Risk Management Framework
A practical playbook for governance, compliance, and strategic resilience. Board-Ready Risk Intelligence Playbook: 30-Day Path from Framework to ROI. This article will help you reduce blind-spots, cut decision-latency, and unlock risk-adjusted growth.
Business risk is no longer limited to isolated incidents or regulatory breaches—it has become a continuous, systemic concern that requires structured, organisation-wide attention. This is where the risk management framework (RMF) comes into play.
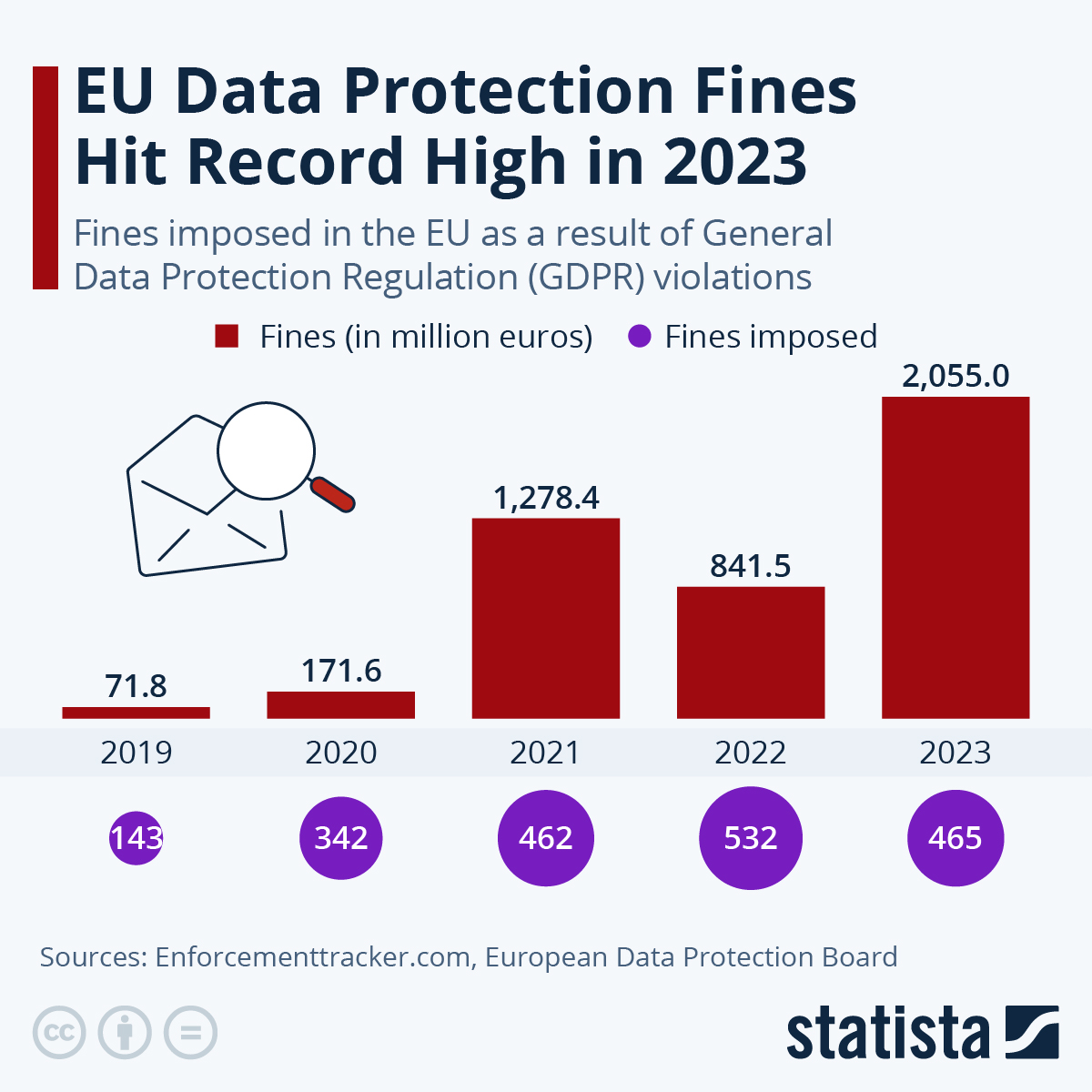
In 2023, GDPR fines surged to €2.1 billion—more than 2019 to 2021 combined—driven by Meta’s €1.2 billion penalty. Average fines also rose sharply to €4.4 million per violation.
This sharp rise in both volume and severity of fines highlights why a robust Risk Management Framework (RMF) is essential—to proactively identify, assess, and mitigate compliance and data protection risks before they escalate into costly regulatory actions.
What is a Risk Management Framework?
A risk management framework is a structured, formalised system that outlines how an organisation identifies, assesses, manages, monitors, and reports risks. It provides a consistent methodology and governance structure for ensuring that risks are addressed across departments, projects, and decision-making levels.
The framework is not a single document or tool. Instead, it encompasses the governance structure, guiding principles, processes, roles, templates, systems, and communication channels used to embed risk thinking across the business.
An effective business risk management framework ensures that both strategic and operational risks are proactively managed—not just for regulatory compliance, but to safeguard value, enable resilience, and support long-term performance.
Risk Policy vs. Risk Framework vs. Risk Process – What’s the Difference?
To avoid confusion, it’s important to differentiate between three commonly misunderstood terms in corporate risk governance:
| Term | Purpose |
|---|---|
| Risk Policy | A board-approved statement of intent that outlines the organisation’s commitment to risk management. It defines scope, roles, responsibilities, and the overall approach. |
| Risk Framework | The overarching structure that connects the risk policy to its implementation. It includes methodologies, tools, risk categorisation, escalation protocols, reporting mechanisms, and integration points with strategy and operations. |
| Risk Process | The step-by-step workflow through which individual risks are identified, analysed, evaluated, treated, and monitored. It operates within the framework and delivers the day-to-day execution. |
Practical example:
If the risk policy is the “why,” the risk management framework is the “how,” and the risk process is the “what and when.”
Why Every Organisation Needs an Integrated Risk Management Framework
No matter the size, sector, or complexity of an organisation, risks will exist—be it financial volatility, cyber threats, regulatory change, supply chain disruption, or reputational exposure. An integrated risk management framework enables the business to:
Align risk with strategy – helping leadership understand how key risks may affect business goals, and enabling scenario planning and resource allocation.
Enable consistent decision-making – standardised risk assessments reduce subjective judgement and allow comparability across functions.
Support regulatory compliance – many industries (e.g. financial services, energy, pharmaceuticals) require a formal risk framework to meet audit and compliance standards.
Improve response times – a clear framework ensures risks are escalated and acted upon quickly, reducing the likelihood of crisis.
Enhance stakeholder trust – whether it’s investors, regulators, partners, or customers, stakeholders expect risk to be managed transparently and systematically.
The absence of such a framework often leads to fragmented efforts, duplicated controls, and blind spots that are only revealed during a crisis or audit.
Common Misconceptions and Pitfalls
Despite widespread awareness of risk management in theory, several recurring issues prevent organisations from fully realising its value:
1. Treating RMF as a compliance obligation only
Many businesses create a framework purely to meet regulatory checklists, without embedding it into operational or strategic planning. This results in a disconnect between risk documentation and real-world business behaviour.
2. Assuming risk registers alone are sufficient
A list of risks without governance, prioritisation, or linkage to business objectives lacks the depth to influence action or inform leadership decisions.
3. Over-engineering the framework
While thoroughness is important, overly complex frameworks often deter adoption, especially among non-risk functions. Simplicity, clarity, and scalability are vital.
4. Failing to link risk appetite to decision-making
If risk appetite is not clearly defined, risk-taking becomes arbitrary. This leads to inconsistency in project approvals, investment decisions, or vendor onboarding.
5. Lack of continuous improvement
Risk management frameworks must evolve with changes in business models, market conditions, and regulatory landscapes. Static frameworks quickly become obsolete.
A risk management framework done well is one that is practical, tailored to the organisation’s context, and embedded into daily decision-making—from front-line teams to the boardroom. It is not about avoiding all risks but managing them wisely and intentionally.
In the following sections, we will explore various frameworks such as ISO 31000, COSO ERM, NIST RMF, and others, along with industry-specific applications across cybersecurity, AI, compliance, third-party risk, and financial controls.
This guide will help you not only understand but apply risk frameworks with clarity, relevance, and impact.
Key Pillars of a Risk Management Framework
A robust risk management framework is built on well-defined, interconnected pillars that ensure risk is not treated as a siloed function but as a core part of how the organisation thinks, plans, and operates. The following components form the structural foundation of any effective and scalable enterprise risk management framework.
1. Risk Governance
Definition:
Risk governance refers to the structures, roles, and responsibilities that guide how risk is managed across the organisation, starting from the boardroom.
Key Elements:
Tone from the Top: The board and senior leadership set the tone by clearly articulating their commitment to risk oversight. Their visible engagement is essential to embed a risk-aware culture.
Risk Culture, Ethics, and Accountability: A strong risk culture promotes ethical behaviour, encourages open communication, and supports responsible decision-making at all levels.
Policy Ownership and Oversight Committees: Risk policies must be owned, maintained, and enforced by designated roles—typically the Chief Risk Officer (CRO), audit committees, or risk steering groups. Their mandate includes escalation paths, breach reviews, and periodic evaluations.
A governance framework ensures risk is not just tracked but actively owned.
2. Risk Identification
Definition:
This pillar ensures that the organisation has mechanisms to detect, document, and categorise risks before they manifest.
Key Elements:
Internal and External Risk Drivers: These include operational breakdowns, regulatory change, political instability, technological disruption, and environmental factors.
Risk Taxonomies: Classification into categories—strategic, operational, compliance, financial, cyber, and reputational—enables focused mitigation and reporting.
Emerging Risks and Black Swan Mapping: Organisations must go beyond traditional threats and actively scan for low-probability, high-impact risks, including those arising from ESG issues, geopolitical shifts, or AI misuse.
Risk identification must be forward-looking, not simply retrospective.
3. Risk Assessment & Analysis
Definition:
Once risks are identified, they must be assessed for their potential impact and likelihood, using structured methodologies.
Key Elements:
Qualitative and Quantitative Models: These range from simple red–amber–green (RAG) ratings to probabilistic modelling, Monte Carlo simulations, and financial impact estimates.
Risk Scoring Matrix: This standard tool evaluates likelihood × impact to assign a risk severity rating, helping to prioritise response.
Heat Maps, Registers, and Velocity Indicators: A heat map visualises risk concentration, while the register documents controls and ownership. Velocity (how quickly a risk could materialise) is increasingly used for high-speed risk environments.
Good analysis separates background noise from real threats.
4. Risk Treatment & Mitigation
Definition:
This is the process of deciding how to respond to identified risks and implementing suitable control strategies.
Key Elements:
Response Options: Risks can be avoided (by ceasing the activity), reduced (through controls), transferred (via insurance or outsourcing), or accepted (within defined thresholds).
Internal Controls: These include process-level controls, segregation of duties, automated alerts, access restrictions, and training interventions.
Insurance and Outsourcing Strategies: Transferring certain risks to third parties requires careful vendor due diligence, performance monitoring, and contract design.
Treatment plans must be realistic, budget-aligned, and time-bound.
5. Monitoring & Review
Definition:
Risks and controls must be continuously monitored to ensure effectiveness, detect changes, and support decision-making.
Key Elements:
Key Risk Indicators (KRIs): KRIs are measurable signals that flag increasing risk levels, such as customer complaints, system failures, or overdue audits.
Continuous Control Testing: Regular validation of control design and operating effectiveness is essential to maintain trust in the framework.
Internal Audits and External Assessments: Third-line assurance functions, external audits, and regulator feedback help identify blind spots and maintain objectivity.
Monitoring turns frameworks into living systems, not static documents.
6. Communication & Reporting
Definition:
Transparent communication ensures that risks are escalated promptly and that leadership receives the right level of insight at the right time.
Key Elements:
Risk Dashboards: Customised dashboards visualise risk exposure, trends, and control status for different stakeholders, including operational managers, compliance leads, and the board.
Regulatory and Compliance Disclosures: Many industries (e.g., finance, energy, pharmaceuticals) require risk reporting aligned to local and global standards.
Real-Time Risk Intelligence: Incorporating external data (e.g. legal filings, ESG ratings, cyber threat feeds) into reporting adds predictive value and external context.
If risk isn’t communicated effectively, it won’t be acted upon.
7. Integration with Strategy
Definition:
The final and most mature pillar of a risk management framework involves the full integration of risk thinking into strategy, performance management, and resource allocation.
Key Elements:
Risk Appetite Statements: These clarify how much risk the organisation is willing to take in pursuit of its objectives, guiding investment and decision-making boundaries.
Scenario Planning and Risk-Adjusted Decisions: Using “what-if” modelling to evaluate the impact of uncertain conditions on strategic plans, especially in areas like capital investment, market entry, or digital transformation.
Integration into Project Management and Budgeting: Risk registers should not sit in isolation—they must influence programme timelines, cost buffers, and contingency plans.
A mature risk framework is not an overhead—it is a strategic asset.
A well-structured risk management framework must balance rigour with agility. It should offer a common language for risk across the organisation while remaining flexible enough to adapt to different contexts, departments, and geographies. The goal is not simply to comply, but to enable better decisions, earlier awareness, and smarter resilience.
Risk Management Frameworks to Learn From
| Framework | Focus Area | Best For |
|---|---|---|
| ISO 31000 | Enterprise Risk Management | Cross-industry standard |
| COSO ERM | Internal control, governance, risk strategy | Finance, audit, board-level governance |
| NIST RMF | Cybersecurity risk in federal systems | Government, regulated tech infrastructure |
| Basel III/IV | Operational and financial risk | Banking and financial institutions |
| Solvency II | Insurance sector capital risk | Insurance and actuarial risk teams |
NIST Risk Management Framework
The NIST Risk Management Framework (RMF) is a structured methodology developed by the National Institute of Standards and Technology for managing cybersecurity and privacy risks across information systems. Widely adopted by US federal agencies and defence sectors, it is increasingly used by private organisations handling critical infrastructure or sensitive data.
What Is the NIST RMF?
The RMF provides a structured, repeatable process to ensure that risks are effectively identified, assessed, mitigated, and monitored in alignment with federal regulations. The core guidance is detailed in NIST Special Publication 800-37 Revision 2:
NIST SP 800-37 Rev. 2:
https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final
This framework aligns with the Federal Information Security Modernization Act (FISMA) and is often implemented alongside NIST SP 800-53, which lists recommended security and privacy controls:
NIST SP 800-53 (Control Catalogue):
https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
NIST RMF PDF: Summary Highlights: The RMF integrates security and privacy considerations from the outset and provides detailed guidance for roles including system owners, authorising officials, and risk officers. While lengthy, the official publication serves as the most authoritative source.
Note: Always consult the official NIST documents as your primary reference.
The full guidance, published as NIST SP 800-37 Rev. 2, is titled:
“Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy”
While the document is publicly accessible and comprehensive, many professionals find its length (140+ pages) overwhelming. Below is a structured commentary to simplify its key takeaways:
1. Integrated Approach:
The RMF integrates privacy and security—not as separate domains but as co-dependent objectives. This allows organisations to manage cyber risk and data protection in unison.
2. Tiered Governance:
The framework distinguishes between organisation-level, mission/business process-level, and system-level risk, enabling tailored strategies at each layer.
3. Flexibility Across Roles:
It supports a broad stakeholder base, from system owners and authorising officials to privacy officers and auditors.
4. Emphasis on Continuous Monitoring:
Unlike older models that operated in periodic certification cycles, the RMF is continuous by design, requiring dynamic risk assessments and real-time updates.
Note: While the Thomas Marsland book “Unveiling the NIST Risk Management Framework (RMF)” offers practitioner insights and real-world commentary, this guide focuses on original interpretation without replicating proprietary summaries or commercial reproductions.
The Six-Step RMF Process Explained
The NIST RMF comprises six key steps, with a preparatory stage included to strengthen initial alignment and stakeholder readiness.
| Stage | Description |
|---|---|
| 0. Prepare | Define roles, responsibilities, assets, and risk tolerance before initiating formal risk management activities. |
| 1. Categorise | Classify the system based on impact (low, moderate, high) to confidentiality, integrity, and availability. |
| 2. Select | Choose baseline security controls (from NIST SP 800-53), and tailor based on the environment. |
| 3. Implement | Deploy and configure the selected controls across systems, platforms, and users. |
| 4. Assess | Conduct control assessments to determine effectiveness and identify any gaps. |
| 5. Authorise | Senior official evaluates residual risk and formally grants system approval to operate (ATO). |
| 6. Monitor | Continuously assess and report on control performance, system changes, and risk posture. |
Key Feature:
Each step includes defined inputs, tasks, outputs, and roles—creating traceability and audit-readiness throughout the lifecycle.
Security & Privacy Synergy:
Unlike many frameworks, RMF integrates security and privacy risk concurrently, rather than sequentially—essential for GDPR and other privacy-focused compliance efforts.
The NIST Risk Management Framework remains a cornerstone of cyber and IT system assurance. Its structured methodology, clear control mapping, and lifecycle integration make it a valuable tool for managing complex digital environments.
However, adopting RMF effectively requires more than following steps—it demands executive sponsorship, proper training, scalable tooling, and a shift from compliance-centric mindsets to continuous, intelligence-led risk monitoring.
Organisations outside the public sector are increasingly customising RMF to suit commercial contexts, proving its flexibility and relevance beyond government use.
COSO Enterprise Risk Management Framework
Structure, Use, and Comparison with ISO 31000
The COSO Enterprise Risk Management (ERM) Framework is a globally recognised governance model that helps organisations identify, manage, and integrate risks into strategic decision-making. Developed by the Committee of Sponsoring Organizations of the Treadway Commission (COSO), it is widely adopted by listed companies, financial institutions, auditors, and regulators—particularly in North America and sectors where internal controls and financial reporting are closely scrutinised.
COSO ERM vs ISO 31000
While both COSO ERM and ISO 31000 serve to guide enterprise-wide risk management, their approaches and structures differ in focus and formality:
| Aspect | COSO ERM | ISO 31000 |
|---|---|---|
| Publisher | COSO (USA-based consortium of professional bodies) | International Organization for Standardization |
| Scope | Integrated risk and internal control, with emphasis on financial governance | Broad enterprise risk guidance applicable across industries |
| Structure | Component-based (20 principles across 5 components) | Principle-based (11 principles, 5-step process) |
| Alignment with Audits | Strong alignment with SOX, PCAOB, and financial audits | Used for operational and strategic risk contexts |
| Documentation Style | Prescriptive and structured | Flexible and interpretation-led |
Reference links:
COSO ERM 2017 Framework Summary: https://www.coso.org/Documents/2017-COSO-ERM-Integrating-with-Strategy-and-Performance-Executive-Summary.pdf
ISO 31000: https://www.iso.org/iso-31000-risk-management.html
COSO ERM Components: The 5 Pillars and 20 Principles
The 2017 COSO ERM update focuses on linking risk to strategy and performance. It outlines 20 principles across five interrelated components:
Governance & Culture
Establishes board oversight, defines operating structures, promotes desired behaviours, and fosters risk awareness.
Strategy & Objective-Setting
Evaluates risk in strategic planning, defines risk appetite, and aligns business goals with the organisation’s tolerance for uncertainty.
Performance
Identifies and assesses risks that may affect the achievement of objectives, prioritises risks, and implements risk responses.
Review & Revision
Assesses changes in internal/external environment and modifies the risk approach accordingly.
Information, Communication & Reporting
Promotes risk-informed communication and develops risk reporting structures that support decision-making.
COSO’s 2013 Internal Control–Integrated Framework also remains relevant, especially for SOX compliance and financial reporting integrity: https://www.coso.org/Pages/ic.aspx
Use in Financial Institutions and Board-Level Governance
Why it matters: In banking, insurance, and capital markets, COSO ERM is often the preferred framework because it provides an auditable structure for managing financial risk, operational resilience, and regulatory compliance—especially under mandates such as SOX (US), CRR/CRD (EU), and Basel III (globally).
Common board-level applications:
Risk Appetite and Tolerance Definitions: COSO principles guide boards in formalising how much risk they are willing to take in different domains.
Strategic Risk Reviews: Linking risk management to key decisions such as mergers, market entries, or product launches.
Three Lines Model Alignment: Clarifies risk roles between business units, risk/compliance functions, and internal audit.
Audit Committee Oversight: COSO provides a vocabulary and structure for independent assurance, internal control reviews, and risk disclosures.
Example in practice: A global bank using COSO may apply its principles to oversee anti-money laundering risks, aligning internal controls with enterprise-wide KYC obligations while also integrating them into broader operational and reputational risk discussions at the board level.
The COSO ERM Framework is a foundational tool for aligning governance, risk, and performance—particularly in complex, regulated environments. Its structure allows financial institutions and large corporates to demonstrate formal control maturity, improve risk reporting, and enhance stakeholder confidence.
ISO 31000 Risk Management Framework
Principles, Structure, and Enterprise Applications
The ISO 31000 Risk Management Framework is an internationally recognised standard developed by the International Organization for Standardization (ISO) to provide structured, principles-based guidance for managing risk across all organisational types and sizes. It is widely used in both public and private sectors due to its flexibility, non-prescriptive nature, and cross-industry applicability.
Principles and Structure of ISO 31000
Published as ISO 31000:2018, the framework defines risk as the “effect of uncertainty on objectives” and sets out a system to systematically identify, assess, treat, and monitor risks in alignment with strategic goals.
The Framework Is Built on Three Core Elements:
The Principles (8 foundational guidelines):
These include integration into governance, structured approach, customisation to context, inclusion of stakeholders, dynamic iteration, use of best information available, consideration of human/cultural factors, and continual improvement.The Framework:
ISO 31000 advocates embedding risk management into all aspects of the organisation—from leadership and planning to operations and decision-making. It recommends clear roles, resources, and oversight structures.The Process:
A five-step cycle:
- Risk identification
- Risk analysis
- Risk evaluation
- Risk treatment
- Monitoring and review
Plus, recording and reporting are embedded throughout.
Official reference:
https://www.iso.org/iso-31000-risk-management.html
Unlike control-based frameworks, ISO 31000 does not prescribe specific risk controls or metrics. Instead, it guides organisations to design their own systems based on risk context, appetite, and strategic objectives.
Application in Multi-Industry Governance Models
One of ISO 31000’s key strengths is its adaptability across industries and regulatory environments. Its neutral, principle-driven format makes it suitable for:
Manufacturing and Supply Chain: Managing operational disruptions, safety risks, and regulatory compliance
Financial Services: Supporting enterprise risk governance without imposing sector-specific control structures
Healthcare and Life Sciences: Enabling patient safety, clinical risk management, and GDPR alignment
Public Sector: Informing national infrastructure and service delivery risk strategies
Energy, Mining and Construction: Managing physical, ESG, and project-level risks with a uniform risk vocabulary
In most settings, ISO 31000 is integrated with other frameworks (e.g. ISO 27001 for information security, ISO 22301 for business continuity) to create a layered, enterprise-wide risk governance model.
Pros and Cons for Mid-Market and Large Enterprises
| Pros | Cons |
|---|---|
| Universally applicable, regardless of size or sector | May require supplementary controls or frameworks for regulated sectors |
| Non-prescriptive: allows tailoring to business model | Lacks detailed control catalogues (e.g. compared to NIST or COSO) |
| Promotes a risk-aware culture across all levels of decision-making | Implementation maturity varies without structured oversight mechanisms |
| Easily integrates with other ISO standards (27001, 9001, 22301 etc.) | Not always sufficient for audit or compliance assurance on its own |
| Supports both strategic and operational risk management | May be too broad without specific industry adaptation |
Best fit use case: Mid-market firms aiming to develop a coherent, business-aligned risk strategy often start with ISO 31000. Large enterprises use it as a unifying risk philosophy, especially when operating across multiple jurisdictions or industries.
The ISO 31000 Risk Management Framework is not a plug-and-play checklist but a foundational guide to creating a risk-aware organisation. Its real value lies in embedding risk thinking into strategy and culture—not just controls. For organisations seeking scalable, industry-neutral risk management practices, ISO 31000 remains the global benchmark.
Download overview (PDF summary):
https://www.iso.org/files/live/sites/isoorg/files/store/en/PUB100426.pdf
Cybersecurity Risk Management Frameworks
From Framework Selection to Intelligence-Driven Cyber Defence
Cybersecurity is no longer a purely technical issue—it is now a critical risk management priority. As cyber threats grow in sophistication and frequency, organisations require structured frameworks to assess, monitor, and mitigate these risks with clarity and control. Below, we explore two widely used frameworks, practical tools, and a maturity path from reactive to predictive cyber risk management.
NIST Cybersecurity Framework (CSF) vs. NIST Risk Management Framework (RMF)
Both the NIST Cybersecurity Framework (CSF) and the NIST Risk Management Framework (RMF) offer robust structures for cyber risk management, but they serve different purposes and user profiles.
| Feature | NIST CSF | NIST RMF |
|---|---|---|
| Purpose | High-level framework for improving cybersecurity posture | Detailed risk management lifecycle for information systems |
| Audience | Business leaders, IT teams, private sector | US federal agencies, defence, and regulated contractors |
| Structure | 5 core functions: Identify, Protect, Detect, Respond, Recover | 6-step process: Categorise, Select, Implement, Assess, Authorise, Monitor |
| Prescriptiveness | Flexible and voluntary | Control-specific, compliance-driven (linked to NIST SP 800-53) |
| Use Case | Strategy development, benchmarking, board reporting | System-level control implementation and certification |
Official references:
- NIST CSF v1.1: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
- NIST CSF 2.0 (released 2024): https://www.nist.gov/cyberframework
- NIST RMF (SP 800-37): https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final
In practice: Use CSF to set strategic priorities and build a cyber roadmap; use RMF to implement controls and demonstrate regulatory alignment.
Cybersecurity Risk Register Template
A cyber risk register is a foundational tool for documenting, tracking, and prioritising cyber risks across assets, systems, and vendors.
Core Elements of a Cyber Risk Register:
| Risk ID | Asset/System | Threat Scenario | Impact | Likelihood | Risk Rating | Control Owner | Current Control | Residual Risk |
|---|---|---|---|---|---|---|---|---|
| CR-001 | Email System | Phishing leading to data breach | High | Likely | High | CISO | Email gateway, training | Medium |
| CR-002 | Web App | OWASP vulnerability exploit | Medium | Possible | Medium | DevSecOps | WAF, code scanning | Low |
Optional columns: risk velocity, risk appetite threshold, planned treatment actions, next review date.
Using Threat Intelligence in Cyber Risk
Traditional frameworks often rely on static assessments, but cyber risks evolve daily. Integrating threat intelligence—both internal (e.g. logs, SOC alerts) and external (e.g. feeds from ISACs, government advisories, dark web monitoring)—brings real-time relevance to your risk framework.
Applications of Threat Intelligence:
- Enriching the risk register with live indicators of compromise (IOCs)
- Prioritising patch management based on emerging exploit trends
- Enhancing vendor risk monitoring using open-source intelligence (OSINT) tools
- Supporting incident response playbooks with current TTPs (tactics, techniques, procedures)
From Reactive to Predictive Cyber Risk Management
Organisations often begin with reactive practices—responding to incidents as they occur. A mature cybersecurity risk management framework enables a shift to predictive posture, characterised by risk anticipation, control automation, and data-driven decision-making.
Maturity Path:
- Reactive – Firefighting after incidents occur; no structured register
- Defined – Risk inventory maintained; controls are in place but manually monitored
- Integrated – Cyber risk linked to enterprise risk; real-time dashboards; board visibility
- Predictive – Threat intelligence drives prioritisation; AI-supported anomaly detection; automated control responses
Features of a Predictive Framework:
- Use of AI/ML for anomaly detection and trend analysis
- Integration of cyber risk metrics with business impact analysis
- Automated alerts based on early warning signals (e.g. KRI breaches)
- Dynamic risk scoring and control reassessment
A cybersecurity risk management framework should not be treated as a static checklist. Whether you’re using NIST CSF, RMF, or a hybrid approach, the real objective is to enable business resilience through informed, risk-based decision-making.
Risk leaders must ensure that cybersecurity is understood in business terms—prioritising risks that affect operations, finance, reputation, and regulatory exposure. When combined with real-time threat intelligence and predictive tooling, cyber risk management becomes a proactive enabler of trust, not just a technical safeguard.
Artificial Intelligence Risk Management Frameworks
Governing AI Systems with Structure, Responsibility, and Foresight
As artificial intelligence (AI) systems become increasingly embedded in critical decision-making—across healthcare, finance, HR, law enforcement, and beyond—the need for a dedicated AI risk management framework is now business-essential. Managing AI risk requires a new class of tools, roles, and regulatory readiness.
NIST AI RMF: Structure, Intent, and Implementation Challenges
The NIST AI Risk Management Framework (AI RMF), released in 2023, is a voluntary guidance document designed to help organisations develop and deploy trustworthy AI systems. It offers a structured model to identify, assess, manage, and monitor AI-related risks throughout the lifecycle.
Four Core Functions:
- Map – Understand context, systems, and stakeholder risks
- Measure – Evaluate risk levels and performance impacts
- Manage – Implement controls, mitigations, and governance
- Govern – Establish accountability, policies, and oversight
Official source: https://www.nist.gov/itl/ai-risk-management-framework
Implementation Challenges:
- Lack of consistent metrics to evaluate AI risk
- Limited technical understanding among compliance and risk teams
- Difficulty embedding AI governance into agile development environments
- Managing both model-level and organisational-level responsibilities
The NIST AI RMF emphasises socio-technical alignment, ensuring fairness, accountability, and explainability—not just technical precision.
Why AI Risk Is Not Just About Model Bias
While algorithmic bias and fairness dominate public discourse, AI risk spans multiple domains:
- Security risks: Model inversion, data poisoning, adversarial attacks
- Privacy risks: Inference of personal information from model outputs
- Operational risks: Model drift, black-box dependencies, misalignment with evolving data
- Regulatory risks: Misuse of AI in hiring, surveillance, or financial decisions
- Reputational risks: Harm from unintended outputs or public backlash
True AI risk management must address input data quality, model explainability, downstream impacts, auditability, and real-world alignment—not just performance metrics.
AI + Risk Intelligence = Next-Gen Controls
Integrating AI risk management frameworks with risk intelligence platforms enables more adaptive, scalable, and transparent governance. Key enablers include:
- Explainability engines (e.g. SHAP, LIME) for audit-friendly transparency
- Model monitoring tools for drift detection, output anomalies, and compliance triggers
- Governance dashboards showing risk heatmaps linked to AI applications
- Cross-functional governance boards involving legal, tech, compliance, and ethics teams
When paired with broader frameworks like NIST RMF, ISO/IEC 23894, or OECD AI Principles, the AI RMF becomes a cornerstone of future-ready risk programmes.
As AI becomes core to decision systems, an AI-specific risk management framework is not optional—it is a governance necessity. From safeguarding individual rights to protecting business reputation, AI risk management must be systemic, accountable, and dynamic.
IT and Data Risk Management Frameworks
Managing Technology, Privacy, and Resilience in the Digital Enterprise
As organisations digitise operations and shift to cloud-native infrastructures, managing IT and data risk has become a fundamental requirement—not just for security and compliance, but for operational continuity and business trust.
An effective IT and data risk management framework enables organisations to identify, mitigate, and monitor risks associated with technology systems, data assets, cloud environments, and regulatory obligations.
IT Risk vs. Cyber Risk: What’s the Difference?
Though often used interchangeably, IT risk and cyber risk refer to distinct, though overlapping, domains.
| IT Risk | Cyber Risk |
|---|---|
| Broader in scope—includes system outages, vendor failures, obsolete technology, and integration issues | Specific to threats from unauthorised digital access or disruption |
| Includes hardware/software lifecycle risk | Focuses on attack vectors (malware, phishing, DDoS, etc.) |
| Often rooted in internal architecture or process gaps | Originates from external threat actors or vulnerabilities |
| Managed through IT governance, service management (ITIL), architecture reviews | Managed via security frameworks (e.g. NIST CSF, ISO 27001) |
Understanding this distinction helps allocate ownership, budget, and control priorities accurately across IT, security, and risk teams.
Data Privacy and GDPR-Led Risk Controls
Modern risk frameworks must address not only data security, but also data privacy—with legal obligations under regulations such as the General Data Protection Regulation (GDPR), CCPA, and emerging global data laws.
Key GDPR-led controls include:
- Data flow mapping to identify where personal data is collected, processed, and stored
- Lawful basis tracking for each processing activity (consent, contract, legal obligation, etc.)
- Privacy Impact Assessments (PIAs) or Data Protection Impact Assessments (DPIAs) for high-risk systems
- Role-based access control (RBAC) to minimise exposure
- Encryption at rest and in transit, with key management
- Data subject rights management, including erasure and portability
Organisations must integrate these controls into their broader IT risk framework—not treat them as standalone compliance tasks.
Reference: https://gdpr.eu/checklist/
Business Continuity and Disaster Recovery (BC/DR)
Key components include:
- Business continuity plans for essential functions
- Disaster recovery for IT systems and data
- Defined RTOs and RPOs
- Backup testing, vendor risk assessments, and crisis simulations
Cloud Risk Mapping (AWS, Azure, GCP)
Cloud frameworks must address:
- Misconfiguration risks
- Shared responsibility and tenant isolation
- API security and vendor lock-in
- Compliance alignment using tools like CSPM and IaC scanning
AWS model: https://aws.amazon.com/compliance/shared-responsibility-model/
Azure framework: https://learn.microsoft.com/en-us/azure/architecture/framework/
GCP security: https://cloud.google.com/security/overview/
A sound IT and data risk framework unifies cybersecurity, privacy, continuity, and cloud oversight. It ensures operational resilience and compliance, while supporting digital growth.
Third-Party, Vendor, and Supply Chain Risk Management
Elevating Assurance Across External Relationships
As organisations increasingly rely on external vendors, suppliers, and service providers, managing third-party risk has become a board-level concern. These external relationships can expose firms to financial loss, regulatory breaches, operational disruption, and reputational damage—often through no fault of their own.
Why Third-Party Risk Is Now a Board-Level Concern
- Regulatory Pressure: Global regulations (e.g. GDPR, FCPA, FCA, CCPA) hold companies accountable for the actions of their suppliers.
- Operational Dependencies: Critical services—from cloud hosting to logistics—are outsourced, making third-party failures high-impact.
- Hidden Risks: Vendors may have opaque ownership structures, legal disputes, or ESG violations not visible in standard due diligence.
- Reputational Damage: Public exposure of unethical supplier practices (e.g. forced labour, data breaches) can quickly impact customer trust and investor confidence.
Boards are now expected to demand transparency, set risk tolerance thresholds, and receive regular reporting on third-party exposure.
Supplier, Vendor, and Procurement Risk Frameworks
Effective third-party risk frameworks address the full vendor lifecycle—from onboarding through to exit. Core components include:
- Risk Categorisation: Classify vendors by criticality, service type, data access, and operational impact.
- Due Diligence: Conduct identity checks, ownership screening, sanctions/adverse media checks, financial health analysis.
- Contractual Controls: Include clauses on liability, audits, termination, and compliance obligations.
- Ongoing Monitoring: Periodic reviews, KRI tracking, and incident alerts.
- Exit Planning: Predefined transition plans to mitigate service disruption.
Frameworks should align with ISO 27036, NIST 800-161, and other sector-specific supply chain guidance.
The 3-Layer Vendor Risk Toolkit
A Modern Operating Model to Build, Score, and Strengthen Third-Party Assurance
Layer 1: Strategic Risk Intelligence Tools
For Screening, Scoring, and Smart Decision-Making
Vendor Risk Scoring Engine
A weighted, customisable model that quantifies third-party exposure across:- Jurisdictional risk
- Sector-specific regulations
- Data criticality
- Financial resilience
Use case: Prioritise high-risk vendors for deeper diligence or board-level review.
OSINT-Based Deep Screening
Real-time alerts and enriched profiles using:- Public litigation records
- Media coverage
- Beneficial ownership tracing
Use case: Detect hidden relationships, reputational concerns, or red-flag triggers missed in standard onboarding.
ESG Risk Ratings & Reports
Third-party sustainability and ethical risk assessments based on:- Environmental policies
- Social responsibility and labour practices
- Governance standards (anti-bribery, transparency)
Use case: Align vendor selection with corporate ESG commitments.
Layer 2: Core Templates for Risk Operations
For Standardised Governance and Execution
| Template | Purpose |
|---|---|
| Risk Register Template | Log, categorise, and update vendor-specific risks systematically |
| Risk Heatmap | Visually rank risk exposure by severity and likelihood |
| Risk Appetite & Tolerance Chart | Clarify what levels of risk are acceptable by type, and where escalation is needed |
| Incident Reporting Template | Enable timely, uniform incident escalation and tracking |
Pro tip: Use shared folders or GRC platforms to keep these live and auditable.
Layer 3: Resilience and Control Frameworks
To Strengthen Post-Onboarding Risk Oversight
- Control Design Checklist: Verify that controls around data handling, access rights, compliance certifications, and third-party audits are clearly defined, implemented, and tested.
- Third-Party Risk Scorecard: An internal summary dashboard to track:
- Due diligence results
- Risk tier and approval status
- Renewal triggers and review cadence
- Business Impact Analysis (BIA): Estimate operational disruption, financial exposure, and regulatory implications if a vendor were to fail or breach.
How to Use This Toolkit Effectively
| When | Toolkit Component |
|---|---|
| Before onboarding | OSINT screening, ESG rating, risk scoring |
| During vendor assessment | Risk register, heatmap, BIA, risk appetite chart |
| Post-onboarding monitoring | Control checklist, scorecard, incident log |
The 4-Step Launch Pad for Risk Intelligence
A Structured Starter Kit to Operationalise Risk in 30 Days
Step 1: The 30-Day Quick-Start Roadmap
A one-month sprint to move from fragmented to structured risk operations
| Week | Action | Output |
|---|---|---|
| Week 1 | Define risk appetite & select 5–10 Key Risk Indicators (KRIs) | Board-approved appetite statement + KRI set |
| Week 2 | Build a rapid risk register & visualise top exposures with a heat map | Priority-ranked risk register + heatmap |
| Week 3 | Conduct a control gap analysis using a RACI matrix | Role-aligned mitigation accountability map |
| Week 4 | Develop an executive dashboard & set a reporting cadence | Risk dashboard + quarterly review rhythm |
Use Case: Ideal for new risk teams, internal audit leaders, or functions adopting enterprise risk principles for the first time.
Step 2: Self-Assessment Diagnostic Tool
A 5-minute internal check to assess where you stand
Create a simple Excel tool (or digital form) with scoring across 4 critical pillars:
| Pillar | Sample Question | Score (1–5) |
|---|---|---|
| Governance | Is there board ownership and escalation protocol? | |
| Data | Are risk indicators tracked in real time? | |
| Technology | Are controls automated or manual? | |
| Culture | Is risk awareness embedded across teams? |

Step 3: ROI Calculator
Convert your risk management effort into financial impact
| Input Fields | Example |
|---|---|
| Incident likelihood (%) | 40% |
| Expected impact if materialised | £250,000 |
| Mitigation investment | £25,000 |
Outputs:
- Estimated value-at-risk avoided
- Payback period in months
- Net savings over 12 months
Use Case: Justify investment in risk tools, training, or personnel.
Step 4: Risk Maturity Model & Progression Path
Benchmark your posture. Plan your next jump.
| Level | Characteristics | What to Fix Next |
|---|---|---|
| Level 1: Reactive | No framework, ad hoc incident response | Establish baseline risk register |
| Level 2: Basic | Static register, little board visibility | Add KRI dashboard + assign ownership |
| Level 3: Managed | Regular reviews, control tracking in place | Integrate OSINT and scenario planning |
| Level 4: Predictive | Intelligence-led, forward-looking, agile | Maintain automation + cross-functional reviews |
90-Day Jump Checklist
Finalise risk appetite
Launch top 10 KRIs
Assign risk owners (RACI)
Deploy dashboard to leadership
Schedule quarterly review cycle
FAQs on Risk Management Framework
What is a risk management framework (RMF)?
A risk management framework is a structured system that helps organisations identify, assess, treat, and monitor risks. It ensures risks are managed consistently across operations and decision-making levels.
What is the purpose of a risk management framework?
Its purpose is to support strategic decision-making, minimise uncertainty, enable regulatory compliance, and strengthen operational resilience through structured risk governance.
What are the key components of a risk management framework?
Core components include risk governance, risk identification, risk assessment and analysis, risk treatment, monitoring and review, communication and reporting, and alignment with business strategy.
What is the NIST Risk Management Framework (NIST RMF)?
The NIST RMF is a federal risk framework designed to manage information security and privacy risks in IT systems. It provides a six-step lifecycle covering everything from risk categorisation to continuous monitoring.
How many steps are there in the NIST Risk Management Framework?
The NIST RMF includes seven stages: Prepare, Categorise, Select, Implement, Assess, Authorise, and Monitor. Each step includes defined tasks, inputs, and outputs.
What is the ISO 31000 risk management framework?
ISO 31000 is a global standard offering principles-based guidance for enterprise risk management. It’s applicable to any organisation and promotes customisable, organisation-wide risk practices.
What is the COSO enterprise risk management framework?
The COSO ERM Framework includes 20 principles across five components and is focused on integrating risk with strategy, governance, and performance. It is widely used in financial services and corporate governance.
How do I build an operational risk management framework?
Start by identifying key operational risks, mapping internal controls, establishing KRIs, assigning ownership, and setting a schedule for ongoing review and incident escalation.
What is a third-party risk management framework?
It is a structured approach to assess, onboard, and monitor risks posed by vendors, suppliers, and external partners. It typically includes due diligence, risk scoring, contract controls, and continuous oversight.
What is a cybersecurity risk management framework?
Cybersecurity risk frameworks like NIST CSF or ISO 27001 help organisations manage digital threats. They include processes to identify vulnerabilities, protect assets, detect incidents, and respond effectively.
What are the five components of the ISO 31000 risk management process?
The ISO 31000 process includes risk identification, risk analysis, risk evaluation, risk treatment, and monitoring and review, with communication and reporting embedded throughout.
What is the difference between NIST RMF and NIST CSF?
NIST RMF is compliance-focused and control-heavy, suitable for federal systems, whereas NIST CSF is flexible and designed for broader cybersecurity risk management across public and private sectors.
How do you prioritise risks in a risk management framework?
Prioritisation is based on scoring each risk by likelihood and impact, adjusted by urgency (velocity) and business criticality, to focus mitigation efforts on the most significant threats.
What is a model risk management framework?
Model risk frameworks are used to govern the development, validation, and use of models, particularly in financial institutions, to reduce the risk of decision-making errors and regulatory breaches.
Why is it important to document a risk management framework?
Documentation enables consistent application, ensures audit-readiness, supports regulatory compliance, and communicates clearly how risks are managed across the business.



 WHAT WE OFFER
WHAT WE OFFER Risk Intelligence Case Studies:
Risk Intelligence Case Studies: Schedule a Call
Schedule a Call