Risk Management Framework

A practical playbook for governance, compliance, and strategic resilience. Board-Ready Risk Intelligence Playbook: 30-Day Path from Framework to ROI. This article will help you reduce blind-spots, cut decision-latency, and unlock risk-adjusted growth.
TPRM Methodology – Comprehensive Guide to Third-Party Risk Management (TPRM)

TPRM methodology, including risk assessment, mitigation strategies, best practices for effective Third-Party Risk Management program implementation in 2025.
Financial Crime Compliance Framework

Financial Crime Compliance Framework – The global framework for fighting financial crime. Anti-Money Laundering and Financial Crime Compliance Solutions
Financial Crime Compliance & Risk Management – Guide to countering financial crime risks

Financial Crime Compliance & Risk Management – Guide to countering financial crime risks. AML Strategies and FCC Framework to Counter financial crime risks.
Risk Intelligence: Strategic Risk Intelligence Software and Advisory Services

What is Risk Intelligence? Strategic Risk Intelligence solutions, risk management framework, and risk intelligence software to manage business risk.
Third-Party Risk Management (TPRM) Lifecycle: Key Stages & Best Practices

Third-Party Risk Management (TPRM) Lifecycle In today’s interconnected business environment, organisations increasingly rely on third-party vendors, suppliers, and service providers to support their operations, drive efficiencies, and deliver specialised expertise. However, while outsourcing and partnerships can foster growth and competitive advantage, they also introduce significant risks. Data breaches, regulatory non-compliance, operational disruptions, and reputational damage […]
Anti-Money Laundering Regulations, AML Checks and Compliance

Anti-Money Laundering Regulations – AML Law, AML Checks, and AML Compliance in 2024
AML transaction monitoring – Regulatory Requirements and Best Practices

Anti-Money Laundering (AML) transaction monitoring involves continuous review of financial transactions conducted by customers to identify suspicious activities
AML Compliance Checklist for Banks: Best Practices for Anti-Money Laundering

AML Compliance Checklist for Banks
AML Compliance Requirements, AML Regulations and Best Practices for Anti-Money Laundering
AML Compliance Checklist: Best Practices for Anti-Money Laundering

AML Compliance Checklist AML Compliance Requirements, AML Regulations and Best Practices for Anti-Money Laundering Anti-Money Laundering (AML) compliance is essential for preventing illicit funds from infiltrating the legitimate financial system. Regulated entities, such as banks, financial institutions, and money service businesses, must implement effective AML programs to detect, prevent, and report money laundering activities. This […]
AML Checks – Anti-Money Laundering regulations for identity assessment and verification process

AML Checks – Anti-Money Laundering regulations for identity assessment and verification process. AML and KYC Checks, Anti Money Laundering Compliance Solutions
Money Laundering Reporting Officer (MLRO) – Meaning, Roles, Responsibilities, and Expert Insights

MLRO Meaning: Who is a Money Laundering Reporting Officer? Roles and Responsibilities of an MLRO in Combating Financial Crime, compliance, & AML regulations.
What is Customer Due Diligence in Banking and Financial Services?

Customer Due Diligence in Banking and Financial Services – Risk management, Compliance, and Anti-Money Laundering (AML) regulation.
OSINT Investigation process and Open Source Investigation Best Practices

Open Source Investigation Best Practices Your ultimate guide to OSINT investigations! Learn techniques, tools, and best practices for gathering actionable intelligence ethically and effectively. In the digital era, Open Source Intelligence (OSINT) has become an indispensable tool across sectors like cybersecurity, law enforcement, corporate security, journalism, and competitive intelligence. With vast amounts of information freely […]
OSINT Sources – Using Archives for OSINT Investigations

Using Archives for OSINT Investigations Open Source Intelligence (OSINT) is a critical component of modern intelligence gathering, relying on publicly available information to develop actionable insights. As digital information continues to proliferate, the use of archives in OSINT investigations has become increasingly important. Archives, whether digital or physical, provide a rich repository of historical data […]
OSINT Sources – Using Dark Web for OSINT Investigations

Using Dark Web for OSINT Investigations – OSINT Sources, OSINT Tools, and OSINT Techniques | Best Practices for dark web investigations in 2024
OSINT Sources – Using Geolocation for OSINT Investigations

OSINT Sources – Using Geolocation for OSINT Investigations – Learn about Geolocation OSINT, Geolocation Intelligence tools, and OSINT Investigation Techniques
OSINT Sources – Using Social Media for OSINT Investigations

OSINT Sources – Using Social Media for OSINT Investigations – Learn about Social Media OSINT, Social Media Intelligence tools, and OSINT Investigation Techniques
What is the OSINT Framework? – A Complete Guide to the OSINT Framework, Essential Tools, and Best Techniques
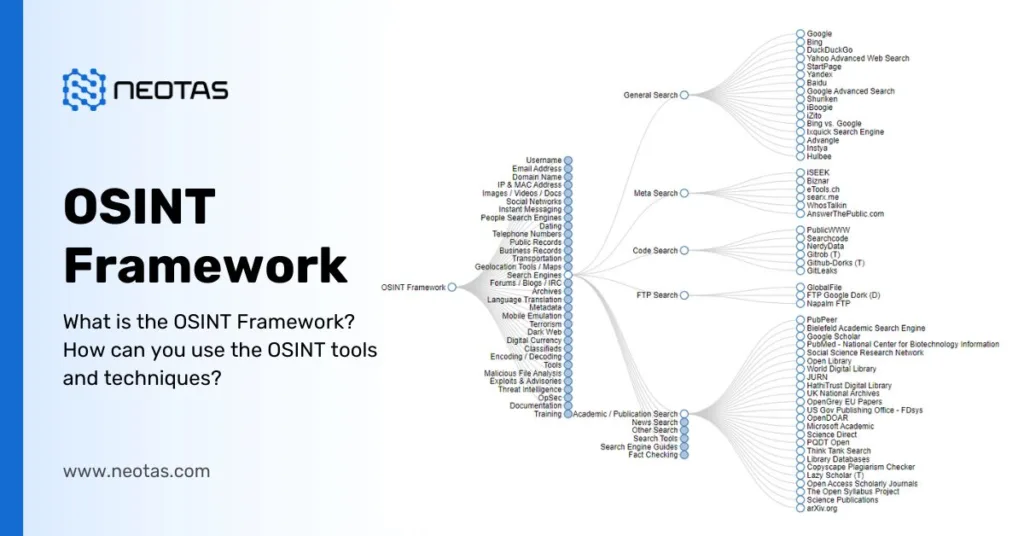
What is the OSINT Framework? – A Complete Guide to the OSINT Framework, Essential Tools, and Best Techniques in 2025 | Neotas UK
Third-Party Risk Management – Third-Party Risk Assessment Framework, TPRM Best practices, and Third-Party Due Diligence

Third-Party Risk Management (TPRM) Guide 2024 – TPRM Framework, TPRM Best practices, Third-Party Risk Assessment, and Third-Party Due Diligence | Neotas UK
Supply Chain Risk Management (SCRM) – Assess and Mitigate Supplier Risk

Supply chain risk management (SCRM) is the process of finding & addressing potential risks in a company’s supply chain. Assess & Mitigate Supplier Risk in 2024
Vendor Due Diligence Checklist – Identify Third Party Risks and Secure Vendor Relationships

Vendor Due Diligence Checklist – Identify Third Party Risks and Secure Supplier Relationships with Vendor Due Diligence (VDD) checklist template.
Risk-based approach (RBA) – effective procedures to determine and manage AML & KYC risk in 2024

A risk-based approach to AML ensures effective procedures to mitigate and reduce AML & KYC risks. Managing AML and KYC risk in 2025
Regulatory Compliance in Digital Screening: International view of the emerging Challenges and Opportunities

Regulatory Compliance in Digital Screening An International view of the emerging Challenges and Opportunities for Digital Screening The bulk of global statutory instruments and regulatory controls concerning general data security and the protection of personal data are outdated and inadequate. These controls can only change using prescribed processes. This ability to change, respond, and maintain […]
Money Laundering Advisory Notice: High Risk Third Countries
Money Laundering Advisory Notice: High Risk Third Countries Recent regulatory changes by HM Government have brought about new challenges for banks, payment providers, andfinancial institutions dealing with high-risk third countries. Neotas launches automated solution to deal with KYC backlogs due to changes in high-risk countries list. Improve AML efficiency with automated CDD and EDD for […]
Anti-Money Laundering (AML) – The 5 pillars of AML Compliance

Anti-Money Laundering (AML) Anti-Money Laundering (AML) is a comprehensive framework of policies, regulations, and procedures established to prevent individuals and entities from disguising illegally obtained funds as legitimate income within the financial system. Its primary purpose is to detect and deter financial crimes by tracing and halting the flow of funds originating from illicit activities. […]
Customer Due Diligence Requirements

What is Customer Due Diligence? Explore the Customer Due Diligence Requirements, CDD Process, CDD Checklist, CDD for Banks and CDD requirements for AML and KYC.
What is Simplified Due Diligence? – Due Diligence for Low-risk customers

🤝 What is Simplified Due Diligence: understand SDD vs CDD vs EDD, who needs SDD, checklist, & the steps involved in Simplified Due Diligence process. Neotas UK.
Due Diligence – Types, Process, Requirements and Checklist

What Is Due Diligence? – definition, types, checklist, process, and report examples. The importance of due diligence in business risk mitigation | Neotas UK
OSINT Framework – Key Components of OSINT Framework and How to use it?

OSINT Framework A comprehensive guide to OSINT framework, OSINT Tools, OSINT Techniques, and how to use it. The OSINT Framework is a comprehensive collection of open source intelligence (OSINT) tools and resources that are organised and categorised for easy access. It’s designed to assist researchers, investigators, cybersecurity professionals, journalists, and anyone else interested in gathering […]
Investment Due Diligence Checklist – 15 Investor Due Diligence Steps

Investment Due Diligence Checklist How to Conduct Investment Due Diligence and Ensure Informed and Sound Investment Decisions Investment Due Diligence is a comprehensive process undertaken by investors before committing to a financial transaction. It involves a thorough examination of all relevant aspects of the investment, aiming to confirm the accuracy of information provided, assess potential […]
What is Third-Party Risk Management (TPRM)?

What is Third-Party Risk Management? All you need to get started with TPRM in UK. Understand TPRM framework, TPRM best practices, TPRM tools, TPRM processes.
What is Customer Due Diligence? Customer Due Diligence Meaning, how it works, types of CDD

What is Customer Due Diligence? Understanding the Significance of Customer Due Diligence in Business Compliance Customer Due Diligence (CDD) is a critical process in the realm of business, particularly in the financial sector. It serves as a cornerstone for maintaining regulatory compliance, safeguarding against financial crimes, and establishing trust between businesses and their customers. This […]
Customer Due Diligence Checklist – What is Customer Due Diligence? – The Process and Requirements

Customer Due Diligence Checklist Understanding the Significance of Customer Due Diligence in Business Compliance – What is Customer Due Diligence? – The Customer Due Diligence Requirements Customer Due Diligence Meaning: Customer Due Diligence (CDD) is a critical process in the realm of business, particularly in the financial sector. It serves as a cornerstone for maintaining […]
Enhanced Due Diligence Checklist – EDD checklist for High-Risk Customers

Enhanced Due Diligence Checklist – Best practices & step by step guide for KYC, AML, fraud prevention & more. EDD checklist for High-Risk Customers | Neotas UK
The Perils of AI-Based Social Media Checks Without Human Intervention

AI-Based Social Media Checks Without Human Intervention AI Social Media Checks As artificial intelligence (AI) continues to advance, its integration into various aspects of our lives becomes increasingly apparent. One area that has created considerable interest is the use of AI-based social media checks. While these AI based systems may promise enhanced security, efficiency, and […]
What is ESG Due Diligence? – A Definitive Guide

Environmental, Social and Governance (ESG) Due Diligence A Definitive Guide to ESG Due Diligence for your Organisation In today’s rapidly evolving business landscape, environmental, social, and governance (ESG) considerations have emerged as critical factors in investment decision-making. ESG Due Diligence, an integral component of this paradigm shift, plays a pivotal role in assessing a company’s […]
Social Media checks and background screening for Teachers and school staff

Social Media checks for Teachers, Social Media Checks for School Staff and Social Media Background Screening Checks in UK – Social Media Screening Guide 2025
How GDPR and FCRA Apply to Social Media Background Checks – The Do’s and Don’ts of Social Media Background Checks for Employers

Social Media Background Checks The widespread use of social media has led to an increasing trend among employers to conduct social media checks as part of their recruitment process. However, employers must be aware of the GDPR and FCRA implications of such checks, which set out strict rules for the processing of personal data, including […]
Social Media Check – What you need to know and it’s impact on your business

Social Media Check The demand for the generation of high-quality, scalable, and affordable candidate social media check reports has grown exponentially in organisations performing pre-employment screening checks before hiring for a position. The Neotas Employee Screening Platforms have been developed to provide social media screening capabilities for its global clients and channel partners to effectively […]
Social Media checks for Lawyers and other legal professionals

Social Media checks for Lawyers and other legal professionals In recent years, social media has become a ubiquitous part of our lives, with millions of people using it every day to share their thoughts, opinions, and experiences with others. Social media has also become an increasingly important tool for businesses and organizations to promote themselves […]
Social media checks for doctors and healthcare specialists

Social media checks for doctors and healthcare specialists In the modern age, social media has become an integral part of our daily lives, extending its influence into professional realms. This article explores the significance of implementing social media checks for doctors and healthcare specialists. Social media checks contribute to maintaining professionalism, upholding ethical standards, staying […]
Importance of using Social Media checks for Police Officers

Social Media checks for Police Officers This article covers the importance of social media checks for police officers, ensuring public safety, preventing misconduct, and building trust. By promoting transparency and professionalism, social media checks foster a stronger relationship between law enforcement and the community they serve. Introduction: The demand for social media checks for police […]
What is Corporate Intelligence and how can it Help Businesses Manage Risk

What is corporate intelligence and how corporate intelligence services helps businesses manage risks. Discover Corporate intelligence companies in London, UK
Overcoming Enhanced Due Diligence Challenges on High Risk Customers

Enhanced Due Diligence for High Risk Customers By Michael Harris MCMI, Head of Financial Crime Risk, Neotas There is growing concern that disinformation and so-called “reputation laundering” campaigns could be used by high-risk customers to illegitimately pass enhanced due diligence checks. Additionally, such campaigns could undermine the introduction of sanctions on high-risk individuals, as well […]
How OSINT Can Help Challenger Banks Create More Robust AML Controls

OSINT for AML Compliance FCA Warns Challenger Banks Over AML Compliance Shortcomings In the latest reproach from the FCA to anti-money-laundering regulated firms across the financial services industry, Challenger Banks were criticised for failing to implement robust AML controls in line with money-laundering regulations. This is hot on the heels of a similar reprimand in […]
Environmental, social and governance (ESG) and The Power Of Open-Source Intelligence (OSINT)

ESG and The Power Of Open-Source Intelligence (OSINT) “We frequently seek opportunities to enhance ESG within our investment processes. We felt that OSINT-based analysis was the natural next step for our ESG programme.” – Coller Capital Neotas Partners With Coller Capital Neotas are delighted to be chosen service providers of Coller Capital, to provide enhanced […]
Suisse Secrets Leaks Exposes EDD Shortcomings

Suisse Secrets Leaks Exposes EDD Shortcomings : It is a sign of the times when the largest political grouping in Europe threatens to designate Switzerland a high-risk jurisdiction for financial trading. A spokesperson for the European People’s Party said information in this week’s data leak (nicknamed the ‘Suisse Secrets’) showed “massive shortcomings of Swiss banks […]
Neotas Due Diligence 2021 Annual Report

Neotas Due Diligence 2021 Annual Report : Risks hidden in plain sight “2021 was another unprecedented year for Neotas. In spite of the circumstances, we enjoyed our most productive year to date and I couldn’t be prouder of the way our team overcame the challenges we faced together. “ – Ian Howard, Director We are […]
Neotas Employment Screening 2021 Annual Report

Neotas Employment Screening 2021 Annual Report Reflections on 2021 “Employers in 2021 were forced to adapt and overcome a host of challenges that were multiplied due to the pandemic. In an increasingly ‘connected’ world, adopting new technologies and techniques like our social media screening services proved vital, leading to actual improvements in hiring decisions.” Ian Howard, […]













