks, can have far-reaching consequences on business operations and supply chains. The interconnected nature of modern business ecosystems means that disruptions affecting third-party vendors can quickly cascade downstream, impacting multiple organisations. Without proper risk management measures in place, businesses are vulnerable to internal and external outages, leading to lapses in operational capabilities and supply chain vulnerabilities.
- For example, if a cloud service provider experiences a service outage, it can result in disruptions to internal systems and applications hosted on their platform, impacting employee productivity and business continuity.
4. Heightened Cybersecurity Risks:
- Vendor Outages That Might Expose Organisation to Supply Chain Vulnerabilities: Changes in third-party operations, such as modifications to data gathering, storage, or security practices, can impact an organisation’s data management and security posture.
- Cybersecurity incidents, including data breaches and ransomware attacks, pose significant threats to organisations of all sizes and industries. Third-party vendors often have access to sensitive data and systems, making them attractive targets for cybercriminals. A breach or security incident involving a third party can expose an organisation to financial losses, regulatory penalties, and reputational damage. Therefore, robust TPRM practices are crucial for assessing and mitigating cybersecurity risks associated with third-party relationships.
- For example, if a cloud storage provider changes its data encryption protocols or data residency requirements without prior notification, it may lead to compliance issues and data security concerns for organisations relying on their services.
5. Operational Resilience Challenges:
- External Outages Affecting Areas Across the Supply Chain: Dependence on a single or limited number of vendors for critical goods or services can expose organisations to supply chain vulnerabilities.
- Disruptions caused by third-party failures or outages can disrupt critical business processes, leading to productivity losses and customer dissatisfaction. Whether it’s a cloud service provider experiencing downtime or a logistics partner facing logistical challenges, organisations must proactively manage third-party risks to ensure uninterrupted operations and customer satisfaction.
- In the event of a vendor outage or disruption, organisations may struggle to find alternative suppliers quickly, leading to supply chain bottlenecks, delays, and potential revenue losses.
Prioritising TPRM is not just a best practice; it is a strategic imperative for modern businesses aiming to thrive amidst evolving threats and challenges.
KPMG International’s new research — which surveyed 1,263 senior TPRM professionals across six sectors and 16 countries, territories and jurisdictions worldwide — reveals that TPRM is a strategic priority for 85 percent of businesses, up from 77 percent before the outbreak of the pandemic.
What’s the Difference Between a Third-Party and a Fourth-Party?
Understanding the distinction between third-party and fourth-party relationships is essential for effective supply chain management and risk mitigation strategies. By recognising the interconnectedness of these relationships and the potential ripple effects of disruptions, organisations can enhance their resilience and ensure business continuity across the supply chain.
| Aspect | Third-Party | Fourth-Party |
|---|---|---|
| Definition | Engages directly with the organisation. | Indirectly connected to the organisation via third parties. |
| Examples | Suppliers, vendors, partners, contractors, etc. | Subcontractors, sub-suppliers, distributors, etc. |
| Contractual Agreement | Typically has contractual agreements. | May not have formal contracts with the organisation. |
| Visibility and Control | Often greater visibility and control due to contractual obligations. | Requires deeper supply chain insights and collaboration for management. |
| Risk Exposure | Directly managed by the organisation. | Poses indirect risks that necessitate proactive monitoring and management. |
Key Differences:
- Direct vs. Indirect Relationship: Third parties engage directly with your organisation, whereas fourth parties are indirectly connected through your third-party relationships.
- Contractual vs. Non-Contractual: Third-party relationships typically involve contractual agreements, while fourth-party relationships may not have formal contracts with your organisation.
- Visibility and Control: Your organisation may have greater visibility and control over third-party activities due to contractual obligations, whereas managing fourth-party risks may require deeper supply chain insights and collaboration with your primary third-party vendors.
- Risk Exposure: While third-party risks are directly managed by your organisation, fourth-party risks may pose indirect risks that require proactive monitoring and management to safeguard against potential disruptions or vulnerabilities in the supply chain.
Types of Third-Party Risks
When collaborating with third-party vendors, organisations are exposed to various types of risks that can impact their operations, reputation, and overall success. Here are the common types of risks introduced by third parties:
| Type of Risk | Description |
|---|---|
| Cybersecurity Risk | The risk of exposure or loss resulting from a cyberattack, security breach, or other security incidents initiated by a third party. It involves potential data breaches, theft, or manipulation of sensitive information. |
| Operational Risk | The risk of a third-party causing disruption to the business operations. This could include service interruptions, delays in delivery, or failure to meet contractual obligations, affecting the organisation’s productivity and performance. |
| Legal, Regulatory, and Compliance Risk | The risk of a third party impacting an organisation’s compliance with local legislation, regulations, or agreements. This is particularly crucial for industries with stringent regulatory requirements, such as financial services, healthcare, and government sectors. |
| Reputational Risk | The risk of negative public opinion or damage to an organisation’s reputation due to the actions or failures of a third party. This could result from data breaches, ethical violations, or subpar service quality, eroding stakeholder trust and brand credibility. |
| Financial Risk | The risk that a third party’s actions or performance will have adverse financial implications for the organisation. This could involve financial losses, increased costs, or missed revenue opportunities due to issues with vendors’ financial stability or performance. |
| Strategic Risk | The risk that a third-party vendor fails to align with the organisation’s strategic objectives, hindering its ability to achieve business goals or pursue growth opportunities. This could involve mismatches in capabilities, culture, or long-term vision, impacting organisational success. |
Understanding and managing these risks is essential for organisations to protect their interests, ensure regulatory compliance, and maintain trust with stakeholders. Implementing robust third-party risk management practices, including due diligence, monitoring, and contingency planning, can help mitigate these risks and enhance organisational resilience in an increasingly interconnected business environment.
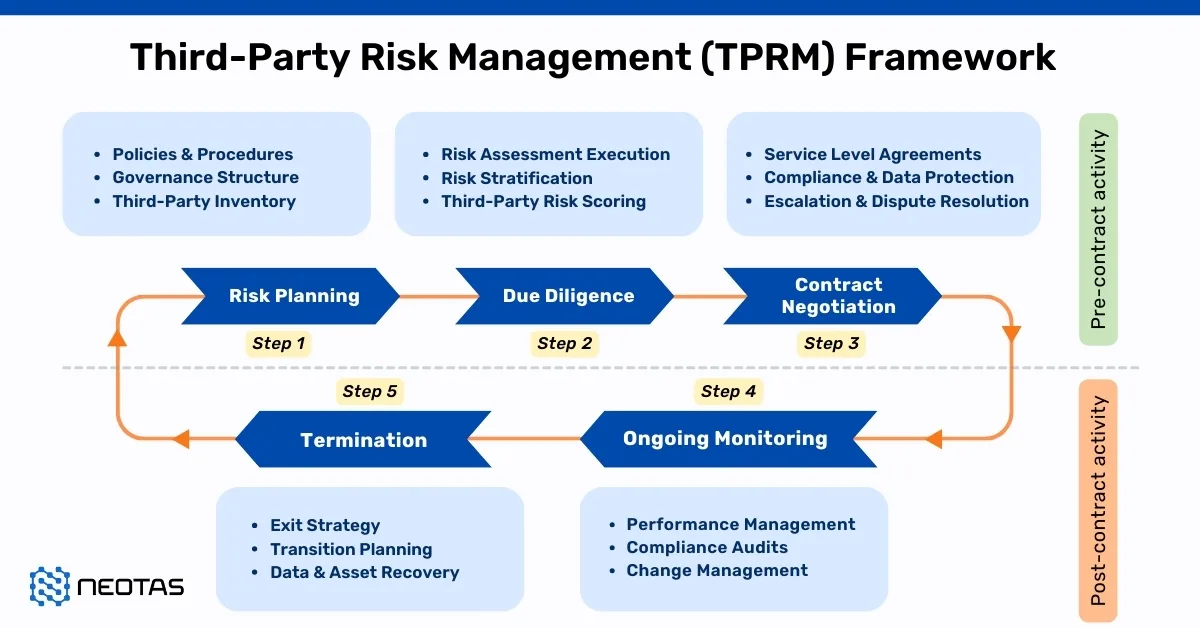
Third-party risk management lifecycle
The Third-Party Risk Management (TPRM) lifecycle serves as a structured framework for organisations to manage their relationships with external vendors effectively. Let’s delve into each phase of the TPRM lifecycle:
Phase 1: Third-Party Identification
- Identify existing and potential third-party vendors through various means, such as consolidating vendor information from spreadsheets, integrating with existing technologies, or conducting assessments and interviews across different business departments.
- Utilise self-service portals to gather preliminary information about new third parties, including personal information involved, business context, and data types.
Phase 2: Evaluation and Selection
- Evaluate vendors based on requests for proposals (RFPs) and select vendors that align with the organisation’s specific needs, objectives, and criteria.
- Consider factors such as vendor capabilities, reputation, pricing, and compatibility with organisational goals during the selection process.
Phase 3: Risk Assessment
- Conduct comprehensive vendor risk assessments to identify and evaluate potential risks associated with third-party relationships.
- Utilise standardised frameworks and assessments, such as ISO standards, SIG Lite, NIST guidelines, or industry-specific standards like HITRUST, to assess vendor security posture and compliance.
Phase 4: Risk Mitigation
- Prioritise and mitigate identified risks through appropriate risk treatment measures, such as implementing additional security controls, contractual obligations, or risk transfer mechanisms.
- Monitor risks for any changes or events that may impact the organisation’s risk profile, such as data breaches, regulatory changes, or vendor mergers.
Phase 5: Contracting and Procurement
- Review and negotiate vendor contracts to ensure alignment with TPRM objectives and requirements.
- Include key provisions, clauses, and terms in contracts related to scope of services, pricing, termination clauses, data protection, compliance, and liability.
Phase 6: Reporting and Recordkeeping
- Maintain detailed records of vendor engagements, assessments, contracts, and risk mitigation activities for audit and compliance purposes.
- Utilise TPRM software or platforms to centralise and manage vendor-related data and generate reports on program performance, risk levels, and compliance status.
Phase 7: Ongoing Monitoring
- Continuously monitor vendor performance, security posture, and compliance throughout the vendor lifecycle.
- Stay vigilant for any changes or events that may impact vendor risks, such as regulatory updates, operational changes, or security incidents.
Phase 8: Vendor Offboarding
- Develop a thorough offboarding process to safely and securely terminate vendor relationships when necessary.
- Conduct internal and external assessments to confirm that all appropriate measures were taken during the offboarding process and maintain a detailed evidence trail for compliance purposes.
By following the TPRM lifecycle, organisations can systematically manage third-party risks, enhance vendor relationships, and safeguard their assets, reputation, and regulatory compliance. This structured approach enables proactive risk identification, assessment, mitigation, and ongoing monitoring to ensure resilience and security in an ever-evolving business environment.
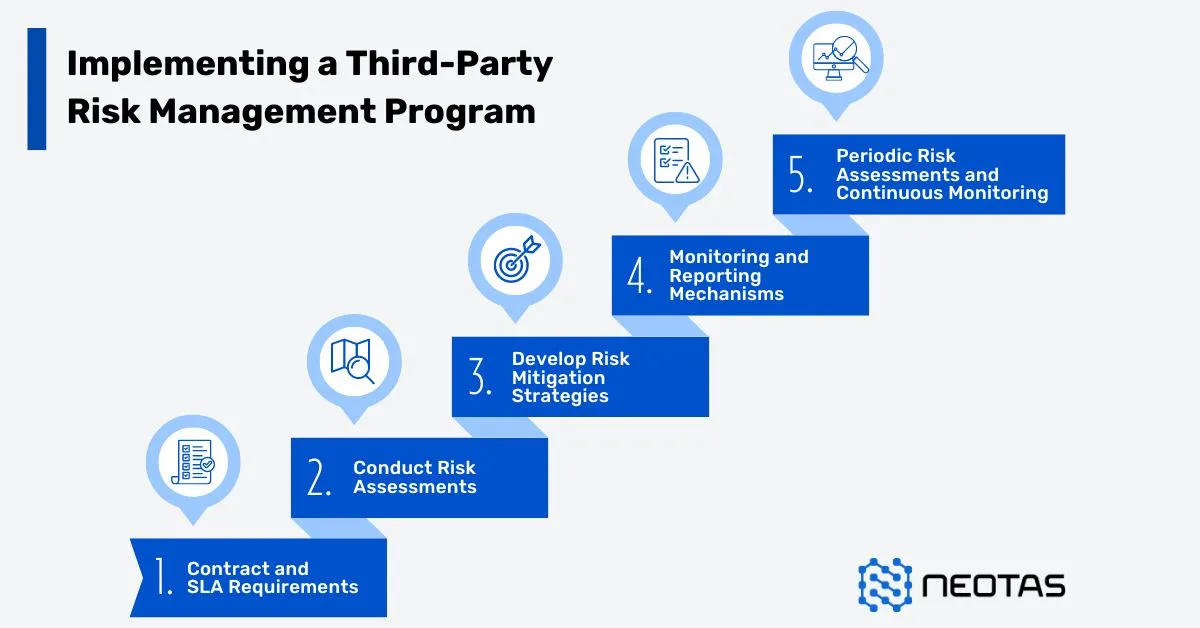
Implementing a Third-Party Risk Management Program
Implementing a robust Third-Party Risk Management (TPRM) program is essential for organisations looking to mitigate risks associated with their external partnerships effectively. Here’s a step-by-step guide to developing and implementing a TPRM program:
Step 1: Analysis – Contract and SLA Requirements
- Before onboarding any third party, conduct a thorough analysis to identify potential risks and assess the level of due diligence required.
- Utilise security ratings or risk assessment tools to evaluate the external security posture of vendors and determine if they meet the organisation’s minimum accepted score.
- Define a clear third-party risk appetite to accurately evaluate the potential impact of third-party risks on the organisation’s overall security posture.
Step 2: Engagement – Conduct Risk Assessments
- Once a vendor’s security rating meets the organisation’s standards, engage with the vendor to obtain detailed insights into their security controls.
- Request the vendor to complete a security questionnaire that provides comprehensive information on their security practices, policies, and procedures.
Step 3: Remediation – Develop Risk Mitigation Strategies
- If the vendor exhibits unacceptable risks during the engagement process, prioritise remediation efforts to address identified security issues.
- Implement a remediation plan in collaboration with the vendor, outlining specific actions required to mitigate risks and enhance security controls.
- Utilise dedicated tools or platforms to track and manage remediation activities efficiently, minimising the risk of overlooking critical issues.
Step 4: Approval – Monitoring and Reporting Mechanisms
- Following remediation efforts, assess the vendor’s readiness for onboarding based on the organisation’s risk tolerance, the criticality of the vendor, and compliance requirements.
- Make an informed decision on whether to proceed with the vendor relationship or explore alternative options based on the effectiveness of remediation efforts and alignment with risk management objectives.
Step 5: Periodic Risk Assessments and Continuous Monitoring
- Implement continuous monitoring mechanisms to track the security posture of onboarded vendors throughout the vendor lifecycle.
- Regularly assess vendor performance, compliance with security requirements, and adherence to contractual obligations.
- Utilise automated monitoring tools and processes to proactively identify and address emerging risks, ensuring ongoing security and compliance with organisational standards.
By following these steps, organisations can establish a structured and proactive approach to third-party risk management, effectively mitigating risks and enhancing the security of their external partnerships. A well-implemented TPRM program not only safeguards the organisation against potential threats but also fosters trust and resilience in its vendor relationships.
Once the decision to implement a TPRM program is made, the following are some questions that pave the foundation of the program:
- Should you engage a partner to assist with initiating and implementing the program?
- How can you effectively address and manage the expectations of internal stakeholders?
- Is there a clear assignment of responsibilities in the event of a data breach?
- What specific criteria must third parties meet to establish business relationships?
- Are external stakeholders adequately informed and capable of meeting compliance requirements?
- What potential financial implications might arise from imposing these requirements on vendors?
- How can the program be seamlessly integrated into existing vendor relationships?
Third-Party Risk Management Program Drivers
Establishing a robust Third-Party Risk Management (TPRM) program is imperative for organisations to effectively mitigate risks associated with their external vendor relationships. Various regulatory and compliance requirements serve as drivers for implementing TPRM programs, ensuring adherence to standards and safeguarding sensitive data. Here’s an in-depth exploration of the key drivers and stakeholders involved in TPRM programs:
Regulatory and Compliance Requirements:
- TPRM programs are often mandated by regulatory bodies and compliance standards across different industries and geographies.
- Regulations such as CMMC, EBA, FCA, FFIEC, HIPAA, NERC, NIST, NYDFS, and OCC outline specific guidelines for managing third-party risks.
- Compliance with these requirements is essential for protecting sensitive data, ensuring customer privacy, and avoiding legal penalties.
Cybersecurity Risk:
- The escalating threat landscape and the increasing frequency of cyberattacks underscore the importance of managing third-party cybersecurity risks.
- TPRM programs help organisations identify and mitigate vulnerabilities in their vendor ecosystem, reducing the risk of data breaches and cyber incidents.
Competitive Advantages:
- Implementing an effective TPRM program can provide organisations with a competitive edge by enhancing their security posture and resilience.
- Demonstrating robust risk management practices to customers, partners, and stakeholders can enhance trust and credibility, leading to increased business opportunities.
Internal Efficiency Drivers:
- Internal factors, such as the need for operational efficiency and streamlined procurement processes, drive the adoption of TPRM programs.
- Efficient vendor management practices enable organisations to optimise resource allocation, reduce costs, and improve overall operational performance.
Financial and Operational Risk Management:
- TPRM programs play a crucial role in managing internal financial and operational risks associated with vendor relationships.
- By identifying and addressing risks proactively, organisations can mitigate potential disruptions, financial losses, and reputational damage.
Customer Requirements:
- Customer expectations and contractual obligations often require organisations to implement robust TPRM measures.
- Meeting customer demands for data security, compliance, and risk management demonstrates commitment to quality and enhances customer satisfaction.
Stakeholders Involvement:
- Establishing a successful TPRM program requires collaboration and alignment among various internal and external stakeholders.
- Internal stakeholders, including executives, board members, legal, compliance, IT, and procurement teams, play a crucial role in defining program objectives and implementing effective workflows.
- External stakeholders, such as vendors, regulators, and customers, contribute to the development and implementation of TPRM policies and procedures.
Key Highlights for an effective Third-Party Risk Management Program:
Organisations must recognise the multifaceted drivers and stakeholders involved in TPRM programs to establish comprehensive risk management frameworks.
By addressing regulatory requirements, cybersecurity risks, competitive advantages, internal efficiency drivers, financial and operational risk management, and customer requirements, organisations can build resilient and trusted vendor relationships.
Collaboration and engagement with internal and external stakeholders are essential for the successful implementation and ongoing management of TPRM programs, ensuring alignment with organisational objectives and regulatory standards.
Key Focus Areas in the Third-Party Risk Management (TPRM)
To effectively mitigate risk exposures within TPRM environments, it is essential to establish organisational standards and protocols across the following domains:
- Third-Party Risk Management Focus Areas:
- Define requirements within contracts and service level agreements to address risk-related obligations comprehensively.
- Vendor Risk Analysis:
- Evaluate the vendor risk profile in alignment with the risk profile of the engagement or service provided to gain a holistic understanding of potential risks.
- Reporting Mechanism:
- Implement a dynamic reporting process driven by ongoing monitoring and risk assessment activities, allowing for prompt response to emerging events.
- Risk Assessment Approaches:
- Employ a balanced approach by combining periodic risk assessments (self-reported) with continuous risk monitoring (externally reported) methodologies to ensure comprehensive risk identification.
- Technology Integration:
- Utilise technology solutions to seamlessly integrate procurement, performance, and risk management functions onto a unified platform. This platform should provide stakeholders with real-time, updated information tailored to their specific requirements.
Third-Party Risk Management (TPRM) best practices
The TPRM best practices depends on the type of business you are in, the macro and micro environment, and the third and forth parties associated with your supply chain.
Here are few best practices that are critical to consider while implementing a TPRM framework:
Comprehensive Risk Assessment:
Start by conducting a thorough assessment of third-party risks. This involves identifying all potential risks associated with your third-party relationships, such as financial instability, data security vulnerabilities, regulatory compliance issues, and more. Prioritise these risks based on their potential impact on your organisation and the likelihood of occurrence. This initial assessment lays the foundation for developing targeted risk mitigation strategies.
Segmenting vendors into tiers based on their risk and criticality is a fundamental aspect of an effective Third-Party Risk Management (TPRM) program. By categorising vendors into tiers, organisations can allocate resources and attention based on the level of risk posed by each vendor. Typically, companies classify vendors into three tiers:
- Tier 1: High Risk, High Criticality:
- Tier 1 vendors are those that present the highest level of risk and are critical to the organisation’s operations. These vendors may have access to sensitive data, provide essential services, or have a significant impact on business continuity.
- Due to the heightened risk associated with Tier 1 vendors, organisations prioritise them for thorough due diligence and assessment. This may involve conducting on-site assessments, rigorous evidence collection, and in-depth analysis of the vendor’s security practices.
- Tier 2: Medium Risk, Medium Criticality:
- Tier 2 vendors pose a moderate level of risk and have a moderate impact on the organisation’s operations. While not as critical as Tier 1 vendors, they still require careful evaluation and monitoring.
- Organisations allocate resources to assess and mitigate the risks associated with Tier 2 vendors, balancing the level of scrutiny with the potential impact on business operations.
- Tier 3: Low Risk, Low Criticality:
- Tier 3 vendors present minimal risk and have a low impact on the organisation’s operations. These vendors typically provide non-critical services or have limited access to sensitive data.
- While Tier 3 vendors may require less intensive oversight compared to Tier 1 and Tier 2 vendors, they still undergo basic due diligence to ensure compliance with relevant policies and regulations.
When determining vendor tiers, organisations consider various factors to assess inherent risk. These factors may include:
- The nature of data shared with the vendor, including proprietary, personal, or sensitive information.
- The geographical scope of the vendor’s services and any cross-border data transfers.
- The vendor’s role in critical business functions and the potential impact of service disruptions.
- The potential consequences of unauthorised disclosure, modification, or destruction of information.
- Contractual value and the financial impact of vendor performance or failures.
By adopting a tiered approach to vendor management, organisations can streamline their TPRM processes, focusing resources where they are most needed to mitigate risks effectively and protect business continuity.
Third-Party Due Diligence and Vendor Selection:
Implement robust due diligence processes when selecting and onboarding third-party vendors. This includes evaluating their financial stability, reputation, cybersecurity measures, compliance with regulatory requirements, and adherence to industry standards. Assessing these factors helps ensure that you engage with trustworthy and reliable partners who align with your organisation’s values and objectives. Regularly review and update your vendor selection criteria to adapt to evolving risks and industry standards.
When devising a third-party risk management (TPRM) program, it’s essential to broaden your perspective beyond cybersecurity risks alone. While cybersecurity is undoubtedly a critical aspect, TPRM encompasses a wide range of risks that can significantly impact an organisation’s operations, reputation, and bottom line. By acknowledging and addressing these diverse risk factors, organisations can enhance the resilience and effectiveness of their TPRM initiatives.
Here’s a more detailed exploration of the various types of risks that should be considered within a comprehensive TPRM framework:
- Reputational Risks: Reputational risks arise from negative perceptions or public relations incidents involving third parties. These incidents can damage an organisation’s brand reputation and erode customer trust.
- Geographical Risks: Geographical risks pertain to the geographic locations in which third parties operate. Factors such as political instability, natural disasters, and regulatory differences across regions can impact the reliability and continuity of third-party services.
- Geopolitical Risks: Geopolitical risks encompass the potential impact of geopolitical events, conflicts, or diplomatic tensions on third-party operations. Changes in international relations or trade policies can affect supply chains and business relationships.
- Strategic Risks: Strategic risks involve threats to an organisation’s long-term objectives and competitive position resulting from third-party actions or decisions. These risks may include shifts in market dynamics, technological advancements, or competitive pressures.
- Financial Risks: Financial risks relate to the financial stability and viability of third-party entities. These risks may include bankruptcy, insolvency, or financial mismanagement, which can disrupt supply chains and contractual obligations.
- Operational Risks: Operational risks stem from failures or inefficiencies in third-party operations that impact service delivery or performance. This could include operational disruptions, service outages, or quality control issues.
- Privacy Risk: Privacy risks involve the unauthorised access, use, or disclosure of sensitive data entrusted to third parties. Non-compliance with data protection regulations or inadequate data security measures can result in privacy breaches and legal consequences.
- Compliance Risks: Compliance risks arise from third parties’ failure to adhere to relevant laws, regulations, or industry standards. Regulatory violations or non-compliance with contractual obligations can lead to legal penalties and reputational damage.
- Ethical Risks: Ethical risks relate to ethical misconduct or unethical business practices by third parties. This may include corruption, fraud, labour violations, or environmental irresponsibility, which can tarnish an organisation’s ethical standing.
- Business Continuity Risks: Business continuity risks involve disruptions to third-party operations that impede the continuity of an organisation’s business activities. These risks encompass factors such as supply chain interruptions, vendor dependency, and disaster recovery capabilities.
- Performance Risks: Performance risks refer to third parties’ inability to meet agreed-upon service levels, performance metrics, or quality standards. Poor performance can lead to customer dissatisfaction, contract disputes, and financial losses.
- Fourth-Party Risks: Fourth-party risks arise from the actions or vulnerabilities of subcontractors or downstream vendors associated with primary third-party relationships. These risks can complicate oversight and increase the complexity of risk management.
- Credit Risks: Credit risks involve the potential financial losses resulting from third parties’ defaulting on payment obligations or failing to meet financial commitments outlined in contracts or agreements.
- Environmental Risks: Environmental risks encompass the environmental impact of third-party activities, including pollution, resource depletion, or non-compliance with environmental regulations. Failure to address environmental risks can lead to regulatory fines, litigation, and reputational harm.
By acknowledging and addressing these diverse risk categories, organisations can develop a robust and resilient TPRM program that safeguards against a wide range of threats and vulnerabilities. It’s essential to adopt a holistic approach to risk management that integrates cybersecurity measures with broader risk mitigation strategies, thereby ensuring comprehensive protection for the organisation and its stakeholders.
Continuous Monitoring and Oversight:
Establish mechanisms for ongoing monitoring and oversight of third-party relationships throughout their lifecycle. This involves implementing regular assessments, audits, and performance reviews to evaluate vendor compliance with contractual obligations, service level agreements, and security protocols. Utilise technology solutions such as vendor risk management platforms to automate monitoring processes and streamline data collection and analysis. Additionally, foster clear communication channels with third-party vendors to address emerging issues promptly and collaboratively.
By adhering to these critical TPRM best practices, organisations can proactively identify, assess, and mitigate third-party risks, thereby safeguarding their operations, reputation, and bottom line.
Key Highlights of the TPRM best practices:
- Conduct thorough due diligence and continuous monitoring to ensure third-party accountability and risk mitigation.
- Enforce stringent access controls for third-party entities to safeguard sensitive data and resources.
- Utilise comprehensive risk intelligence to proactively identify and address potential threats posed by third-party relationships.
- Categorise relationships based on risk levels to allocate resources effectively and prioritise risk mitigation efforts.
- Foster collaboration with both internal and external auditors to enhance oversight and compliance with regulatory standards.
- Harness automation tools to streamline processes, increase efficiency, and strengthen the effectiveness of third-party risk management initiatives.
Role of Data and Technology in Third-Party Risk Management
In today’s globalised business landscape, where external vendors are integral to operations across industries, the role of technology and data in Third-Party Risk Management (TPRM) is crucial. These TPRM tools and resources play a pivotal role in enabling organizations to navigate the complex and dynamic ecosystem of interconnected risks with greater precision, efficiency, and agility.
Leveraging advanced TPRM technological solutions and harnessing the power of data analytics are instrumental in enhancing the effectiveness and responsiveness of TPRM processes.
Some of the key ways in which technology and data contribute to TPRM include:
- Data Aggregation and Integration: Technological solutions facilitate the aggregation and integration of data from diverse sources, including internal systems, external databases, and third-party platforms. This consolidated data repository provides organizations with a comprehensive view of their third-party relationships, enabling them to identify, assess, and monitor risks more effectively.
- Risk Assessment and Scoring: Analytics-driven tools utilize data-driven algorithms to assess and score the risk associated with each third-party relationship. By analyzing factors such as financial stability, compliance history, and cybersecurity posture, organizations can quantify risk levels and prioritize mitigation efforts accordingly.
- Continuous Monitoring and Surveillance: Technology enables real-time monitoring and surveillance of third-party activities and performance metrics. Automated monitoring tools can rapidly detect anomalies, deviations from established benchmarks, or emerging risks, allowing for prompt intervention and mitigation before they escalate into crises.
- Predictive Analytics and Modelling: Through the application of predictive analytics and modelling techniques, organizations can anticipate potential risks and vulnerabilities in third-party relationships. By analyzing historical data and extrapolating future trends, businesses can proactively identify and mitigate emerging threats, enhancing their resilience and agility in the face of uncertainty.
- Vendor Risk Assessment Platforms: Dedicated vendor risk assessment platforms provide tailored frameworks and templates for evaluating and managing third-party risks. These platforms streamline the assessment process, standardize risk evaluation criteria, and facilitate collaboration between internal stakeholders and third-party vendors.
- Blockchain Technology for Supply Chain Transparency: Blockchain technology’s immutable and transparent record-keeping capabilities can be leveraged to enhance supply chain transparency and traceability, mitigating risks such as counterfeit products, supply chain disruptions, and ethical lapses in supplier practices.
- AI-Powered Due Diligence: Artificial intelligence (AI) algorithms can analyze vast amounts of unstructured data, including news articles, social media posts, and regulatory filings, to assess the reputational and operational risks associated with third-party vendors. AI-powered due diligence tools augment traditional risk assessment methods, providing deeper insights and enhancing risk intelligence.
- Incident Response and Crisis Management: Technology-enabled incident response platforms facilitate swift and coordinated responses to third-party incidents, such as data breaches or service outages. These platforms streamline communication, coordination, and remediation efforts, minimizing the impact on operations and preserving organizational resilience.
By embracing technological innovations and harnessing the power of data-driven insights, organizations can enhance their TPRM capabilities, proactively identify and mitigate third-party risks, and safeguard their reputations, financial stability, and long-term sustainability in an increasingly interconnected and dynamic business environment.
How can Neotas Third-Party Risk Management and Third-Party Due Diligence solutions help?
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM) challenges. In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Moreover, Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
Request a Demo
If you’re curious about whether our Third-Party Risk Management and Third-Party Vendor Due Diligence solutions align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
FAQs on Third-Party Risk Management (TPRM)
What is Third-Party Risk Assessment?
- Third-Party Risk Assessment refers to the specific process of evaluating and quantifying the potential risks associated with engaging third-party vendors, suppliers, or partners.
- It involves identifying and understanding various types of risks that third parties may pose to the organisation, such as financial instability, data breaches, regulatory non-compliance, operational disruptions, reputational damage, and other potential liabilities.
- The focus of a Third-Party Risk Assessment is on conducting thorough due diligence, risk evaluation, and analysis of individual third-party relationships to identify potential risks and vulnerabilities.
What is Third-Party Risk Management Framework?
A Third-Party Risk Management Framework is a structured approach used by organisations to identify, assess, mitigate, and monitor risks associated with their third-party relationships. It provides guidelines, processes, and controls to effectively manage risks across the vendor lifecycle, ensuring alignment with business objectives and regulatory requirements.
What is a Vendor Risk Management?
Vendor Risk Management covers a wide range of activities beyond risk management, such as vendor selection criteria, contract negotiations, service level agreements (SLAs), vendor performance evaluations, vendor audits, and vendor relationship management.
While risk management is an essential component of Vendor Management, it may not be as comprehensive or focused on third-party risks specifically as in the TPRM framework.
What is third-party risk compliance?
Third-party risk compliance refers to ensuring that third-party relationships adhere to relevant laws, regulations, and industry standards to mitigate potential risks associated with non-compliance.
What is meant by third-party management?
Third-party management involves overseeing and managing relationships with external vendors, suppliers, contractors, and partners to ensure alignment with organisational goals and mitigate associated risks.
What is an example of a third-party risk management framework?
An example of a third-party risk management framework is the Shared Assessments Standardised Information Gathering (SIG) questionnaire, which provides a structured approach for assessing and managing third-party risks.
What is the meaning of third-party risk management?
Third-party risk management involves identifying, assessing, mitigating, and monitoring risks associated with engaging external parties to safeguard an organisation from potential harm or disruption.
What are the 5 phases of third-party risk management?
The five phases of third-party risk management typically include: assessment and categorisation, due diligence and selection, contract negotiation and onboarding, ongoing monitoring and oversight, and termination or renewal.
What is an example of a third-party risk?
An example of a third-party risk is a data breach caused by vulnerabilities in a vendor’s cybersecurity practices, leading to the exposure of sensitive information belonging to the organisation and its customers.
What are the roles in third-party risk management?
Roles in third-party risk management may include a third-party risk manager, vendor relationship manager, compliance officer, legal advisor, and cybersecurity analyst, among others.
Who is responsible for third-party risk?
Various stakeholders share responsibility for third-party risk, including senior management, risk management teams, procurement departments, legal and compliance teams, and business unit owners.
Why is third-party risk important?
Third-party risk is important because it helps organisations identify and mitigate potential threats posed by external parties, safeguarding reputation, financial stability, and regulatory compliance.
What is third-party lifecycle?
The third-party lifecycle refers to the stages of engagement with external vendors or partners, including identification, due diligence, contract negotiation, ongoing monitoring, and termination or renewal of the relationship.
How do you identify third-party risk?
Third-party risk can be identified through thorough due diligence, risk assessments, evaluating compliance with regulations and industry standards, and monitoring changes in the external environment.
What is ESG risk?
ESG (Environmental, Social, and Governance) risk refers to the potential negative impact that environmental, social, or governance factors associated with third-party relationships may have on an organisation’s sustainability or reputation.
What is a high-risk third-party?
A high-risk third-party is one that poses a significant threat to an organisation’s operations, finances, or reputation due to factors such as financial instability, inadequate cybersecurity measures, regulatory non-compliance, or poor performance.
What is a third-party risk in AML?
In Anti-Money Laundering (AML) compliance, third-party risk refers to the potential for external entities, such as vendors or partners, to facilitate money laundering or terrorist financing activities, posing regulatory and reputational risks to the organisation.
What is a third-party risk analyst?
A third-party risk analyst is responsible for assessing, analysing, and monitoring risks associated with engaging external vendors, suppliers, or partners, and providing recommendations for risk mitigation strategies to protect the organisation.
Read more about Third-Party Risk, TPRM software, and TPRM processes.
TPRM Solutions:
- Enhanced Due Diligence
- Management Due Diligence
- Customer Due Diligence
- Simplified Due Diligence
- Third Party Risk Management
- Open Source Intelligence (OSINT)
- Introducing the Neotas Enhanced Due Diligence Platform
TPRM Case Studies:
- Third Party Risk Management (TPRM) Using OSINT
- Open-source Intelligence For Supply Chain – OSINT
- ESG Risk Management Framework with Neotas’ OSINT Integration
- Open Source Intelligence In AML Compliance | Case Study
- Identifying Difficult And Dangerous Senior Managers
- ESG Risk Investigation Uncovers Supply Chain Risks
- Financial Crime Compliance & Risk Management Trends
- Network Analysis Reveals International Links In Credit Risk Case
- Network Analysis and Due Diligence – Terrorist Financing
- Using OSINT For Sources Of Wealth Checks
- ESG Risks Uncovered In Investigation For Global Private …
- PEP Screening: Undisclosed Political Links Uncovered For European Organisation



 New Whitepaper and Checklist
New Whitepaper and Checklist