

All you need to know about Third-Party Risk Management, TPRM Framework and a step by step practical guide to implement the TPRM Framework.
Third-party risk management (TPRM) is a structured approach that organisations use to identify, assess, mitigate, and continuously monitor risks associated with their external vendors, suppliers, contractors, and partners. As businesses increasingly rely on third parties to streamline operations, enhance efficiency, and reduce costs, managing associated risks becomes critical to safeguarding sensitive data, ensuring regulatory compliance, and maintaining business continuity.
A Third-Party Risk Management (TPRM) Framework is a structured, systematic approach that organisations use to identify, assess, mitigate, and monitor risks associated with third-party relationships. These third parties can include vendors, suppliers, contractors, service providers, and other external entities that interact with an organisation’s operations, data, or systems.
Given the increasing reliance on third-party services in today’s business landscape, a TPRM framework is essential to protect against financial, operational, cybersecurity, compliance, and reputational risks that may arise from these external partnerships.
A well-defined Third-Party Risk Management framework provides businesses with a systematic approach to mitigating potential risks introduced by third-party relationships.
Organisations depend on third parties for critical services such as cloud computing, data processing, supply chain logistics, and customer support. However, these relationships introduce inherent risks that can impact security, compliance, and business continuity.
A well-defined TPRM framework helps organisations:





A robust TPRM framework ensures that third-party risks are proactively managed rather than addressed reactively, reducing the likelihood of costly incidents such as data breaches, compliance violations, or financial losses.
An effective third-party risk management framework should be structured around key risk management principles to ensure thorough oversight. The following are its fundamental components:
By integrating these core elements, businesses can proactively manage third-party risks and ensure compliance with regulatory obligations.
A TPRM framework is essential for organisations across all industries, particularly those handling sensitive data, financial transactions, or critical infrastructure. It is especially crucial for:
Any business that engages with third-party service providers—whether for IT services, cloud hosting, supply chain management, or payroll processing—must have a robust third-party risk management framework in place.
Organisations that implement a strong TPRM framework can experience several advantages, including:
1. Enhanced Security and Data Protection
By enforcing stringent security measures, businesses can minimise vulnerabilities introduced by third-party vendors.
2. Regulatory Compliance Assurance
A structured framework ensures adherence to industry regulations such as GDPR, ISO 27001, NIST, and SOC 2, reducing legal liabilities.
3. Operational Resilience
An effective TPRM framework reduces the likelihood of operational disruptions caused by vendor failures.
4. Improved Decision-Making
With clear risk assessment metrics, organisations can make informed decisions regarding vendor selection and management.
5. Reputational Safeguarding
Maintaining a strong risk management culture reduces reputational damage from third-party misconduct.
Despite its benefits, implementing a TPRM framework presents challenges that organisations must address:
1. Managing Complex Supply Chains
With globalisation, organisations often engage with a vast network of third parties, making risk oversight complex.
2. Data Security and Privacy Risks
Third parties may have access to sensitive data, increasing the risk of cyber threats. Ensuring they comply with data protection laws is crucial.
3. Regulatory Variability
Different regions and industries have unique compliance requirements, making it difficult to standardise TPRM processes.
4. Resource Constraints
Many organisations lack dedicated teams and technology to monitor third-party risks effectively.
Overcoming these challenges requires strategic investments in technology, process automation, and governance frameworks.
1. Establish Governance and Accountability
2. Develop Comprehensive Risk Policies
3. Implement Risk Assessment Tools
4. Conduct Ongoing Due Diligence
5. Automate Risk Monitoring with Technology
6. Regularly Update and Review the TPRM Framework
To ensure regulatory adherence, businesses must comply with global third-party risk management standards, such as:
1. ISO 27001
A leading standard for information security management systems.
2. NIST (National Institute of Standards and Technology) Framework
A widely recognised framework for improving cybersecurity risk management.
3. GDPR (General Data Protection Regulation)
Applicable to organisations handling EU citizens’ data, enforcing strict third-party data processing controls.
4. SOC 2 (System and Organisation Controls 2)
A framework ensuring third parties maintain strong security and privacy practices.
Understanding and integrating these regulations into a TPRM framework can prevent legal and financial repercussions.
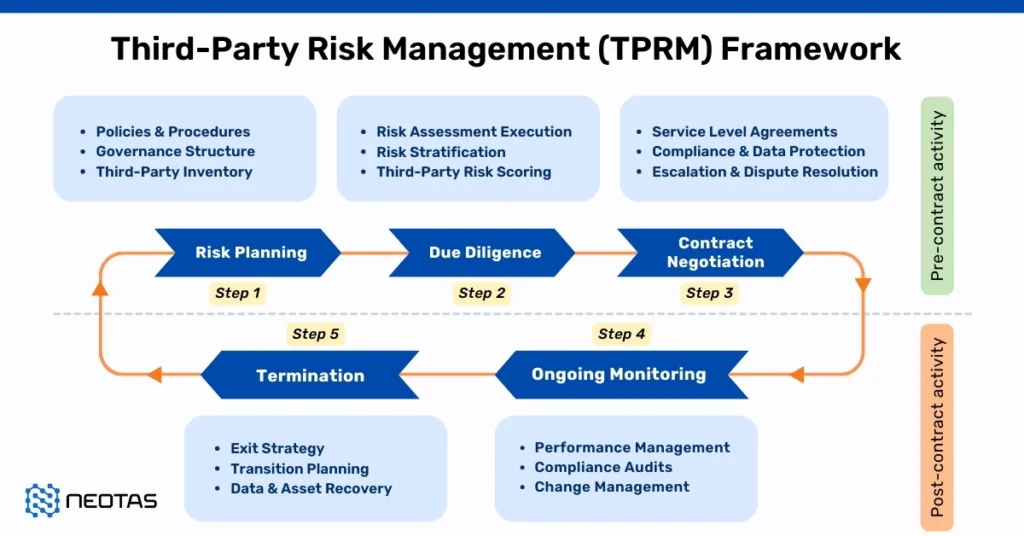
Implementing a Third-Party Risk Management (TPRM) Framework requires a structured approach to identify, assess, mitigate, and continuously monitor risks associated with third-party relationships. Below is a detailed breakdown of each implementation step to help organisations establish an effective TPRM framework.
Before engaging with third-party vendors, organisations must first define governance structures and establish clear policies that outline expectations, responsibilities, and compliance requirements.
Key Actions:



A third-party risk assessment is crucial before onboarding a vendor, ensuring that they meet security, financial, operational, and regulatory requirements.
Key Actions:








To mitigate third-party risks, it is crucial to incorporate legal and contractual protections when engaging with vendors.
Key Actions:




Risk assessments should not be a one-time event—continuous monitoring is essential to detect emerging risks and compliance violations throughout the vendor relationship.
Key Actions:




Despite preventive measures, security breaches, compliance violations, or service failures can still occur. A well-defined incident response plan ensures that the organisation can respond effectively to third-party-related incidents.
Key Actions:




Implementing a Third-Party Risk Management Framework requires a structured, proactive approach to identifying, assessing, and mitigating third-party risks while ensuring compliance with industry regulations. By following this five-step process, organisations can:




Next Steps:


By embedding third-party risk management best practices into your organisation’s operations, you can safeguard your business against vendor-related threats while maintaining strong and compliant third-party relationships.

For many organisations, third-party risk management stops at onboarding. Once a vendor is approved, the relationship moves forward on trust.

What’s the cost of missing these red flags?


The Neotas TPRM Framework helps businesses take a smarter approach by:



 Download the Whitepaper
Download the WhitepaperComprehensive Guide to Third-Party Risk Management (TPRM): Framework, Best Practices, and Step-by-Step Implementation
Neotas offers an innovative solution to businesses grappling with Third-Party Risk Management (TPRM). In an era of increasing outsourcing, TPRM has become pivotal, and Neotas recognises this need. Through our enhanced due diligence platform, businesses can efficiently track and evaluate vendors and contractors, ensuring adherence to security protocols in a cost-effective manner.
The Neotas platform automates the vendor onboarding process, streamlining the addition of new vendors with remarkable ease and speed.
Neotas provides a customisable dashboard, enabling businesses to proactively identify and address emerging risks. By consolidating vital vendor information, Neotas facilitates the seamless integration of risk management into existing Customer Relationship Management (CRM) and Supply Chain Management (SCM) systems, ultimately helping businesses maximise profits while minimising risk exposure.
If you’re curious about whether our third-party risk management solutions and services align with your organisation, don’t hesitate to schedule a call. We’re here to help you make informed decisions tailored to your needs.
A Third-Party Risk Management Framework (TPRM Framework) is a structured approach to identifying, assessing, mitigating, and monitoring third-party risks across an organisation’s supply chain, vendors, and service providers.
Businesses today rely on third-party vendors, cloud service providers, and external suppliers to enhance operations. However, this also introduces third-party security risks, including data breaches, vendor compliance failures, supply chain disruptions, and operational inefficiencies. A well-structured TPRM framework ensures businesses can proactively mitigate vendor security risks, comply with industry regulations such as ISO 27001, SOC 2, GDPR, and NIST 800-161, and enhance operational resilience.




Implementing a robust Third-Party Risk Management Framework strengthens vendor risk oversight, enhances data security frameworks, and ensures third-party contract compliance.
A TPRM Framework is critical for cybersecurity and regulatory compliance because it helps businesses:




A comprehensive TPRM Framework helps businesses manage multiple third-party risk categories, including:





A TPRM Framework ensures businesses establish a vendor security governance framework to reduce third-party risks effectively.
A vendor risk assessment is a critical part of any Third-Party Risk Management Framework and involves:




A comprehensive vendor risk assessment ensures businesses select trusted, compliant, and secure third-party vendors.
To ensure a successful TPRM implementation, follow these best practices:





A well-structured TPRM Framework enhances third-party risk reduction strategies and strengthens supply chain security.
A Third-Party Risk Management Framework ensures compliance with ISO 27001, NIST, and GDPR by:



A strong TPRM compliance framework reduces regulatory risks and ensures data security resilience.
A Third-Party Risk Management Framework (TPRM Framework) is essential for third-party vendor risk mitigation by ensuring:





By integrating these third-party risk mitigation strategies, organisations can secure vendor ecosystems, enhance compliance oversight, and reduce financial and reputational risks.
The third-party risk management lifecycle consists of six critical phases:
 Vendor Onboarding & Risk Assessment
Vendor Onboarding & Risk Assessment Third-Party Risk Classification
Third-Party Risk Classification Risk Mitigation & Security Controls
Risk Mitigation & Security Controls Contractual Risk Governance & Compliance
Contractual Risk Governance & Compliance Continuous Vendor Risk Monitoring
Continuous Vendor Risk Monitoring Third-Party Vendor Offboarding & Data Protection
Third-Party Vendor Offboarding & Data ProtectionA structured TPRM lifecycle enhances third-party oversight, mitigates supply chain risks, and strengthens enterprise security posture.
A TPRM Framework protects against the following third-party data security risks:





A third-party security governance framework ensures vendors meet cybersecurity best practices, encryption standards, and third-party risk assessment guidelines.
A comprehensive Third-Party Risk Management Framework must align with key regulatory and compliance mandates, including:





Ensuring vendors comply with global regulatory requirements strengthens business resilience, data security frameworks, and compliance auditing processes.
Automated third-party risk monitoring tools enhance TPRM compliance framework implementation by:




Top third-party risk monitoring tools include OneTrust, Prevalent, and UpGuard, which offer automated vendor risk scoring models and compliance tracking.
A third-party incident response plan ensures businesses can contain, investigate, and remediate vendor security breaches. Key steps include:




A structured TPRM incident response plan minimises third-party security risks and ensures business continuity after vendor-related breaches.
To measure the success of a Third-Party Risk Management Framework, businesses should track:





Effective third-party risk evaluation models provide data-driven insights into TPRM framework performance.
To future-proof third-party risk management strategies, businesses must:




By leveraging advanced cybersecurity measures and regulatory risk governance frameworks, organisations can create a future-ready Third-Party Risk Management Framework.
Choosing the right Third-Party Risk Management Framework (TPRM Framework) depends on industry requirements, regulatory compliance, and organisational risk tolerance. The key factors to consider include:
 Regulatory & Compliance Requirements
Regulatory & Compliance Requirements Risk Domains & Scope of the TPRM Framework
Risk Domains & Scope of the TPRM Framework Third-Party Risk Mitigation Strategies
Third-Party Risk Mitigation Strategies Technology Integration & Automation
Technology Integration & Automation Scalability & Customisation
Scalability & CustomisationA comprehensive TPRM Framework ensures businesses can select, assess, and monitor third-party vendors effectively while minimising cybersecurity vulnerabilities and regulatory risks.
A risk management framework consists of five essential components that help businesses manage third-party vendor risks, cybersecurity risks, and operational threats:





A well-structured risk management framework enhances business resilience, vendor security governance, and regulatory compliance.
The 7-step Risk Management Framework (RMF) follows a structured approach to assessing, mitigating, and monitoring third-party vendor risks:







A risk management framework following these seven steps strengthens vendor oversight and security governance.
A TPRM System (Third-Party Risk Management System) is a technology-driven platform that enables businesses to automate third-party risk assessments, monitor vendor security risks, and ensure regulatory compliance.




A robust TPRM System enables organisations to proactively manage third-party risks, prevent security incidents, and strengthen vendor compliance frameworks.
To build a Third-Party Risk Management Program, follow these structured steps:
 Establish TPRM Governance & Policies
Establish TPRM Governance & Policies Implement Vendor Risk Assessment Frameworks
Implement Vendor Risk Assessment Frameworks Deploy Third-Party Risk Monitoring Tools
Deploy Third-Party Risk Monitoring Tools Develop Incident Response & Risk Mitigation Strategies
Develop Incident Response & Risk Mitigation Strategies Conduct Continuous Vendor Audits & Compliance Reviews
Conduct Continuous Vendor Audits & Compliance ReviewsA well-structured TPRM program enhances third-party risk reduction strategies, regulatory compliance alignment, and vendor security resilience.
TPRM (Third-Party Risk Management) and GRC (Governance, Risk, and Compliance) frameworks both focus on risk oversight, but they serve distinct functions:



Businesses integrating both TPRM and GRC frameworks enhance enterprise-wide security, compliance tracking, and third-party vendor risk mitigation.
Protect your business from third-party risks—Strengthen your risk management strategy with Neotas TPRM Services
Neotas is an Enhanced Due Diligence Platform that leverages AI to join the dots between Corporate Records, Adverse Media and Open Source Intelligence (OSINT).
Schedule a Call or Book a Demo of Third-Party Risk Management Solutions

Neotas Enhanced Due Diligence covers 600Bn+ Archived web pages, 1.8Bn+ court records, 198M+ Corporate records, Global Social Media platforms, and more than 40,000 Media sources from over 100 countries to help you screen & manage risks.
risk management framework
rmf
third party risk management
tprm
nist risk management framework
nist rmf
third-party risk management
tprm meaning
it security risk management
rmf steps
third party risk
information security risk management
3rd party risk management
security risk management
cyber security risk management
risk framework
what is rmf
third party vendor
risk assessment framework
nist assessment
information risk management
what is tprm
security and risk management
cyber security and risk management
nist controls
cybersecurity risk management framework
risk management framework steps
rmf process
risiko management
risk management frameworks
third party vendor management
it risk management framework
nist risk assessment
t&r frameworks
3rd party vendor
rmf framework
risk monitoring
cyber risk management framework
third party risk management framework
vendor risk management program
serlect risks
third party management
third party vendor risk management
what is third party risk management
rmf cybersecurity
tprm assessment
7 steps of rmf
what is a third party vendor
information security and risk management
risk governance framework
third party risk compliance
third party compliance
third party risk software
nist rmf steps
3rd party vendor risk management
risk management framework (rmf)
7 steps of risk management process with example
third party risk assessments
third party risk management program
nist frameworks
third party risk management solution
nist rmf framework
rmf compliance
third party risk management policy
nist control framework
nist third party risk management
rmf nist
third party vendors
rmf risk management framework
third party security
third party access management
rmf cycle
third party risks
risk management framework nist
risk management controls
vendor risk management framework
risk management guide
third party cyber risk assessment
tprm framework
third party risk management process
nist compliance framework
third party cyber risk
information security framework
third-party risk management framework
third party risk management solutions
third party cyber risk management
risk & security management
risk and security management
nist rmf vs csf
third party risk assessment template
information security risk management program
third party threat
third party risk monitoring
third party risk management services
third party risk management technology
risk management framework examples
third party risk solutions
cyber risk framework
nist risk assessment framework
tprm software
risk management framework example
tprm program
what does tprm stand for
information security risk management framework
it third party risk management
business risk management framework
3rd party risk
third party management system
it security and risk management
tprm risk management
security risk model
risk assessment management system
what is tprm in cyber security
framework risk management
third party supplier management
third-party risk
risk management information security
it risk management system
third party risk management assessment
tprm process
nist risk management
types of risk management frameworks
vanta frameworks
importance of third party risk management
information security risk management process
third party risk management vendors
third party risk management regulations
3rd party compliance
rmf acronym
compliance risk management framework
cyber security risk management framework
third party security assessment
cyber security third party risk management
risk management in information security
nist risk assessment methodology
framework for risk management
risque management
third party risk management best practices
risk frameworks
3rd party vendor management
nist cybersecurity controls
third-party risk management examples
nist risk framework
infosec risk management
compliance risk assessment framework
security risk management plan
tprm solutions
supplier risk management program
risk management standards
3rd party management
tprm lifecycle
third party assessment
nist vendor management
third party vendor monitoring
rmf cyber
managing third party risk
third party risk cyber security
third party security management
cybersecurity risk assessment framework
third party risk governance
third party vendor risk assessment example
nist risk management framework steps
third party management risk
third party governance
nist csf vs rmf
shared assessments sig
vendor risk management best practices
risk management security
nist risk matrix
nist risk management framework 800-53
rmf 7 steps
it risk assessment framework
tprm platforms
nist cybersecurity risk assessment
third party vendor definition
7 steps of risk management process
risk analysis framework
risk security management
third party risk assessment framework
3rd party security assessment
security risk management program
nist cybersecurity risk assessment template
regulatory risk management framework
third party compliance management
third-party cyber risk management
third party risk management examples
rmf process steps
third party risk definition
nist rmf 7 steps
third party risk management system
3rd party vendor risk assessment
third party risk assessment process
third party compliance risk management
what is third party management
tprm risk assessment
nist cyber risk scoring
what is third-party risk management
tprm compliance
risk assessment frameworks
third party operational risk
threat management framework
management frameworks
risk managment framework
technology risk management framework
third party vendor risks
how to mitigate third party risk
what is third party risk
third party risk management workflow
third-party vendor
risk management framework cybersecurity
third party risk management compliance
higher education tprm
third party vendor risk
nist risk management framework (rmf)
tprm cybersecurity
cyber risk frameworks
technology risk framework
risk management frameworks list
risk management and security
how to manage third party risk
tprm policy
third party risk management guide
3rd party monitoring
third-party vendor risk management
cyber security risk assessment framework
security risk management framework
third-party management
go/tprm
rmf lifecycle
third party risk management as a service
manage third party risk
rmf tools
nist management framework
digital risk management framework
nist rmf 800-53
what is nist rmf
third party risk management programs
supplier risk management framework
rmf security controls
cyber risk assessment framework
third party risk management standards
third-party risk management best practices
third party information security
health tprm
third party cyber security risk management
sig shared assessments
cyber security third party risk
nist csf risk assessment
risk mitigation framework
cyber rmf
managing third party vendors
third-party risk management program
rmf nist 800-53
why is third party risk management important
it vendor management framework
third party risk management definition
third-party vendor examples
third party risk management controls
third party risk manager
rmf security
robust risk management program
3rd party risk management framework
risk management guidelines
rmf requirements
cyber security risk framework
3rd party risk assessment process
3rd party cyber risk
nist grc
third party risk assessment methodology
third-party risk examples
third party exposure
nist risk
third party risk management framework nist
nist risk management process
risk management framework rmf
nist 800-53 rmf
third party supplier risk
3rd party security risk assessment
nist third party risk management framework
security & risk management
vendor risk assessment framework
information technology risk management framework
risk based cybersecurity framework
risk assessment nist
cybersecurity rmf
cybersecurity third party risk management
third party risk reporting
risk management and compliance framework
federal tprm
what is third party risk assessment
what is rmf?
third party information security risk management
nist risk management framework template
third party risk mitigation
third party security risk assessment
third party security risk
cyber security rmf
securities risk management
third party compliance risk
nist vendor risk management
effective third party risk management
rmf cyber security
third party security risk management
third-party risk management market
risk management framwork
third party evaluation
tprm security
risk control framework
nist methodology
what is 3rd party risk management
nist tprm
3rd party assessment
third-party cyber risk
enterprise vendor risk management program
nist rmf controls
third party risk policy
nist 800 framework
information security compliance framework
risk information management
third party risk management tprm
third-party risk management process
nist cybersecurity risk management framework
third party risk regulations
nist rmf certification
third party risk management framework pdf
tprm best practices
risk assessment cybersecurity framework
cybersecurity risk management frameworks
what is third party vendor
3rd party security
third party risk management policy example
third party procurement
third party risk management audit
third party risk statistics
nist 800 rmf
third party risk management process flow
risk and control framework
risk management nist
third party relationship management
isms risk management
3rd party risk assessments
third party governance and risk management
which of the following poses a higher risk to ensuring business continuity?
third party management policy
third party compliance program
third-party risk management lifecycle
nist model
nist steps
tprm life cycle
third-party vendor management
risk framework management
thirdparty risk management
the risk management framework
it risk framework
nist risk assessment process
third party risk assessment best practices
third party risk management cyber security
third party risk due diligence
third party risk managment
third party managers
nist risk management framework 800 53
third-party risk assessment framework
third party risk management ongoing monitoring
cyber risk management frameworks
third party vendor security
what is nist risk management framework
non profit tprm
nist rmf process
nist rmf training
third party risk management frameworks
nist 800-53 risk management framework
third party risk management program template
the nist risk management approach includes all but which of the following elements?
nist 800-53 risk assessment
nist 800-53 vendor management
nist controls framework
third-party risk management policy
nist risk scoring matrix
what is third party vendor management
third party performance management
nist 800-53 risk assessment template
third-party risk management process flow
third party service provider risk assessment
list of nist frameworks
nist risk assessment tool
third party vendor management security best practices
rmf 800-53
third party risk management policies and procedures
third-party risk assessment example
rmf it
third party management process
third party management framework
nist rfm
nist cyber risk management framework
state & local tprm
it risk management frameworks
risk assessment framework nist
computer risk management
nist cyber risk assessment
third party information security assessment
third party risk management framework template
nist framework controls
third-party compliance
third party risk management checklist
third party risk examples
risk assessment controls
what are some things that are generally included on a third party security assessment report
third party risk management financial services
third party risk framework
third party vendor management program
information security management framework
what are some things that are generally included on a third party security assessment report?
risk models and frameworks
information risk management framework
nist risk assessments
nist third-party risk management framework
guidance for managing third party risk
rmf support
third-party risks examples
nist risk management framework training
third party threats
vendor risk management process flow
tprm services
third party risk assurance
rmf step
rmf documentation
third-party vendor risk assessment example
nist framework risk assessment
third-party risk management regulations
it risk assessment frameworks
third party risk scoring
risk and controls framework
third-party management best practices
security risk frameworks
risk management framework
rmf
third party risk management
tprm
nist risk management framework
nist rmf
third-party risk management
tprm meaning
it security risk management
rmf steps
third party risk
information security risk management
3rd party risk management
security risk management
cyber security risk management
risk framework
what is rmf
third party vendor
risk assessment framework
nist assessment
information risk management
what is tprm
security and risk management
cyber security and risk management
nist controls
cybersecurity risk management framework
risk management framework steps
rmf process
risiko management
risk management frameworks
third party vendor management
it risk management framework
nist risk assessment
t&r frameworks
3rd party vendor
rmf framework
risk monitoring
cyber risk management framework
third party risk management framework
vendor risk management program
serlect risks
third party management
third party vendor risk management
what is third party risk management
rmf cybersecurity
tprm assessment
7 steps of rmf
what is a third party vendor
information security and risk management
risk governance framework
third party risk compliance
third party compliance
third party risk software
nist rmf steps
3rd party vendor risk management
risk management framework (rmf)
7 steps of risk management process with example
third party risk assessments
third party risk management program
nist frameworks
third party risk management solution
nist rmf framework
rmf compliance
third party risk management policy
nist control framework
nist third party risk management
rmf nist
third party vendors
rmf risk management framework
third party security
third party access management
rmf cycle
third party risks
risk management framework nist
risk management controls
vendor risk management framework
risk management guide
third party cyber risk assessment
tprm framework
third party risk management process
nist compliance framework
third party cyber risk
information security framework
third-party risk management framework
third party risk management solutions
third party cyber risk management
risk & security management
risk and security management
nist rmf vs csf
third party risk assessment template
information security risk management program
third party threat
third party risk monitoring
third party risk management services
third party risk management technology
risk management framework examples
third party risk solutions
cyber risk framework
nist risk assessment framework
tprm software
risk management framework example
tprm program
what does tprm stand for
information security risk management framework
it third party risk management
business risk management framework
3rd party risk
third party management system
it security and risk management
tprm risk management
security risk model
risk assessment management system
what is tprm in cyber security
framework risk management
third party supplier management
third-party risk
risk management information security
it risk management system
third party risk management assessment
tprm process
nist risk management
types of risk management frameworks
vanta frameworks
importance of third party risk management
information security risk management process
third party risk management vendors
third party risk management regulations
3rd party compliance
rmf acronym
compliance risk management framework
cyber security risk management framework
third party security assessment
cyber security third party risk management
risk management in information security
nist risk assessment methodology
framework for risk management
risque management
third party risk management best practices
risk frameworks
3rd party vendor management
nist cybersecurity controls
third-party risk management examples
nist risk framework
infosec risk management
compliance risk assessment framework
security risk management plan
tprm solutions
supplier risk management program
risk management standards
3rd party management
tprm lifecycle
third party assessment
nist vendor management
third party vendor monitoring
rmf cyber
managing third party risk
third party risk cyber security
third party security management
cybersecurity risk assessment framework
third party risk governance
third party vendor risk assessment example
nist risk management framework steps
third party management risk
third party governance
nist csf vs rmf
shared assessments sig
vendor risk management best practices
risk management security
nist risk matrix
nist risk management framework 800-53
rmf 7 steps
it risk assessment framework
tprm platforms
nist cybersecurity risk assessment
third party vendor definition
7 steps of risk management process
risk analysis framework
risk security management
third party risk assessment framework
3rd party security assessment
security risk management program
nist cybersecurity risk assessment template
regulatory risk management framework
third party compliance management
third-party cyber risk management
third party risk management examples
rmf process steps
third party risk definition
nist rmf 7 steps
third party risk management system
3rd party vendor risk assessment
third party risk assessment process
third party compliance risk management
what is third party management
tprm risk assessment
nist cyber risk scoring
what is third-party risk management
tprm compliance
risk assessment frameworks
third party operational risk
threat management framework
management frameworks
risk managment framework
technology risk management framework
third party vendor risks
how to mitigate third party risk
what is third party risk
third party risk management workflow
third-party vendor
risk management framework cybersecurity
third party risk management compliance
higher education tprm
third party vendor risk
nist risk management framework (rmf)
tprm cybersecurity
cyber risk frameworks
technology risk framework
risk management frameworks list
risk management and security
how to manage third party risk
tprm policy
third party risk management guide
3rd party monitoring
third-party vendor risk management
cyber security risk assessment framework
security risk management framework
third-party management
go/tprm
rmf lifecycle
third party risk management as a service
manage third party risk
rmf tools
nist management framework
digital risk management framework
nist rmf 800-53
what is nist rmf
third party risk management programs
supplier risk management framework
rmf security controls
cyber risk assessment framework
third party risk management standards
third-party risk management best practices
third party information security
health tprm
third party cyber security risk management
sig shared assessments
cyber security third party risk
nist csf risk assessment
risk mitigation framework
cyber rmf
managing third party vendors
third-party risk management program
rmf nist 800-53
why is third party risk management important
it vendor management framework
third party risk management definition
third-party vendor examples
third party risk management controls
third party risk manager
rmf security
robust risk management program
3rd party risk management framework
risk management guidelines
rmf requirements
cyber security risk framework
3rd party risk assessment process
3rd party cyber risk
nist grc
third party risk assessment methodology
third-party risk examples
third party exposure
nist risk
third party risk management framework nist
nist risk management process
risk management framework rmf
nist 800-53 rmf
third party supplier risk
3rd party security risk assessment
nist third party risk management framework
security & risk management
vendor risk assessment framework
information technology risk management framework
risk based cybersecurity framework
risk assessment nist
cybersecurity rmf
cybersecurity third party risk management
third party risk reporting
risk management and compliance framework
federal tprm
what is third party risk assessment
what is rmf?
third party information security risk management
nist risk management framework template
third party risk mitigation
third party security risk assessment
third party security risk
cyber security rmf
securities risk management
third party compliance risk
nist vendor risk management
effective third party risk management
rmf cyber security
third party security risk management
third-party risk management market
risk management framwork
third party evaluation
tprm security
risk control framework
nist methodology
what is 3rd party risk management
nist tprm
3rd party assessment
third-party cyber risk
enterprise vendor risk management program
nist rmf controls
third party risk policy
nist 800 framework
information security compliance framework
risk information management
third party risk management tprm
third-party risk management process
nist cybersecurity risk management framework
third party risk regulations
nist rmf certification
third party risk management framework pdf
tprm best practices
risk assessment cybersecurity framework
cybersecurity risk management frameworks
what is third party vendor
3rd party security
third party risk management policy example
third party procurement
third party risk management audit
third party risk statistics
nist 800 rmf
third party risk management process flow
risk and control framework
risk management nist
third party relationship management
isms risk management
3rd party risk assessments
third party governance and risk management
which of the following poses a higher risk to ensuring business continuity?
third party management policy
third party compliance program
third-party risk management lifecycle
nist model
nist steps
tprm life cycle
third-party vendor management
risk framework management
thirdparty risk management
the risk management framework
it risk framework
nist risk assessment process
third party risk assessment best practices
third party risk management cyber security
third party risk due diligence
third party risk managment
third party managers
nist risk management framework 800 53
third-party risk assessment framework
third party risk management ongoing monitoring
cyber risk management frameworks
third party vendor security
what is nist risk management framework
non profit tprm
nist rmf process
nist rmf training
third party risk management frameworks
nist 800-53 risk management framework
third party risk management program template
the nist risk management approach includes all but which of the following elements?
nist 800-53 risk assessment
nist 800-53 vendor management
nist controls framework
third-party risk management policy
nist risk scoring matrix
what is third party vendor management
third party performance management
nist 800-53 risk assessment template
third-party risk management process flow
third party service provider risk assessment
list of nist frameworks
nist risk assessment tool
third party vendor management security best practices
rmf 800-53
third party risk management policies and procedures
third-party risk assessment example
rmf it
third party management process
third party management framework
nist rfm
nist cyber risk management framework
state & local tprm
it risk management frameworks
risk assessment framework nist
computer risk management
nist cyber risk assessment
third party information security assessment
third party risk management framework template
nist framework controls
third-party compliance
third party risk management checklist
third party risk examples
risk assessment controls
what are some things that are generally included on a third party security assessment report
third party risk management financial services
third party risk framework
third party vendor management program
information security management framework
what are some things that are generally included on a third party security assessment report?
risk models and frameworks
information risk management framework
nist risk assessments
nist third-party risk management framework
guidance for managing third party risk
rmf support
third-party risks examples
nist risk management framework training
third party threats
vendor risk management process flow
tprm services
third party risk assurance
rmf step
rmf documentation
third-party vendor risk assessment example
nist framework risk assessment
third-party risk management regulations
it risk assessment frameworks
third party risk scoring
risk and controls framework
third-party management best practices
security risk frameworks
risk management framework
rmf
third party risk management
tprm
nist risk management framework
nist rmf
third-party risk management
tprm meaning
it security risk management
rmf steps
third party risk
information security risk management
3rd party risk management
security risk management
cyber security risk management
risk framework
what is rmf
third party vendor
risk assessment framework
nist assessment
information risk management
what is tprm
security and risk management
cyber security and risk management
nist controls
cybersecurity risk management framework
risk management framework steps
rmf process
risiko management
risk management frameworks
third party vendor management
it risk management framework
nist risk assessment
t&r frameworks
3rd party vendor
rmf framework
risk monitoring
cyber risk management framework
third party risk management framework
vendor risk management program
serlect risks
third party management
third party vendor risk management
what is third party risk management
rmf cybersecurity
tprm assessment
7 steps of rmf
what is a third party vendor
information security and risk management
risk governance framework
third party risk compliance
third party compliance
third party risk software
nist rmf steps
3rd party vendor risk management
risk management framework (rmf)
7 steps of risk management process with example
third party risk assessments
third party risk management program
nist frameworks
third party risk management solution
nist rmf framework
rmf compliance
third party risk management policy
nist control framework
nist third party risk management
rmf nist
third party vendors
rmf risk management framework
third party security
third party access management
rmf cycle
third party risks
risk management framework nist
risk management controls
vendor risk management framework
risk management guide
third party cyber risk assessment
tprm framework
third party risk management process
nist compliance framework
third party cyber risk
information security framework
third-party risk management framework
third party risk management solutions
third party cyber risk management
risk & security management
risk and security management
nist rmf vs csf
third party risk assessment template
information security risk management program
third party threat
third party risk monitoring
third party risk management services
third party risk management technology
risk management framework examples
third party risk solutions
cyber risk framework
nist risk assessment framework
tprm software
risk management framework example
tprm program
what does tprm stand for
information security risk management framework
it third party risk management
business risk management framework
3rd party risk
third party management system
it security and risk management
tprm risk management
security risk model
risk assessment management system
what is tprm in cyber security
framework risk management
third party supplier management
third-party risk
risk management information security
it risk management system
third party risk management assessment
tprm process
nist risk management
types of risk management frameworks
vanta frameworks
importance of third party risk management
information security risk management process
third party risk management vendors
third party risk management regulations
3rd party compliance
rmf acronym
compliance risk management framework
cyber security risk management framework
third party security assessment
cyber security third party risk management
risk management in information security
nist risk assessment methodology
framework for risk management
risque management
third party risk management best practices
risk frameworks
3rd party vendor management
nist cybersecurity controls
third-party risk management examples
nist risk framework
infosec risk management
compliance risk assessment framework
security risk management plan
tprm solutions
supplier risk management program
risk management standards
3rd party management
tprm lifecycle
third party assessment
nist vendor management
third party vendor monitoring
rmf cyber
managing third party risk
third party risk cyber security
third party security management
cybersecurity risk assessment framework
third party risk governance
third party vendor risk assessment example
nist risk management framework steps
third party management risk
third party governance
nist csf vs rmf
shared assessments sig
vendor risk management best practices
risk management security
nist risk matrix
nist risk management framework 800-53
rmf 7 steps
it risk assessment framework
tprm platforms
nist cybersecurity risk assessment
third party vendor definition
7 steps of risk management process
risk analysis framework
risk security management
third party risk assessment framework
3rd party security assessment
security risk management program
nist cybersecurity risk assessment template
regulatory risk management framework
third party compliance management
third-party cyber risk management
third party risk management examples
rmf process steps
third party risk definition
nist rmf 7 steps
third party risk management system
3rd party vendor risk assessment
third party risk assessment process
third party compliance risk management
what is third party management
tprm risk assessment
nist cyber risk scoring
what is third-party risk management
tprm compliance
risk assessment frameworks
third party operational risk
threat management framework
management frameworks
risk managment framework
technology risk management framework
third party vendor risks
how to mitigate third party risk
what is third party risk
third party risk management workflow
third-party vendor
risk management framework cybersecurity
third party risk management compliance
higher education tprm
third party vendor risk
nist risk management framework (rmf)
tprm cybersecurity
cyber risk frameworks
technology risk framework
risk management frameworks list
risk management and security
how to manage third party risk
tprm policy
third party risk management guide
3rd party monitoring
third-party vendor risk management
cyber security risk assessment framework
security risk management framework
third-party management
go/tprm
rmf lifecycle
third party risk management as a service
manage third party risk
rmf tools
nist management framework
digital risk management framework
nist rmf 800-53
what is nist rmf
third party risk management programs
supplier risk management framework
rmf security controls
cyber risk assessment framework
third party risk management standards
third-party risk management best practices
third party information security
health tprm
third party cyber security risk management
sig shared assessments
cyber security third party risk
nist csf risk assessment
risk mitigation framework
cyber rmf
managing third party vendors
third-party risk management program
rmf nist 800-53
why is third party risk management important
it vendor management framework
third party risk management definition
third-party vendor examples
third party risk management controls
third party risk manager
rmf security
robust risk management program
3rd party risk management framework
risk management guidelines
rmf requirements
cyber security risk framework
3rd party risk assessment process
3rd party cyber risk
nist grc
third party risk assessment methodology
third-party risk examples
third party exposure
nist risk
third party risk management framework nist
nist risk management process
risk management framework rmf
nist 800-53 rmf
third party supplier risk
3rd party security risk assessment
nist third party risk management framework
security & risk management
vendor risk assessment framework
information technology risk management framework
risk based cybersecurity framework
risk assessment nist
cybersecurity rmf
cybersecurity third party risk management
third party risk reporting
risk management and compliance framework
federal tprm
what is third party risk assessment
what is rmf?
third party information security risk management
nist risk management framework template
third party risk mitigation
third party security risk assessment
third party security risk
cyber security rmf
securities risk management
third party compliance risk
nist vendor risk management
effective third party risk management
rmf cyber security
third party security risk management
third-party risk management market
risk management framwork
third party evaluation
tprm security
risk control framework
nist methodology
what is 3rd party risk management
nist tprm
3rd party assessment
third-party cyber risk
enterprise vendor risk management program
nist rmf controls
third party risk policy
nist 800 framework
information security compliance framework
risk information management
third party risk management tprm
third-party risk management process
nist cybersecurity risk management framework
third party risk regulations
nist rmf certification
third party risk management framework pdf
tprm best practices
risk assessment cybersecurity framework
cybersecurity risk management frameworks
what is third party vendor
3rd party security
third party risk management policy example
third party procurement
third party risk management audit
third party risk statistics
nist 800 rmf
third party risk management process flow
risk and control framework
risk management nist
third party relationship management
isms risk management
3rd party risk assessments
third party governance and risk management
which of the following poses a higher risk to ensuring business continuity?
third party management policy
third party compliance program
third-party risk management lifecycle
nist model
nist steps
tprm life cycle
third-party vendor management
risk framework management
thirdparty risk management
the risk management framework
it risk framework
nist risk assessment process
third party risk assessment best practices
third party risk management cyber security
third party risk due diligence
third party risk managment
third party managers
nist risk management framework 800 53
third-party risk assessment framework
third party risk management ongoing monitoring
cyber risk management frameworks
third party vendor security
what is nist risk management framework
non profit tprm
nist rmf process
nist rmf training
third party risk management frameworks
nist 800-53 risk management framework
third party risk management program template
the nist risk management approach includes all but which of the following elements?
nist 800-53 risk assessment
nist 800-53 vendor management
nist controls framework
third-party risk management policy
nist risk scoring matrix
what is third party vendor management
third party performance management
nist 800-53 risk assessment template
third-party risk management process flow
third party service provider risk assessment
list of nist frameworks
nist risk assessment tool
third party vendor management security best practices
rmf 800-53
third party risk management policies and procedures
third-party risk assessment example
rmf it
third party management process
third party management framework
nist rfm
nist cyber risk management framework
state & local tprm
it risk management frameworks
risk assessment framework nist
computer risk management
nist cyber risk assessment
third party information security assessment
third party risk management framework template
nist framework controls
third-party compliance
third party risk management checklist
third party risk examples
risk assessment controls
what are some things that are generally included on a third party security assessment report
third party risk management financial services
third party risk framework
third party vendor management program
information security management framework
what are some things that are generally included on a third party security assessment report?
risk models and frameworks
information risk management framework
nist risk assessments
nist third-party risk management framework
guidance for managing third party risk
rmf support
third-party risks examples
nist risk management framework training
third party threats
vendor risk management process flow
tprm services
third party risk assurance
rmf step
rmf documentation
third-party vendor risk assessment example
nist framework risk assessment
third-party risk management regulations
it risk assessment frameworks
third party risk scoring
risk and controls framework
third-party management best practices
security risk frameworks
risk management framework
rmf
third party risk management
tprm
nist risk management framework
nist rmf
third-party risk management
tprm meaning
it security risk management
rmf steps
third party risk
information security risk management
3rd party risk management
security risk management
cyber security risk management
risk framework
what is rmf
third party vendor
risk assessment framework
nist assessment
information risk management
what is tprm
security and risk management
cyber security and risk management
nist controls
cybersecurity risk management framework
risk management framework steps
rmf process
risiko management
risk management frameworks
third party vendor management
it risk management framework
nist risk assessment
t&r frameworks
3rd party vendor
rmf framework
risk monitoring
cyber risk management framework
third party risk management framework
vendor risk management program
serlect risks
third party management
third party vendor risk management
what is third party risk management
rmf cybersecurity
tprm assessment
7 steps of rmf
what is a third party vendor
information security and risk management
risk governance framework
third party risk compliance
third party compliance
third party risk software
nist rmf steps
3rd party vendor risk management
risk management framework (rmf)
7 steps of risk management process with example
third party risk assessments
third party risk management program
nist frameworks
third party risk management solution
nist rmf framework
rmf compliance
third party risk management policy
nist control framework
nist third party risk management
rmf nist
third party vendors
rmf risk management framework
third party security
third party access management
rmf cycle
third party risks
risk management framework nist
risk management controls
vendor risk management framework
risk management guide
third party cyber risk assessment
tprm framework
third party risk management process
nist compliance framework
third party cyber risk
information security framework
third-party risk management framework
third party risk management solutions
third party cyber risk management
risk & security management
risk and security management
nist rmf vs csf
third party risk assessment template
information security risk management program
third party threat
third party risk monitoring
third party risk management services
third party risk management technology
risk management framework examples
third party risk solutions
cyber risk framework
nist risk assessment framework
tprm software
risk management framework example
tprm program
what does tprm stand for
information security risk management framework
it third party risk management
business risk management framework
3rd party risk
third party management system
it security and risk management
tprm risk management
security risk model
risk assessment management system
what is tprm in cyber security
framework risk management
third party supplier management
third-party risk
risk management information security
it risk management system
third party risk management assessment
tprm process
nist risk management
types of risk management frameworks
vanta frameworks
importance of third party risk management
information security risk management process
third party risk management vendors
third party risk management regulations
3rd party compliance
rmf acronym
compliance risk management framework
cyber security risk management framework
third party security assessment
cyber security third party risk management
risk management in information security
nist risk assessment methodology
framework for risk management
risque management
third party risk management best practices
risk frameworks
3rd party vendor management
nist cybersecurity controls
third-party risk management examples
nist risk framework
infosec risk management
compliance risk assessment framework
security risk management plan
tprm solutions
supplier risk management program
risk management standards
3rd party management
tprm lifecycle
third party assessment
nist vendor management
third party vendor monitoring
rmf cyber
managing third party risk
third party risk cyber security
third party security management
cybersecurity risk assessment framework
third party risk governance
third party vendor risk assessment example
nist risk management framework steps
third party management risk
third party governance
nist csf vs rmf
shared assessments sig
vendor risk management best practices
risk management security
nist risk matrix
nist risk management framework 800-53
rmf 7 steps
it risk assessment framework
tprm platforms
nist cybersecurity risk assessment
third party vendor definition
7 steps of risk management process
risk analysis framework
risk security management
third party risk assessment framework
3rd party security assessment
security risk management program
nist cybersecurity risk assessment template
regulatory risk management framework
third party compliance management
third-party cyber risk management
third party risk management examples
rmf process steps
third party risk definition
nist rmf 7 steps
third party risk management system
3rd party vendor risk assessment
third party risk assessment process
third party compliance risk management
what is third party management
tprm risk assessment
nist cyber risk scoring
what is third-party risk management
tprm compliance
risk assessment frameworks
third party operational risk
threat management framework
management frameworks
risk managment framework
technology risk management framework
third party vendor risks
how to mitigate third party risk
what is third party risk
third party risk management workflow
third-party vendor
risk management framework cybersecurity
third party risk management compliance
higher education tprm
third party vendor risk
nist risk management framework (rmf)
tprm cybersecurity
cyber risk frameworks
technology risk framework
risk management frameworks list
risk management and security
how to manage third party risk
tprm policy
third party risk management guide
3rd party monitoring
third-party vendor risk management
cyber security risk assessment framework
security risk management framework
third-party management
go/tprm
rmf lifecycle
third party risk management as a service
manage third party risk
rmf tools
nist management framework
digital risk management framework
nist rmf 800-53
what is nist rmf
third party risk management programs
supplier risk management framework
rmf security controls
cyber risk assessment framework
third party risk management standards
third-party risk management best practices
third party information security
health tprm
third party cyber security risk management
sig shared assessments
cyber security third party risk
nist csf risk assessment
risk mitigation framework
cyber rmf
managing third party vendors
third-party risk management program
rmf nist 800-53
why is third party risk management important
it vendor management framework
third party risk management definition
third-party vendor examples
third party risk management controls
third party risk manager
rmf security
robust risk management program
3rd party risk management framework
risk management guidelines
rmf requirements
cyber security risk framework
3rd party risk assessment process
3rd party cyber risk
nist grc
third party risk assessment methodology
third-party risk examples
third party exposure
nist risk
third party risk management framework nist
nist risk management process
risk management framework rmf
nist 800-53 rmf
third party supplier risk
3rd party security risk assessment
nist third party risk management framework
security & risk management
vendor risk assessment framework
information technology risk management framework
risk based cybersecurity framework
risk assessment nist
cybersecurity rmf
cybersecurity third party risk management
third party risk reporting
risk management and compliance framework
federal tprm
what is third party risk assessment
what is rmf?
third party information security risk management
nist risk management framework template
third party risk mitigation
third party security risk assessment
third party security risk
cyber security rmf
securities risk management
third party compliance risk
nist vendor risk management
effective third party risk management
rmf cyber security
third party security risk management
third-party risk management market
risk management framwork
third party evaluation
tprm security
risk control framework
nist methodology
what is 3rd party risk management
nist tprm
3rd party assessment
third-party cyber risk
enterprise vendor risk management program
nist rmf controls
third party risk policy
nist 800 framework
information security compliance framework
risk information management
third party risk management tprm
third-party risk management process
nist cybersecurity risk management framework
third party risk regulations
nist rmf certification
third party risk management framework pdf
tprm best practices
risk assessment cybersecurity framework
cybersecurity risk management frameworks
what is third party vendor
3rd party security
third party risk management policy example
third party procurement
third party risk management audit
third party risk statistics
nist 800 rmf
third party risk management process flow
risk and control framework
risk management nist
third party relationship management
isms risk management
3rd party risk assessments
third party governance and risk management
which of the following poses a higher risk to ensuring business continuity?
third party management policy
third party compliance program
third-party risk management lifecycle
nist model
nist steps
tprm life cycle
third-party vendor management
risk framework management
thirdparty risk management
the risk management framework
it risk framework
nist risk assessment process
third party risk assessment best practices
third party risk management cyber security
third party risk due diligence
third party risk managment
third party managers
nist risk management framework 800 53
third-party risk assessment framework
third party risk management ongoing monitoring
cyber risk management frameworks
third party vendor security
what is nist risk management framework
non profit tprm
nist rmf process
nist rmf training
third party risk management frameworks
nist 800-53 risk management framework
third party risk management program template
the nist risk management approach includes all but which of the following elements?
nist 800-53 risk assessment
nist 800-53 vendor management
nist controls framework
third-party risk management policy
nist risk scoring matrix
what is third party vendor management
third party performance management
nist 800-53 risk assessment template
third-party risk management process flow
third party service provider risk assessment
list of nist frameworks
nist risk assessment tool
third party vendor management security best practices
rmf 800-53
third party risk management policies and procedures
third-party risk assessment example
rmf it
third party management process
third party management framework
nist rfm
nist cyber risk management framework
state & local tprm
it risk management frameworks
risk assessment framework nist
computer risk management
nist cyber risk assessment
third party information security assessment
third party risk management framework template
nist framework controls
third-party compliance
third party risk management checklist
third party risk examples
risk assessment controls
what are some things that are generally included on a third party security assessment report
third party risk management financial services
third party risk framework
third party vendor management program
information security management framework
what are some things that are generally included on a third party security assessment report?
risk models and frameworks
information risk management framework
nist risk assessments
nist third-party risk management framework
guidance for managing third party risk
rmf support
third-party risks examples
nist risk management framework training
third party threats
vendor risk management process flow
tprm services
third party risk assurance
rmf step
rmf documentation
third-party vendor risk assessment example
nist framework risk assessment
third-party risk management regulations
it risk assessment frameworks
third party risk scoring
risk and controls framework
third-party management best practices
security risk frameworks
risk management framework
risk management framework
third party risk management
third party risk monitoring
risk management framework
risk management framework
third party risk management
third party risk management
it security risk management
rmf steps
third party risk
it security risk management
third party risk management
security risk management
cyber security and risk management
risk management framework
risk management framework
ssid meaning
risk management framework
nist assessment
what risks are involved in information management?
third party risk management
security risk management
cybersecurity risk management
nist controls
risk management framework
rmf steps
rmf steps
risk management
risk management frameworks
third party vendor management
risk management framework
nist 800-30
t&r frameworks
third party vendor
risk management framework
risk monitoring
risk management framework
third party risk management
vendor risk management
serlect risks
third party management
third party risk management
third party risk management
risk management framework
tprm
rmf steps
ssid meaning
it security risk management
risk governance framework
third party risk management
third party compliance
third-party risk management software
nist rmf steps
third party risk management
risk management framework
7 steps of risk management process with example
third party risk assessment
third party risk management
nist frameworks
third-party risk management software
risk management framework
risk management framework
third-party risk management
nist csf
risk management framework
risk management framework
defining customer satisfaction
risk management framework
third party security
third party access management
risk management framework
third-party risk management
risk management framework
risk control
vendor risk management framework
an example of a risk management strategy is…
third party cyber risk assessment
tprm framework
third party risk management
nist csf
third party threat
nist csf
third-party risk management
supplier risk management software
third party cyber risk management
risk & security management
security risk management
nist rmf vs csf
vendor risk assessment questionnaire
it security risk management
third party cyber risk
third-party risk management
third party risk management services
third party risk management
risk management framework
third-party risk management
nist csf
risk management framework
third-party risk management software
risk management frameworks
third party risk management
third party risk management
risk management framework
third party risk management
risk management framework
third party risk management
third party management
it security risk management
third party risk management
security risk model
safety risk assessment
third party risk management
risk management framework
third party vendor management
third-party risk management
it security risk management
it risk management
third party risk assessment
third party vendor management
risk management framework
risk management frameworks
vanta frameworks
importance of third party risk management
it security risk management
third-party risk management software
federal tprm
third party compliance
what does rmf stand for
compliance risk management framework
risk management framework
third party risk assessment
tprm meaning
it security risk management
information security risk assessments
risk management framework
risikomanagement
third-party risk management
risk management frameworks
third party vendor management
nist csf
third party cyber risk management
risk management framework
it security risk management
compliance risk assessment framework
cyber risk management
supplier risk management software
supplier risk management
risk management standards
third party management
tprm lifecycle
third party risk assessment
nist vendor risk management
third party vendor monitoring
risk management framework
fourth party vendor
third party cyber risk
third party cyber risk management
cyber security risk assessment
third-party risk management
third-party risk management examples
rmf steps
third party risk monitoring
third party governance
nist rmf vs csf
sig questionnaire
vendor risk management
risk management security
nist 800-30
nist controls
rmf steps
nist cybersecurity risk management framework
third-party risk management software
cyber security risk assessment
third party vendor definition
7 steps of risk management process with example
risk management frameworks
security risk management
third party risk management
3rd party security assessment
it security risk management
cyber risk assessment tools
risk management regulations
third party compliance
third party cyber risk management
third party risk management
rmf steps
third party cyber risk
nist rmf steps
third party risk management
third party risk assessment
third party risk assessment
third party risk management
third party management
third party risk management
nist score
what is tprm
tprm compliance
risk management frameworks
3rd party risk management
cyber threat management
strategy frameworks
risk management framework
risk management framework
vendor risk
tprm
third party cyber risk
third party risk management
ssid meaning
risk management framework
tprm
higher education tprm
third party cyber risk
risk management framework
tprm meaning
nist csf
it risk management
risk management frameworks
security risk management
third party risk management
tprm policy
third party risk management
third party vendor monitoring
third-party risk management
cybersecurity risk assessment
risk management framework
third party management
third-party risk management
risk management framework
third party risk management as a service
third-party risk management
open source risk management software
risk management framework
digital risk management
nist controls
risk management framework
third-party risk management
supplier risk management
risk management framework
cyber security risk assessment
third party oversight
third-party risk management
third party security
health tprm
third party cyber risk management
sig questionnaire
third party cyber risk
cybersecurity risk management
risk management framework
risk management framework
third party vendor management
third party risk monitoring
nist controls
importance of third party risk management
vendor management framework
third party risk management
third-party vendor
third party risk management
third party risk management
risk management framework
robust risk management program
third-party risk management
iso 31000
risk management framework
nist csf
third party risk assessment
third party threat
nist grc
third party risk assessment
third party vendor risk assessment example
third party risk
risk management framework
risk management framework
risk management framework
risk management framework
nist controls
vendor risk
third party risk assessment
risk management framework
security risk management
vendor risk management framework
risk management framework
risk-based approach
nist 800-30
risk management framework
third party cyber risk management
third party risk management
what is rmf
federal tprm
third party risk assessment
risk management framework
tprm meaning
nist 800-53 risk assessment template
tprm
third party security assessment
third party risks
risk management framework
security risk management
third-party risk management
risk management framework
third party risk management
risk management framework
third party risk management
third party risk management market
risk management framework
third party evaluation
third party cyber risk management
risk management framework
nist methodology
third party risk management
risk management framework
third party risk assessment
third party cyber risk
enterprise vendor risk management
nist controls
tprm policy
nist cybersecurity risk management framework
security compliance standards
what risks are involved in information management?
third party risk management
third-party risk management
risk management framework
third party risk management
rmf certification
third party risk management framework pdf
third party risk management
cyber security risk assessment
cybersecurity framework list
3pl
third party security
tprm policy
third party procurement
third party vendor risk management
third party risk statistics
risk management framework
third party risk management
risk managment framework
cyber security and risk management
3rd party banks
information security risk management
third party risk assessment
third party risk management
which of the following poses a higher risk to ensuring business continuity?
third party risk management policy
third party compliance
third party lifecycle management
nist csf
rmf steps
third party risk management lifecycle
third party vendor management
risk management framework
third party risk management
risk management framework
it risk management
risk assessment
third party risk assessment
third party cyber risk management
third party due diligence
tprm
third party management
nist controls
third-party risk management
third party risk management ongoing monitoring
cyber security framework
third party cyber risk
risk management framework
non profit tprm
risk management framework
rmf certification
tprm framework
risk management framework
third party risk management policy
the nist risk management approach includes all but which of the following elements?
nist 800-30 risk assessment example
nist third party risk management
nist csf
third-party risk management
nist score
third party vendor management
third party performance management
nist risk management framework template
third party risk management
third party risk assessment
nist frameworks
cybersecurity risk assessment template excel
3rd party risk management
nist controls
tprm policy
third party risk assessment
risk management framework
third party risk management
tprm framework
risk management framework
risk management framework
state & local tprm
it risk management framework
risk management framework
it risk assessment
information security risk assessments
third party risk assessment
third party risk management framework pdf
nist csf
third party compliance
third party risk management checklist
third party vendor risk assessment example
risk assessment process
what are some things that are generally included on a third party security assessment report
third party risk management regulations
tprm framework
3rd party vendor management
nist csf
what are some things that are generally included on a third party security assessment report
risk management frameworks
risk management framework
nist 800-30
risk management framework
third party risk management
rmf cybersecurity
third-party risk management examples
rmf certification
third party cyber risk
vendor management workflow
tprm services
third-party risk management
risk management framework
risk management framework
vendor risk assessment template
risk management framework
third party risk management regulations
it risk management framework
third party risk assessment
risk and controls framework
3rd party risk management
cyber security framework
We leverage Open source intelligence (OSINT) to use publicly available data to provide organisations with hyper-accurate and fully auditable insights with no false positives.
Improve analyst efficiencies, including cost and time reduction of minimum 25% with zero false positives.
The FCA recommends open source Internet checks as best practice (FG 18/5). Manage and reduce risk by incorporating 100% of online sources into your processes.
Manage risk with hyper accurate ongoing monitoring. We will monitor 100% of publicly available online data to help identify relevant risks.























The Neotas Platform covers 600Bn+ archived web pages, 1.8Bn+ court records, 198M+ corporate records, global social media platforms, and 40,000+ media sources from over 100 countries to help you build a comprehensive risk assessment of individuals, entities, and their networks.
Neotas Platform covers 600Bn+ archived web pages, 1.8Bn+ court records, 198M+ corporate records, global social media platforms, and 40,000+ Media sources from over 100 countries to help you build a comprehensive picture of the team.
| Cookie | Duration | Description |
|---|---|---|
| AWSALBTG | 7 days | AWS Application Load Balancer Cookie. Load Balancing Cookie: Used to encode information about the selected target group. |
| AWSALBTGCORS | 7 days | AWS Classic Load Balancer Cookie: Used to map the session to the instance. This cookie is identical to the original ELB cookie except for the attribute &SameSite=None; |
| cookielawinfo-checkbox-advertisement | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Advertisement" category . |
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| CookieLawInfoConsent | 1 year | Records the default button state of the corresponding category & the status of CCPA. It works only in coordination with the primary cookie. |
| debug | never | Cookie used to debug code and website issues |
| shown | session | Session cookie to control number of times a pop up is shown. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| __cf_bm | 30 minutes | This cookie, set by Cloudflare, is used to support Cloudflare Bot Management. |
| AnalyticsSyncHistory | 1 month | Used to store information about the time a sync took place with the lms_analytics cookie |
| bcookie | 2 years | LinkedIn sets this cookie from LinkedIn share buttons and ad tags to recognize browser ID. |
| bscookie | 2 years | LinkedIn sets this cookie to store performed actions on the website. |
| lang | session | LinkedIn sets this cookie to remember a user's language setting. |
| lidc | 1 day | LinkedIn sets the lidc cookie to facilitate data center selection. |
| UserMatchHistory | 1 month | LinkedIn sets this cookie for LinkedIn Ads ID syncing. |
| Cookie | Duration | Description |
|---|---|---|
| li_gc | 2 years | Used to store consent of guests regarding the use of cookies for non-essential purposes |
| rl_anonymous_id | 1 year | Generates an unique anonymous Id to identify a user and attach to a subsequent event. |
| rl_user_id | 1 year | to store a unique user ID for the purpose of Marketing/Tracking |
| Cookie | Duration | Description |
|---|---|---|
| _ga | 2 years | The _ga cookie, installed by Google Analytics, calculates visitor, session and campaign data and also keeps track of site usage for the site's analytics report. The cookie stores information anonymously and assigns a randomly generated number to recognize unique visitors. |
| _gat_gtag_UA_107495977_1 | 1 minute | Set by Google to distinguish users. |
| _gat_UA-107495977-1 | 1 minute | A variation of the _gat cookie set by Google Analytics and Google Tag Manager to allow website owners to track visitor behaviour and measure site performance. The pattern element in the name contains the unique identity number of the account or website it relates to. |
| _gcl_au | 3 months | Provided by Google Tag Manager to experiment advertisement efficiency of websites using their services. |
| _gid | 1 day | Installed by Google Analytics, _gid cookie stores information on how visitors use a website, while also creating an analytics report of the website's performance. Some of the data that are collected include the number of visitors, their source, and the pages they visit anonymously. |
| attribution_user_id | 1 year | This cookie is set by Typeform for usage statistics and is used in context with the website's pop-up questionnaires and messengering. |
| CONSENT | 2 years | YouTube sets this cookie via embedded youtube-videos and registers anonymous statistical data. |
| Cookie | Duration | Description |
|---|---|---|
| _fbp | 3 months | This cookie is set by Facebook to display advertisements when either on Facebook or on a digital platform powered by Facebook advertising, after visiting the website. |
| fr | 3 months | Facebook sets this cookie to show relevant advertisements to users by tracking user behaviour across the web, on sites that have Facebook pixel or Facebook social plugin. |
| IDE | 1 year 24 days | Google DoubleClick IDE cookies are used to store information about how the user uses the website to present them with relevant ads and according to the user profile. |
| test_cookie | 15 minutes | The test_cookie is set by doubleclick.net and is used to determine if the user's browser supports cookies. |
| VISITOR_INFO1_LIVE | 5 months 27 days | A cookie set by YouTube to measure bandwidth that determines whether the user gets the new or old player interface. |
| YSC | session | YSC cookie is set by Youtube and is used to track the views of embedded videos on Youtube pages. |
| yt-remote-connected-devices | never | YouTube sets this cookie to store the video preferences of the user using embedded YouTube video. |
| yt-remote-device-id | never | YouTube sets this cookie to store the video preferences of the user using embedded YouTube video. |
| yt.innertube::nextId | never | This cookie, set by YouTube, registers a unique ID to store data on what videos from YouTube the user has seen. |
| yt.innertube::requests | never | This cookie, set by YouTube, registers a unique ID to store data on what videos from YouTube the user has seen. |